A safety vulnerability has been came upon within the USB-C port controller this is put in at the iPhone 15 and 16. Alternatively, the use of this will also be so tricky that Apple and the protection researcher who came upon it showed that it does no longer pose a danger to the actual international. Alternatively, the protection downside that threatens iPhone customers is a technique utilized by scammers to avoid considered one of Apple’s safety… The primary chip used to be offered in Apple merchandise in 2023. In truth, it may be used to hack the iPhone, akin to Cyber Safety Information stories. Safety researchers hacked Apple’s ACE3 USB-C controller. This chip, which used to be offered with the iPhone 15 and iPhone 15 Professional, represents an enormous bounce in USB-C era, operating to switch energy and act as a small controller with get admission to to vital interior programs. […]
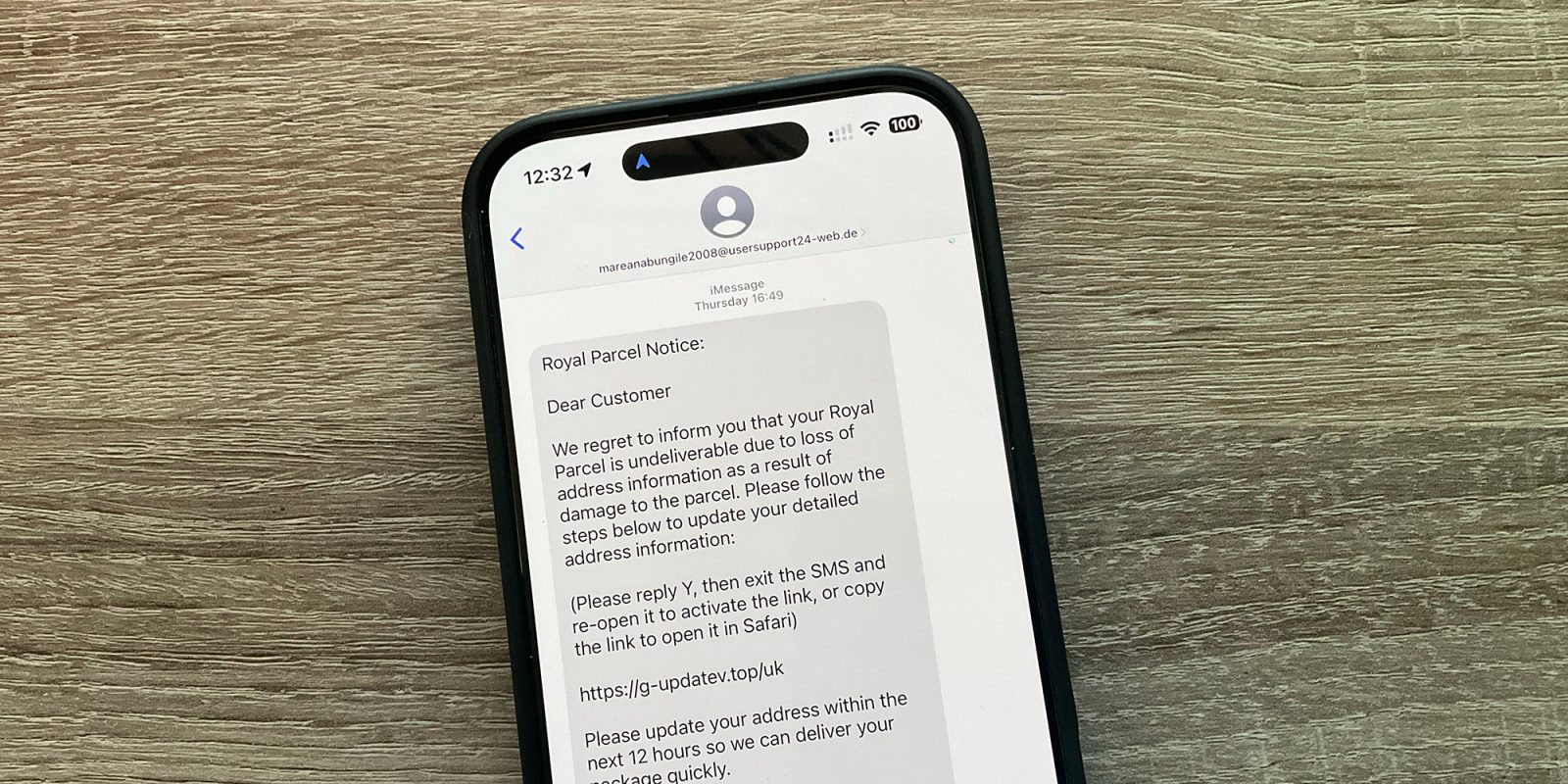
[Roth’s team was able] to search out the codes at the ACE3 chip. Via in moderation measuring the electromagnetic indicators right through the initialization of the chip, they made up our minds the precise time when the firmware verification came about. The usage of energy injection at this important time, they handed the verification exams and put in the up to date firmware patch into the chip’s CPU. In principle, this may give an attacker entire keep watch over over the iPhone. Alternatively, it calls for get admission to to the software, and it is extremely tricky to take away it. Macworld reported that Apple made up our minds it used to be no longer unhealthy after investigating the process used, and Roth agreed. Signals created by means of iMessage scammers can bypass SMS safety and iMessages are utilized by hackers to ship phishing hyperlinks, and to take a look at to put in malware on iPhones. To give protection to by contrast, if you happen to obtain an iMessage from somebody who isn’t to your courting, and with whom you could have by no means despatched messages, your iPhone will disable any hyperlinks within the message. They appear to be easy phrases, and so they can’t be recorded. Alternatively, scammers have discovered some way round this. In the event that they inspire you to answer the message, even with a STOP command supposed to instruct the approved sender to not ship you a message once more, then this coverage will probably be misplaced. BleepingComputer says that you’ve got despatched them messages, despite the fact that you answer to 1 individual, it implies that the iPhone considers them as professional and opens their hyperlinks. Apple informed BleepingComputer that if the consumer replies to the message or provides the sender to their record, the hyperlinks will probably be activated. During the last few months, BleepingComputer has noticed an build up in threats that try to trick customers into answering textual content messages in an effort to have hyperlinks reset. This web page presentations examples of bogus paperwork that declare to be from the USPS and a toll corporate, every asking the recipient to respond to with Y. This may end up in hyperlinks. It is easy sufficient that I used to be ready to search out the highest instance symbol simply by having a look in my deleted messages folder. How to give protection to your self Don’t click on or click on on a hyperlink won in an e mail or different message until you are expecting it. The easiest way to do that is to only use your individual bookmarks or manually input the URLs, and simplest do that in case you have excellent explanation why to imagine that the message is authentic. When unsure, name or e mail the corporate the use of the touch main points to substantiate. Photograph: 9to5Mac FTC: We use associate hyperlinks that generate source of revenue. Additional information.











