Getty Pictures Probably the most not unusual makes use of of the community is the vulnerability of newly came upon assaults that may permit attackers to keep watch over quite a lot of domain names, together with commercial operators, telecommunications, ISPs, and a wide variety of companies. Quick for Far flung Authentication Dial-In Person Provider, RADIUS harkens again to the times of Web dial-up and community get entry to by means of public switched phone networks. It has remained the definitive light-weight same old ever since and is supported via just about all switches, routers, get entry to issues, and VPN concentrators which have been shipped over the last twenty years. In spite of its early origins, RADIUS continues to be a key component in managing buyer interactions for: VPN get entry to DSL and Fiber to the House connections supplied via ISPs, Wi-Fi and 802.1X authentication for 2G and 3G roaming 5G Information Community Title obtain Authentication for personal APNs to glue cellular units to trade networks Authentication of key instrument control equipment Eduroam and OpenRoaming Wi-Fi RADIUS supplies seamless conversation between purchasers—normally routers, switches, or different units that offer community get entry to—and a central server RADIUS, which acts as a gatekeeper for consumer authentication and get entry to. The aim of RADIUS is to offer centralized authentication, authorization, and accounting control for far off get entry to. This plan used to be evolved in 1991 via an organization referred to as Livingston Enterprises. In 1997 the Web Engineering Activity Pressure made it an reputable same old, which used to be revised 3 years later. Even if there’s a proposal to ship RADIUS visitors inside a TLS-encrypted box this is supported via some distributors, maximum units the use of the protocol most effective ship transparent packets by means of UDP (Person Datagram Protocol).
 XKCD photographs
XKCD photographs
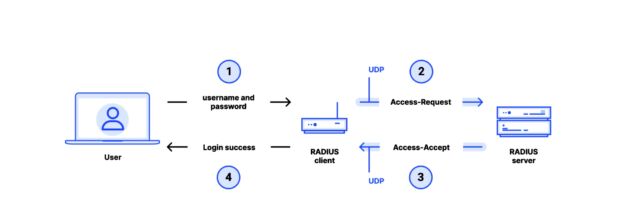 Make bigger / Detailed diagram of RADIUS the use of Password Authentication Protocol over UDP.Goldberg et al. Give your affirmation with MD5? In reality? Since 1994, RADIUS has depended on the usage of an effective, local MD5 hash. First evolved in 1991 and authorized via the IETF in 1992, MD5 used to be on the time a not unusual apply for growing what are referred to as “message digests” that encode arbitrary textual content corresponding to numbers, textual content, or binary information to a set period. 16-byte output. For a cryptographic hash serve as, it must be unattainable for an attacker to search out two inputs that fit the similar output. Sadly, MD5 used to be in keeping with a susceptible design: In a couple of years, there have been indicators that the operation may well be extra unhealthy than it used to be concept at the start of the collision that brought about the assaults, a deadly error that allowed the attacker to create two other units that produce. equivalent effects. Those suspicions had been formally showed in a paper revealed in 2004 via researchers Xiaoyun Wang and Hongbo Yu and had been revised in a analysis paper revealed 3 years later. The remaining paper – revealed in 2007 via researchers Marc Stevens, Arjen Lenstra, and Benne de Weger – described what’s referred to as an preliminary collision, a kind of collision that effects from two messages decided on via the attacker, when blended with two further ones. messages, create the similar hash. This is, the adversary freely chooses two other prefixes 𝑃 and 𝑃′ of gibberish that, when blended with the corresponding gibberish-like phrases 𝑆 and 𝑆′, shape the similar hash. Mathematically, the sort of selected preliminary collision may also be written as 𝐻(𝑃‖𝑆)=𝐻(𝑃′‖𝑆′). This sort of assault may be very tough as it provides the attacker the liberty to create extremely custom designed simulations. To reveal the character and damaging results of the assault, Stevens, Lenstra, and de Weger used it to create two cryptographic X.509 certificate that produced the similar MD5 signature however other workforce keys and other portions of the Outstanding Title. Such collisions could cause a certificates authority that desires to signal a certificates for one area to inadvertently signal a certificates for any other, malicious area. In 2008, a gaggle of researchers that incorporated Stevens, Lenstra, and de Weger confirmed how the primary selected phrase on MD5 allowed them to create a malicious certificates that might create a TLS certificates that may be depended on via all primary browsers. The important thing to the assault is device referred to as hashclash, evolved via researchers. Hashclash has been publicly to be had. In spite of the unknown finish of MD5, this serve as has been extensively used for a few years. The decline of MD5 didn’t start in earnest till 2012 after a malware referred to as Flame, allegedly evolved in collaboration with the Israeli and US governments, used to be discovered to have used a key phrase to compromise MD5-based code signing via the Microsoft Home windows replace mechanism. . Flame used collision-enhanced spoofing to thieve the transfer in order that the malware may just unfold from instrument to instrument throughout the inflamed community. 12 years after the Flame assault used to be came upon and two decades after the collision chance used to be showed, MD5 has dropped any other extensively used generation that has defied typical knowledge to transport clear of the RADIUS hashing-protocol device, which is supported via units or units. techniques presented via a minimum of 86 distributors. The result’s “Blast RADIUS,” an advanced assault that permits an attacker with an adversary-in-the-middle to achieve keep watch over get entry to to units that use RADIUS to authenticate to a server. “Strangely, within the twenty years since Wang et al. demonstrated the MD5 hash blast in 2004, RADIUS has no longer been changed to take away MD5,” the analysis staff in the back of Blast RADIUS wrote in a paper revealed Tuesday titled RADIUS/UDP Regarded as Susceptible . “In truth, RADIUS turns out to have gained much less safety scrutiny as a result of its presence in these days’s networks.” The newsletter of the paper coincides with safety indicators from a minimum of 90 outlets whose merchandise are in danger. Many of the notes are accompanied via patches that offer temporary fixes, whilst a staff of mavens around the trade develops long-term answers. Any person the use of {hardware} or device that comes with RADIUS must learn the technical knowledge supplied later on this submit and talk over with the protection producer.
