Hackers are all the time discovering new tactics to get into your gadgets. A brand new iOS vulnerability now lets in hackers to secret agent in your keyboard. Certo Tool launched a revealing document on how cybercriminals are bypassing Apple’s same old security features to scouse borrow your individual knowledge. The principle factor hackers are doing is putting in a third-party keyboard with a keylogger for your iPhone. They’re going to conceal the keylogger in a small program and use Apple’s TestFlight software to permit builders to circumvent Apple’s safety exams. Hackers hope you’ll be able to obtain those techniques and alter your content material.CLICK TO GET KURT’S FREE CYBERGUY NEWSLETTER CONTAINS EVENTS, HOW-TO VIDEOS, REVIEWS, AND EASY TUTORIALS What’s TestFlight? their tool, and TestFlight supplies a spot for it. It lets in builders to obtain unfinished tool and ship hyperlinks to testers. They’ve a number of tactics to take a look at, too. Builders will have testers to make use of all the app or create “Applets” or explicit checks. Testers give you the chance to check all the program or “Systems” and supply comments to each the tool developer and Apple.  TestFlight program. (Apple) It’s the maximum complicated software of Apple. Many evaluations point out how simple it’s to make use of and the way it makes beta checking out a breeze. There also are different safety considerations. Apple stocks your identify and e mail cope with should you use the app. If you are a tester, it stocks the kind of software you might be the use of, the provider and different knowledge.MORE: BEWARE OF FAKE ADVICE ON YOUR MAC Are hackers the use of TestFlight to scouse borrow your knowledge? to do. It is going to release a small program with a default keyboard. The keyboard has a keylogger, which data the entirety you kind and sends it to them. As soon as this system is put in in your telephone, they are going to set up a customized keyboard in your iPhone during the settings of your program and supply all keyboard get entry to. They’re going to then exchange your default keyboard to any other model in their malicious. You have to observe that, usually, those keyboards glance just like the iPhone keyboard – which makes it not possible to inform if you are the use of a pretend keyboard.
TestFlight program. (Apple) It’s the maximum complicated software of Apple. Many evaluations point out how simple it’s to make use of and the way it makes beta checking out a breeze. There also are different safety considerations. Apple stocks your identify and e mail cope with should you use the app. If you are a tester, it stocks the kind of software you might be the use of, the provider and different knowledge.MORE: BEWARE OF FAKE ADVICE ON YOUR MAC Are hackers the use of TestFlight to scouse borrow your knowledge? to do. It is going to release a small program with a default keyboard. The keyboard has a keylogger, which data the entirety you kind and sends it to them. As soon as this system is put in in your telephone, they are going to set up a customized keyboard in your iPhone during the settings of your program and supply all keyboard get entry to. They’re going to then exchange your default keyboard to any other model in their malicious. You have to observe that, usually, those keyboards glance just like the iPhone keyboard – which makes it not possible to inform if you are the use of a pretend keyboard.  An individual is protecting a telephone appearing their apps. (Kurt “CyberGuy” Knutsson) MORE: HOW TO PROTECT YOUR IPHONE AGAINST CYBERATTACKS AND LOCKDOWN QUESTIONS How to offer protection to your self To be sure to’re no longer the use of a hacky keyboard, you must test your keyboard personal tastes in iOS. Here is tips on how to test: Pass on your Settings app Faucet Extra Faucet Keyboards Then faucet Keyboards
