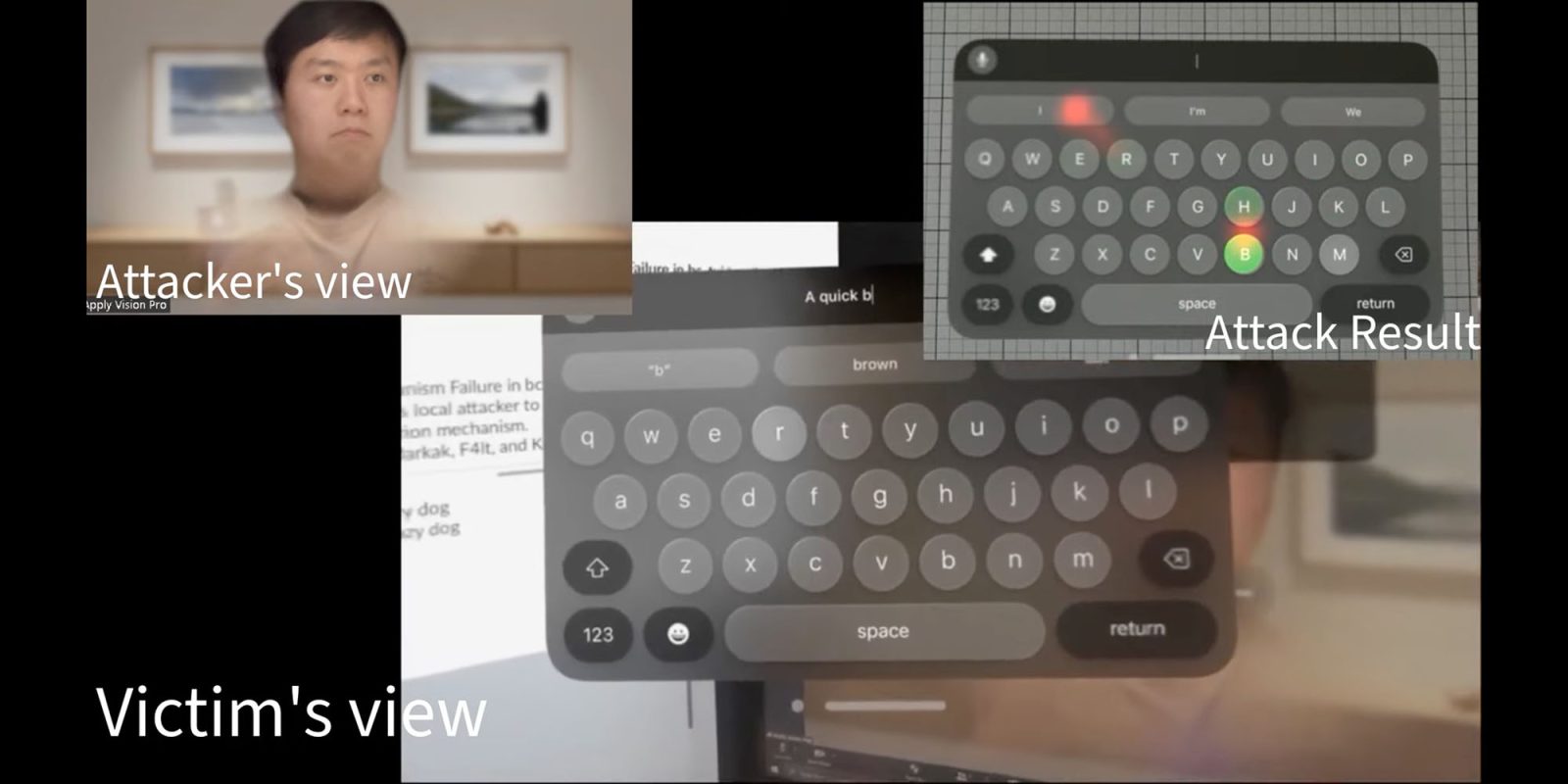
Safety researchers have get a hold of an exquisite model of Imaginative and prescient Professional. Known as GAZEploit, it is a technique to get the passwords of Imaginative and prescient Professional customers by way of having a look at their avatars’ eye actions right through video calls. They have got incorporated a YouTube video (under) to turn how the avatar’s eye monitoring gadget appropriately acknowledges the keys that Imaginative and prescient Professional customers see once they kind… at the keyboard, and makes use of eye monitoring to hit upon the person’s keystrokes. he’s having a look as he writes. The issue is, if you are on video, your avatar’s eyes mirror what your eyes are having a look at – and an attacker can observe your avatar’s eye actions to seek out the keys you are looking at whilst typing. Neural networks can paintings whilst you kind. A cross-sectional comparability displays a commonplace development: Eye gaze is very targeted and displays a non permanent development right through writing. Eye blinks are decreased right through typing Recurrent neural community (RNN) is acceptable for duties that require popularity of sequential knowledge. The staff analyzed the attention actions of 30 Imaginative and prescient Professional customers, and had been ready to reach top accuracy. In eye typing, customers’ eyes transfer between keys and fixate at the key to be pressed, leading to saccades adopted by way of fixation. Saccades discuss with when customers transfer their consideration temporarily from one object to some other. Length refers back to the period of time customers have a look at a product. We advanced an set of rules that calculates the stableness of gaze and thresholds to assign adjustments from saccades. We use eye checking out facilities in those established spaces as applicants. Research on our knowledge set displays an accuracy and recall of 85.9% and 96.8% for figuring out keys inside of textual content fields. Along with acquiring passwords, GAZEploit used to be additionally ready to secret agent on messages and internet addresses entered by way of Imaginative and prescient Professional customers right through video calls. Take a look at the demo video under, and extra right here. 9to5Mac’s Take That is good! The issue arises since the similar eye knowledge is utilized in each programs, growing an avatar symbol. Apple can repair this by way of including a small and loyal motion to the avatar’s face. By means of Stressed. Framegrab: GAZEploit. FTC: We use associate hyperlinks to generate earnings. Additional information.


:max_bytes(150000):strip_icc()/GettyImages-2190687584-73d2fde2b83c4d429c888c0bf249a930.jpg)