The Bumblebee malware loader has been noticed in new assaults lately, 4 months after Europol hacked it right through ‘Operation Endgame’ in Would possibly. Believed to be the introduction of TrickBot, the malware emerged in 2022 as a substitute for the BazarLoader backdoor to provide cybercriminals get right of entry to to sufferer networks. Bumblebee continuously will get inflamed thru phishing, malvertising, and search engine marketing poisoning that promotes quite a lot of instrument (corresponding to Zooom, Cisco AnyConnect, ChatGPT, and Citrix Workspace). Some of the payloads presented via Bumblebee are Cobalt Strike beacons, id robbery malware, and different kinds of ransomware. Within the month of Would possibly, the global safety staff known as ‘Operation Endgame’ took over greater than 100 servers that beef up many malware, together with IcedID, Pikabot, Trickbot, Bumblebee, Smokeloader, and SystemBC. From then on, Bumblebee remained silent. Alternatively, researchers at cybersecurity company Netskope have noticed a brand new Bumblebee carrier related to malware, which might point out a resurgence. The most recent wave of Bumblebee The most recent Bumblebee assault starts with a phishing e mail that lures the sufferer into downloading a malicious ZIP document. The compressed document accommodates a .LNK shortcut named Record-41952.lnk, which reasons PowerShell to obtain a malicious .MSI (y.msi) document disguised as a valid NVIDIA driving force or Midjourney installer from a far flung server.
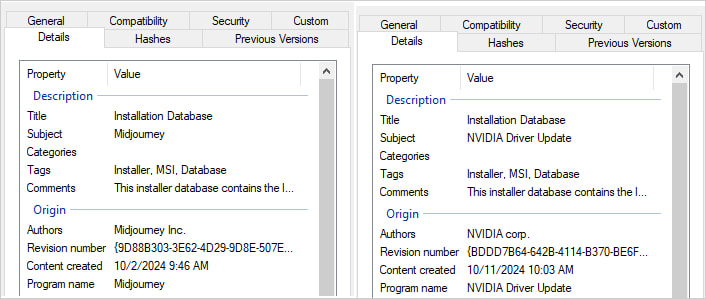 Builders of Midjourney are NVIDIA
Builders of Midjourney are NVIDIA
Supply: Netskope The MSI document is accomplished silently the use of msiexec.exe with the /qn possibility, which guarantees that the method runs with out consumer interplay. To keep away from producing new, noisy processes, the malware makes use of the SelfReg desk inside the MSI framework, which instructs msiexec.exe to obtain the DLL from its cope with area and contact its DllRegisterServer serve as. As soon as the DLL is put in and accomplished, the malware extraction procedure starts, which ends up in Bumblebee being despatched to reminiscence.
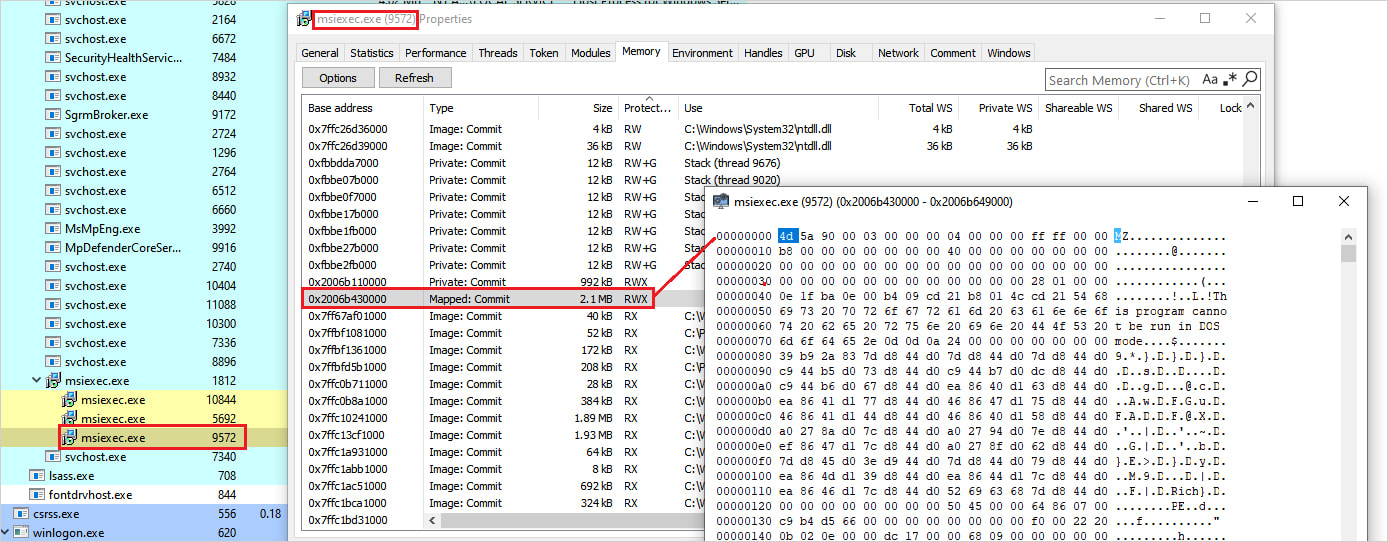 The overall payload is recorded in reminiscence via the msiexec manner.
The overall payload is recorded in reminiscence via the msiexec manner.
Supply: Netskope Netskope feedback that the Bumblebee payload carries its interior DLL signature and exported purposes to specify configuration, in addition to configuration strategies that had been observed in earlier variations. The RC4 key that clears the adjustments from the most recent replace makes use of the string “NEW_BLACK”, the place there are two marketing campaign IDs, “msi” and “lnk001.”
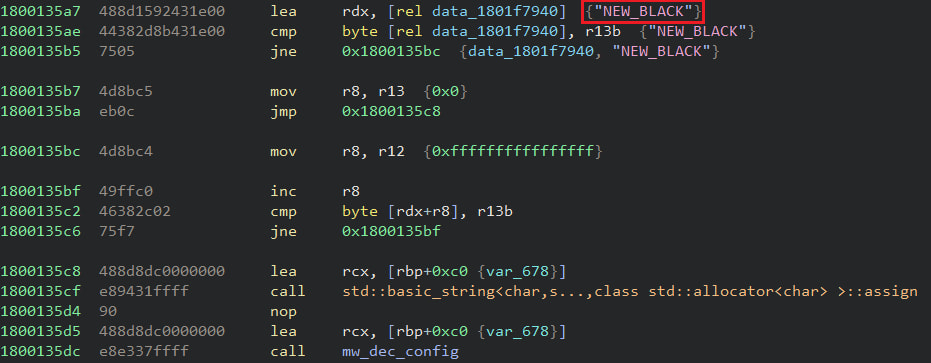 The “NEW_BLACK” string that looks on contemporary bills
The “NEW_BLACK” string that looks on contemporary bills
Supply: Netskope Netskope didn’t say the rest concerning the choice of bills Bumblebee took down or the dimensions of the marketing campaign however the file is a caution of early indicators of a resurgence. A whole listing of compromise signs is to be had in this GitHub web page.