
Getty Pictures Researchers nonetheless have no idea the reason for the just lately came upon malware an infection that has affected just about 1.3 million units with an open-source model of Android in just about 200 nations. Safety company Physician Internet mentioned Thursday {that a} malware referred to as Android.Vo1d has inflamed Android containers. through striking malicious content material on their machine’s garage, the place it may be changed with further malware at any time through command-and-control servers. Google representatives say the inflamed units use an working machine in response to the Android Open Supply Mission, a model overseen through Google however become independent from Android TV, a model simplest to be had to proprietary builders who’ve licenses. Many varieties Even though Physician Internet has a just right working out of Vo1d and the original succeed in it has completed, business researchers say they nonetheless have no idea what brought about the illness. “Recently, the supply of the illness at the back of the TV is unknown,” it mentioned on Thursday. “One imaginable vector for the virus may well be an assault through a middleware malware that exploits an working machine vulnerability to achieve get right of entry to. Any other possible downside may well be using unauthorized firmware variations with everlasting root get right of entry to.” The next software varieties suffering from Vo1d are: TV field fashion Declared firmware model R4 Android 7.1.2; TV BOX Construct/NHG47K Android 10.1; As an example, variations 7.1, 10.1, and 12.1 had been launched in 2016, 2019, and 2022 respectively. Moreover, Physician Internet mentioned that it’s not bizarre for funds builders to incorporate older variations of the OS in promotional containers. As well as, even though simplest authorized software producers are allowed to change Google’s AndroidTV, any software producer has the best to change the open supply variations. This opens up the likelihood that the software was once inflamed and was once already corrupted on the time it was once bought through the person. “Those non-branded units that had been discovered to be inflamed weren’t approved Play Offer protection to units for Android,” Google mentioned in a commentary. “If a tool isn’t qualified through Play Offer protection to, Google has no safety historical past and check effects. Android units licensed through Play Offer protection to are broadly examined to verify the security of customers. The commentary says that folks can ascertain that the software is operating Android TV OS through checking this hyperlink and following the directions. is written right here. Physician Internet mentioned that there are lots of forms of Vo1d that use other code and plant malware within the garage, however all of them get the similar results of connecting to the server managed through the attacker and putting in the closing section that may set up the extra malware. VirusTotal displays that Lots of the Vo1d variants had been first uploaded to the malware identity web site a couple of months in the past. The researchers wrote: A majority of these instances had identical signs, so we can describe them the use of probably the most first requests we won for example. The next pieces had been modified at the affected TV field: install-recovery.sh daemnsu As well as, 4 new recordsdata seemed in its recordsdata: /machine/xbin/vo1d/machine/xbin/wd/machine/bin/debuggerd/machine/ bin/ debuggerd_real The vo1d and wd recordsdata are elements of the Android.Vo1d trojan we came upon. The authors of the trojan can have attempted to hide certainly one of its elements because the machine /machine/bin/vold, naming it with the identical title “vo1d” (substituting the lowercase letter “l” and the quantity “1”). The title of this malware comes from the title of this report. Additionally, this spelling corresponds to the English phrase “void”. The install-recovery.sh report is a script discovered on maximum Android units. It’s lively when it’s put in and accommodates information to control the items outlined in it. If any malware has root and will write to the /machine listing, it could actually set up itself within the inflamed software through including itself to the listing (or through growing it from the show if it’s not discovered within the machine). Android.Vo1d registers the autostart of the wd module on this report.
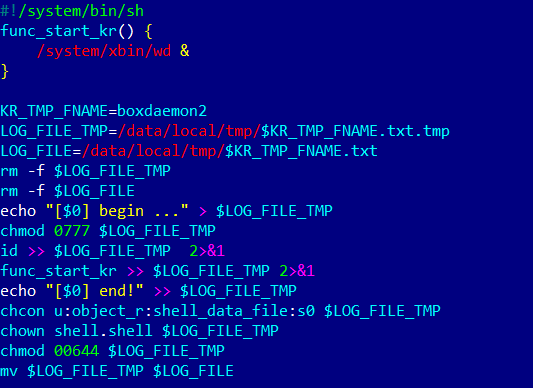 Changed report install-recovery.shDoctor Internet The daemonsu report is to be had on maximum rooted Android units. It’s began through the working machine when the appliance begins and is accountable for granting get right of entry to to the person. Android.Vo1d is registered on this report, too, after resetting autostart for the wd module. A daemon-edited report this is used to generate experiences on occasions. But if the TV field was once inflamed, this report was once changed through a script that begins the wd part. The debuggerd_real report within the article we’re discussing is a replica of the script that was once used as an alternative of the particular debugger report. Internet Physician professionals consider that the authors of the trojan sought after the debugger to be moved into debuggerd_real to proceed operating. On the other hand, since the an infection can have befell two times, the trojan moved the prior to now loaded report (ie, the script). Because of this, the software contained two recordsdata from the