An individual is protecting a telephone appearing their apps. (Kurt “CyberGuy” Knutsson) MORE: HOW TO PROTECT YOUR IPHONE AGAINST CYBERATTACKS AND LOCKDOWN QUESTIONS How to offer protection to your self To be sure to’re no longer the use of a hacky keyboard, you must test your keyboard personal tastes in iOS. Here is tips on how to test: Pass on your Settings app Faucet Extra Faucet Keyboards Then faucet Keyboards 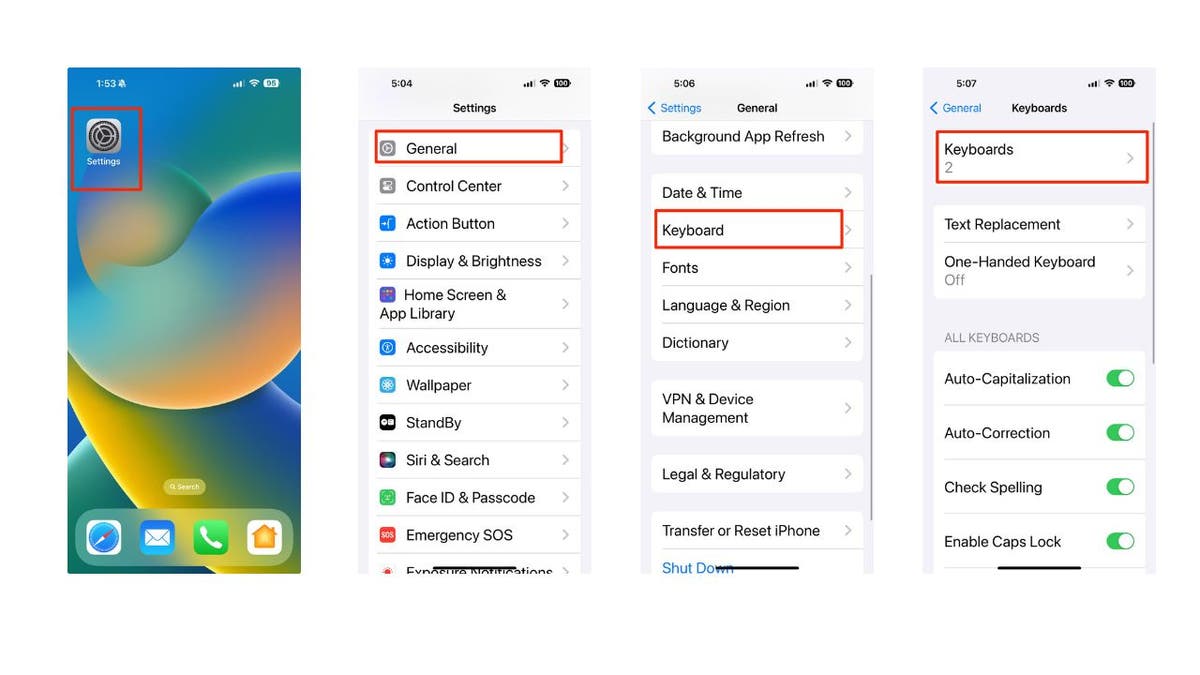 Techniques to view your keyboard personal tastes in iOS. (Kurt “CyberGuy” Knutsson )You must see the keyboards you might be usingClick on Edit to take away everythingTo take away a keyboard, simply click on the pink take away icon in entrance of the keyboardFROM STICKERS TO SUPPORT EMAILS: HOW AI IS CREATING MORE REAL THINGS.
Techniques to view your keyboard personal tastes in iOS. (Kurt “CyberGuy” Knutsson )You must see the keyboards you might be usingClick on Edit to take away everythingTo take away a keyboard, simply click on the pink take away icon in entrance of the keyboardFROM STICKERS TO SUPPORT EMAILS: HOW AI IS CREATING MORE REAL THINGS.  Easy methods to set up your iPhone keyboard personal tastes in iOS. (Kurt “CyberGuy” Knutsson) MORE: POLICE HELP PARENTS TURN OFF APPLE IPHONES WITH CHILDREN’S FEATURES How to offer protection to your iPhone from keyboard spying Steer clear of downloading apps from unknown or untrusted resources. Best obtain apps from the respectable App Retailer or from respected builders. Watch out when the use of TestFlight to check tool. Learn the app description and evaluations sparsely ahead of putting in. Don’t grant get entry to to any keyboards you don’t acknowledge or consider. Test your keyboard settings steadily and take away any suspicious or undesirable keyboards. You’ll be able to apply the stairs discussed above to do that. Replace your iOS to the most recent model and set up any safety patches that Apple releases. This may assist repair any vulnerabilities or insects that hackers would possibly exploit. Have excellent anti-virus tool on all of your gadgets. Blockading hackers out of your gadgets will also be have shyed away from when you have a excellent anti-virus tool. Having antivirus tool in your software will make sure that you might be stopped from clicking on any malicious hyperlinks that would possibly set up malware in your software, permitting hackers to realize get entry to on your knowledge. In finding my Perfect Antivirus Coverage evaluate right here. What to do if you’re suffering from a keyboard spyware and adware danger it has already came about, so you want to take quick motion to attenuate the wear and offer protection to your software. Listed below are the stairs you’ll apply: APPLE HAS RELEASED MOST IOS UPDATES DUE TO SECURITY1. Alternate your password. If hackers have recorded your passwords the use of a keylogger, they are able to get entry to your on-line accounts and scouse borrow your knowledge or cash. FOR SOMETHING (for instance, your pc or pc), you must exchange the passwords for all of your necessary accounts, similar to e mail, banking, social networks, and many others. You need to do that on any other software in order that the hacker does not report you. add your password in your hacked software. Use sturdy and distinctive passwords which might be tough to bet or crack. You’ll be able to additionally use a password supervisor to create and retailer your passwords securely.2. Arrange your accounts and actions. You must test your on-line accounts and transactions steadily for any suspicious or unauthorized process. If you happen to realize the rest abnormal, notify your healthcare supplier or the government once imaginable. You must additionally evaluate your credit score experiences and ratings for indicators of robbery or fraud.3. Touch your