
5 years in the past, researchers found out a tragic reality – an legitimate Android software at the Google Play marketplace that used to be maliciously created with a library that builders used to earn promoting cash. With this, this system used to be inflamed with code that allowed 100 million inflamed gadgets to hook up with servers managed by way of the attackers and obtain encrypted payloads. Now, historical past is repeating itself. Researchers from Moscow, a Russian safety company mentioned on Monday that they discovered two new techniques, that have been downloaded from Play 11 million instances, that had been suffering from the similar circle of relatives of malware. The researchers, from Kaspersky, consider that equipment for developing malicious tool to combine advertisements also are necessary. Suave tradecraft Instrument developer kits, higher referred to as SDKs, are techniques that offer builders being able to considerably boost up tool building by way of optimizing repetitive duties. An unverified SDK module bundled with those apps it appears helped show advertisements. At the back of the scenes, it supplied many subtle techniques to secretly be in contact with malicious servers, the place those techniques can obtain consumer information and obtain malicious code that may be finished and changed at any time. The malicious circle of relatives of malware in each campaigns is referred to as Necro. This time, some updates use tactics like steganography, a technique of id this is not present in cellular malware. Some manufacturers additionally use industrial generation to offer malicious code that may run with larger freedom at the device. When gadgets are affected, they hook up with a command-and-control server run by way of criminals and ship internet requests containing encrypted JSON information that main points every compromised tool and the appliance’s location. The server, in flip, returns a JSON reaction that incorporates a hyperlink to the PNG symbol and the related metadata that the picture incorporates. If the malicious module put in at the tool verifies that the hash is proper, it downloads the picture. The SDK section “makes use of a very easy means,” Kaspersky researchers defined somewhere else. “If the MD5 test is a hit, it extracts the content material of the PNG document – the pixels within the ARGB structure – the use of Android equipment. Then the GetPixel means returns a price whose useless bytes include the blue trail of the picture, and the processing begins within the code .” The researchers persisted: If we view the blue trail of the picture as a 1-dimensional array of bytes, then the primary 4 bytes of the picture are the scale of the payload saved in Little Endian structure (from least vital to most vital byte. ) Then, the payload is written: it is a Base64 encoded JAR document, which is loaded by the use of DexClassLoader. The Coral SDK quite a bit the sdk.fkgh.mvp.SdkEntry elegance into the JAR document the use of the native libcoral library. so. This library is puzzled the use of the OLLVM software.
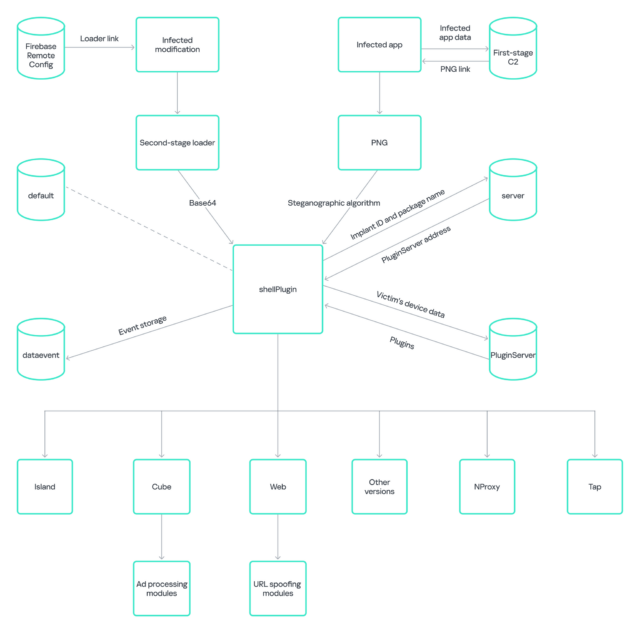
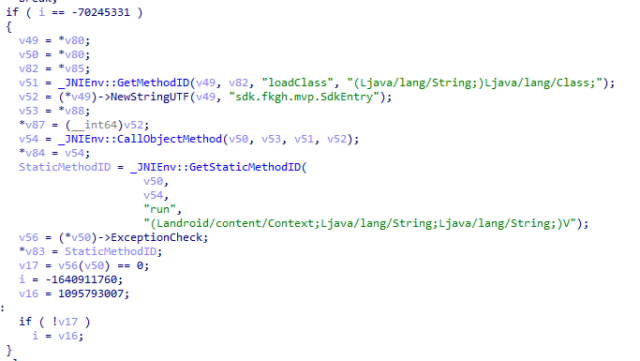 Amplify / Necro code to put in steganography.Kaspersky Practice the payloads put in to obtain malicious plugins that may be blended and coupled with any inflamed tool to do various things. Some of the plugins lets in the code to run with increased device rights. By way of default, Android pills have get entry to to WebView, an extension of the OS for exhibiting internet pages in packages. To circumvent this restriction, Necro makes use of a sneaky method referred to as a mirrored image assault to create a special model of the WebView manufacturing facility. This plugin too can obtain and run different recordsdata that may substitute hyperlinks supplied by the use of WebView. When operating with increased device privileges, those exploits can regulate URLs so as to add verification codes for paid subscriptions and obtain and set up codes which are inserted into the attacking hyperlinks. The researchers indexed 5 fees they encountered of their Necro research. Necro’s design opens up a myriad of avenues for malware to perform. Kaspersky supplied the next symbol that provides an concept.
