What’s the oldest manner within the guide to get other people to do issues they wouldn't another way do? Fake to be any individual you aren’t. That is what the Antidot banking trojan is doing. With a view to draw in Android customers to obtain it, it sounds as if as an replace app for Google Play. Even supposing it is strongly recommended to stay your telephone and apps up-to-the-minute, you must watch out when downloading the replace and now not fall for a false caution. , which might come from cybercriminals like the ones in the back of Antidot. Safety researchers at Cyble (by means of Tom's Information) first encountered Antidot on Might 6. This is a banking trojan, designed to achieve get entry to on your monetary accounts to scouse borrow cash. .When you obtain the Google Play Replace App, a pretend web page with a “Proceed” button is displayed at the display. This website will use German, French, Spanish, Russian, Portuguese, Romanian, or English, relying on the place you are living. Like many different banking trojans, Antidot depends on the Accessibility function to do what it needs. As soon as the permissions are granted, an ID is created in your instrument.
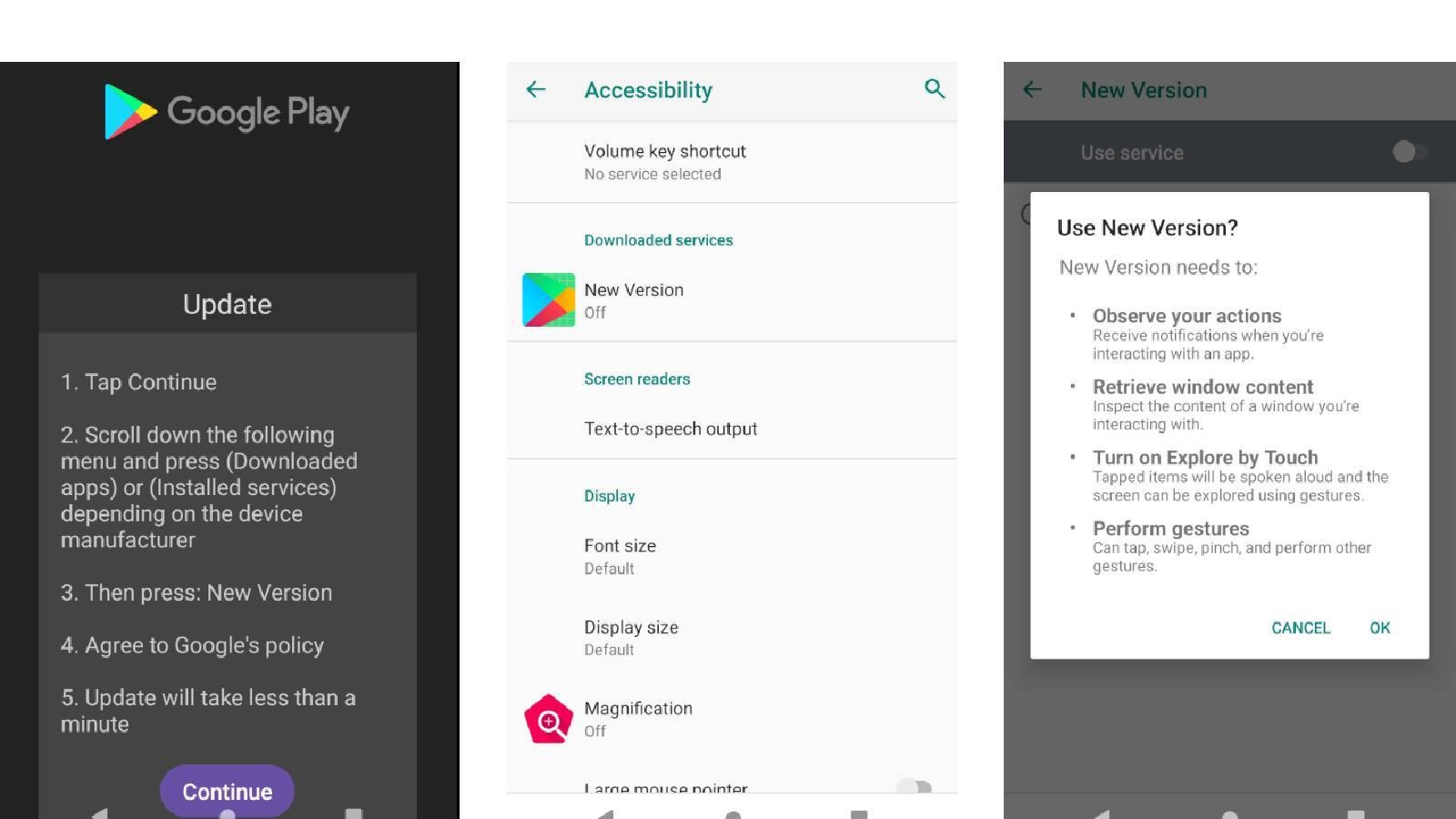

A pretend Google Play app forces you to grant get entry to permissions with a view to do malicious issues. The instrument additionally establishes a reference to the Command and Keep watch over (C&C) server and maintains a real-time reference to it to accomplish its purposes. overlay assault – deleting your profile. This can be utilized to get entry to your checking account or cryptocurrency programs. It might additionally carry out keylogging, display seize, ship calls, reproduction contacts, learn your SMS, lock and unencumber your instrument, and ship USSD requests (fast codes) In brief, this malware can regulate the whole thing in your Android instrument and that makes it the harmful factor is that it’s excellent at hiding its presence. So you’ll be ingesting espresso on your mattress, whilst this disgusting piece of instrument is silently sending your hard earned cash to its masters or studying articles that nobody must learn.
To steer clear of being stuck by means of such threats, obtain instrument most effective from relied on assets, even if this on my own isn’t sufficient to offer protection to you. You must additionally watch out when opening hyperlinks despatched to you which are unknown or untrustworthy and watch out for granting pointless permissions to systems.