trojan and no longer one precise report was once broken. On the similar time, some customers who contacted us had a distinct record of recordsdata on their inflamed units: daemonsu (analogue of vo1d – Android.Vo1d.1); wd (Android.Vo1d.3); debugged (similar textual content as described above); debuggerd_real (unique debugger report); install-recovery.sh (the script that a lot the pieces laid out in it). The research of the entire aforementioned recordsdata confirmed that so as to set up Android.Vo1d within the machine, its authors used no less than 3 strategies: the amendment of the install-recovery.sh and daemonsu recordsdata and the set up of the broken program. They must be expecting that the recordsdata they’re focused on will likely be provide within the inflamed machine, as a result of controlling even certainly one of them will reason the trojan to start out operating effectively all through reboot. The principle serve as of Android.Vo1d is hidden in its vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3) elements, which paintings respectively. The Android.Vo1d.1 module is accountable for beginning Android.Vo1d.3 and operating its procedure, restarting its procedure if essential. Moreover, it could actually obtain and run simulations when suggested to take action through the C&C server. In flip, the Android.Vo1d.3 module installs and begins the Android.Vo1d.5 daemon this is encrypted and saved in its personal frame. This module too can obtain and run occasions. As well as, it displays decided on hyperlinks and installs the APK recordsdata they get right of entry to. The unfold of the illness is popular, and the absolute best numbers had been present in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
Changed report install-recovery.shDoctor Internet The daemonsu report is to be had on maximum rooted Android units. It’s began through the working machine when the appliance begins and is accountable for granting get right of entry to to the person. Android.Vo1d is registered on this report, too, after resetting autostart for the wd module. A daemon-edited report this is used to generate experiences on occasions. But if the TV field was once inflamed, this report was once changed through a script that begins the wd part. The debuggerd_real report within the article we’re discussing is a replica of the script that was once used as an alternative of the particular debugger report. Internet Physician professionals consider that the authors of the trojan sought after the debugger to be moved into debuggerd_real to proceed operating. On the other hand, since the an infection can have befell two times, the trojan moved the prior to now loaded report (ie, the script). Because of this, the software contained two recordsdata from the trojan and no longer one precise report was once broken. On the similar time, some customers who contacted us had a distinct record of recordsdata on their inflamed units: daemonsu (analogue of vo1d – Android.Vo1d.1); wd (Android.Vo1d.3); debugged (similar textual content as described above); debuggerd_real (unique debugger report); install-recovery.sh (the script that a lot the pieces laid out in it). The research of the entire aforementioned recordsdata confirmed that so as to set up Android.Vo1d within the machine, its authors used no less than 3 strategies: the amendment of the install-recovery.sh and daemonsu recordsdata and the set up of the broken program. They must be expecting that the recordsdata they’re focused on will likely be provide within the inflamed machine, as a result of controlling even certainly one of them will reason the trojan to start out operating effectively all through reboot. The principle serve as of Android.Vo1d is hidden in its vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3) elements, which paintings respectively. The Android.Vo1d.1 module is accountable for beginning Android.Vo1d.3 and operating its procedure, restarting its procedure if essential. Moreover, it could actually obtain and run simulations when suggested to take action through the C&C server. In flip, the Android.Vo1d.3 module installs and begins the Android.Vo1d.5 daemon this is encrypted and saved in its personal frame. This module too can obtain and run occasions. As well as, it displays decided on hyperlinks and installs the APK recordsdata they get right of entry to. The unfold of the illness is popular, and the absolute best numbers had been present in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
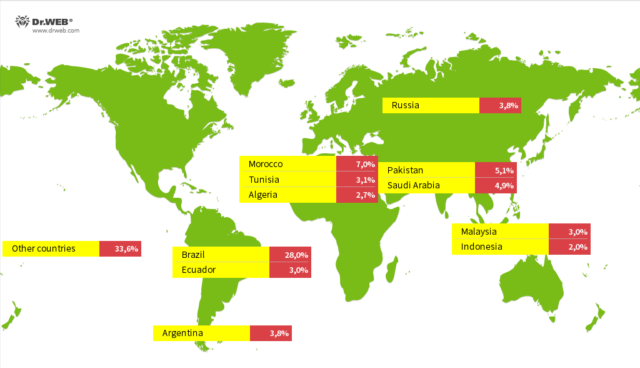 Increase / Global map appearing the choice of infections in numerous nations.Physician Web page It is not simple particularly for individuals who have no idea a lot about it to peer if the software is inflamed with out putting in a malware scanner. Physician Internet mentioned its Android antivirus device will discover all Vo1d variants and antivirus equipment that offer root get right of entry to. Skilled customers can test for indicators of incompatibility right here.
Increase / Global map appearing the choice of infections in numerous nations.Physician Web page It is not simple particularly for individuals who have no idea a lot about it to peer if the software is inflamed with out putting in a malware scanner. Physician Internet mentioned its Android antivirus device will discover all Vo1d variants and antivirus equipment that offer root get right of entry to. Skilled customers can test for indicators of incompatibility right here.