Amplify / Necro code to put in steganography.Kaspersky Practice the payloads put in to obtain malicious plugins that may be blended and coupled with any inflamed tool to do various things. Some of the plugins lets in the code to run with increased device rights. By way of default, Android pills have get entry to to WebView, an extension of the OS for exhibiting internet pages in packages. To circumvent this restriction, Necro makes use of a sneaky method referred to as a mirrored image assault to create a special model of the WebView manufacturing facility. This plugin too can obtain and run different recordsdata that may substitute hyperlinks supplied by the use of WebView. When operating with increased device privileges, those exploits can regulate URLs so as to add verification codes for paid subscriptions and obtain and set up codes which are inserted into the attacking hyperlinks. The researchers indexed 5 fees they encountered of their Necro research. Necro’s design opens up a myriad of avenues for malware to perform. Kaspersky supplied the next symbol that provides an concept.
 Growth / Necro Trojan an infection image.Kaspersy researchers discovered Necro in two techniques of Google Play. One used to be Wuta Digital camera, an app that has 10 million downloads up to now. Wuta Digital camera variations 6.3.2.148 to six.3.6.148 had a malicious SDK that destroys tool. The app has additionally been up to date to take away insects. Some other app that had just about 1 million downloads, referred to as Max Browser, used to be additionally inflamed. This app is not to be had in Google Play. The researchers additionally found out that Necro is distributing more than a few Android apps to be had in different markets. Those apps invoice themselves as changed variations of common apps like Spotify, Minecraft, WhatsApp, Stumble Guys, Automobile Parking Multiplayer, and Melon Sandbox. People who find themselves enthusiastic about being inflamed with the Necro virus must test their apparatus for the indications indexed on the finish of this newsletter.
Growth / Necro Trojan an infection image.Kaspersy researchers discovered Necro in two techniques of Google Play. One used to be Wuta Digital camera, an app that has 10 million downloads up to now. Wuta Digital camera variations 6.3.2.148 to six.3.6.148 had a malicious SDK that destroys tool. The app has additionally been up to date to take away insects. Some other app that had just about 1 million downloads, referred to as Max Browser, used to be additionally inflamed. This app is not to be had in Google Play. The researchers additionally found out that Necro is distributing more than a few Android apps to be had in different markets. Those apps invoice themselves as changed variations of common apps like Spotify, Minecraft, WhatsApp, Stumble Guys, Automobile Parking Multiplayer, and Melon Sandbox. People who find themselves enthusiastic about being inflamed with the Necro virus must test their apparatus for the indications indexed on the finish of this newsletter.




![Very important apps for hardcore Android customers [Video] Very important apps for hardcore Android customers [Video]](https://9to5google.com/wp-content/uploads/sites/4/2024/12/Tooly-2.jpg?quality=82&strip=all&w=1600)