Make bigger / Detailed diagram of RADIUS the use of Password Authentication Protocol over UDP.Goldberg et al. Give your affirmation with MD5? In reality? Since 1994, RADIUS has depended on the usage of an effective, local MD5 hash. First evolved in 1991 and authorized via the IETF in 1992, MD5 used to be on the time a not unusual apply for growing what are referred to as “message digests” that encode arbitrary textual content corresponding to numbers, textual content, or binary information to a set period. 16-byte output. For a cryptographic hash serve as, it must be unattainable for an attacker to search out two inputs that fit the similar output. Sadly, MD5 used to be in keeping with a susceptible design: In a couple of years, there have been indicators that the operation may well be extra unhealthy than it used to be concept at the start of the collision that brought about the assaults, a deadly error that allowed the attacker to create two other units that produce. equivalent effects. Those suspicions had been formally showed in a paper revealed in 2004 via researchers Xiaoyun Wang and Hongbo Yu and had been revised in a analysis paper revealed 3 years later. The remaining paper – revealed in 2007 via researchers Marc Stevens, Arjen Lenstra, and Benne de Weger – described what’s referred to as an preliminary collision, a kind of collision that effects from two messages decided on via the attacker, when blended with two further ones. messages, create the similar hash. This is, the adversary freely chooses two other prefixes 𝑃 and 𝑃′ of gibberish that, when blended with the corresponding gibberish-like phrases 𝑆 and 𝑆′, shape the similar hash. Mathematically, the sort of selected preliminary collision may also be written as 𝐻(𝑃‖𝑆)=𝐻(𝑃′‖𝑆′). This sort of assault may be very tough as it provides the attacker the liberty to create extremely custom designed simulations. To reveal the character and damaging results of the assault, Stevens, Lenstra, and de Weger used it to create two cryptographic X.509 certificate that produced the similar MD5 signature however other workforce keys and other portions of the Outstanding Title. Such collisions could cause a certificates authority that desires to signal a certificates for one area to inadvertently signal a certificates for any other, malicious area. In 2008, a gaggle of researchers that incorporated Stevens, Lenstra, and de Weger confirmed how the primary selected phrase on MD5 allowed them to create a malicious certificates that might create a TLS certificates that may be depended on via all primary browsers. The important thing to the assault is device referred to as hashclash, evolved via researchers. Hashclash has been publicly to be had. In spite of the unknown finish of MD5, this serve as has been extensively used for a few years. The decline of MD5 didn’t start in earnest till 2012 after a malware referred to as Flame, allegedly evolved in collaboration with the Israeli and US governments, used to be discovered to have used a key phrase to compromise MD5-based code signing via the Microsoft Home windows replace mechanism. . Flame used collision-enhanced spoofing to thieve the transfer in order that the malware may just unfold from instrument to instrument throughout the inflamed community. 12 years after the Flame assault used to be came upon and two decades after the collision chance used to be showed, MD5 has dropped any other extensively used generation that has defied typical knowledge to transport clear of the RADIUS hashing-protocol device, which is supported via units or units. techniques presented via a minimum of 86 distributors. The result’s “Blast RADIUS,” an advanced assault that permits an attacker with an adversary-in-the-middle to achieve keep watch over get entry to to units that use RADIUS to authenticate to a server. “Strangely, within the twenty years since Wang et al. demonstrated the MD5 hash blast in 2004, RADIUS has no longer been changed to take away MD5,” the analysis staff in the back of Blast RADIUS wrote in a paper revealed Tuesday titled RADIUS/UDP Regarded as Susceptible . “In truth, RADIUS turns out to have gained much less safety scrutiny as a result of its presence in these days’s networks.” The newsletter of the paper coincides with safety indicators from a minimum of 90 outlets whose merchandise are in danger. Many of the notes are accompanied via patches that offer temporary fixes, whilst a staff of mavens around the trade develops long-term answers. Any person the use of {hardware} or device that comes with RADIUS must learn the technical knowledge supplied later on this submit and talk over with the protection producer.






![Pixel 9a design leaks with flat cameras that ditch Google’s maximum recognizable design [Gallery] Pixel 9a design leaks with flat cameras that ditch Google’s maximum recognizable design [Gallery]](https://9to5google.com/wp-content/uploads/sites/4/2024/09/pixel-9a-render-design-leak-2.jpg?quality=82&strip=all&w=1600)