financial institution and bank card corporations. If hackers get your financial institution or bank card knowledge, they are able to use it to make purchases or withdraw cash with out your permission. You must touch your financial institution and bank card corporations and allow them to know what’s going on. They may be able to let you droop or cancel your playing cards, prosecute any fraud fees and factor new playing cards.4. Watch out with your pals. If hackers have get entry to on your e mail or social media accounts, they are able to use them to ship junk mail or phishing messages on your contacts. They may be able to additionally impersonate you and ask for cash or your knowledge. You should alert your contacts and warn them to not open or reply to any messages from you that seem suspicious or abnormal.5. Reset your software to manufacturing facility settings. If you wish to make certain your software is freed from malware or spyware and adware, you’ll repair it to manufacturing facility settings. This may increasingly erase all of your knowledge and settings and repair the unique model of iOS. You must again up your necessary knowledge ahead of doing this, and repair it from a relied on supply.6. Use knowledge safety: If hackers can report the entirety you kind in your keyboard, they are able to use that knowledge to open accounts for your identify, get entry to your financial institution and bank card accounts, and impersonate you on-line. That is the place knowledge safety corporations are available. They may be able to observe your knowledge similar to your house cope with, Social Safety Quantity (SSN), telephone quantity and e mail cope with and notify you if you’re the use of it to open an account. They may be able to additionally let you freeze your financial institution and bank card accounts to stop unauthorized use by means of criminals. Take a look at my guidelines and recommendation on how to offer protection to your self from scams.Kurt’s Giant TakeawaysThere are loads, if no longer 1000’s, of how other folks can scouse borrow your knowledge. You’ll be able to do your self a prefer by means of giving them much less of a possibility to scouse borrow from you by means of being cautious about the place you obtain your tool and tracking malware. CLICK HERE FOR THE FOX NEWS APP Do you assume tech corporations like Apple must take steps to offer protection to you from attainable malware, or do you consider it is a duty? your to offer protection to your apparatus? Tell us by means of writing to us at Cyberguy.com/ContactFor my tech guidelines & safety guidelines, subscribe to my loose CyberGuy Record by means of going to Cyberguy.com/NewsletterAsk Kurt a query or let us know a tale you need us to hide. Solutions to CyberGuy’s maximum regularly requested questions:CyberGuy Perfect Vacation Reward GuideCopyright 2023 CyberGuy.com. All rights reserved. Kurt “CyberGuy” Knutsson is an award-winning generation journalist who’s keen about generation, devices and gear that make lifestyles higher and he contributes to Fox Information & FOX Industry beginning within the morning on “FOX & Pals.” Have a technical query? Get Kurt’s CyberGuy Publication, percentage your phrases, tales or feedback on CyberGuy.com.
Easy methods to set up your iPhone keyboard personal tastes in iOS. (Kurt “CyberGuy” Knutsson) MORE: POLICE HELP PARENTS TURN OFF APPLE IPHONES WITH CHILDREN’S FEATURES How to offer protection to your iPhone from keyboard spying Steer clear of downloading apps from unknown or untrusted resources. Best obtain apps from the respectable App Retailer or from respected builders. Watch out when the use of TestFlight to check tool. Learn the app description and evaluations sparsely ahead of putting in. Don’t grant get entry to to any keyboards you don’t acknowledge or consider. Test your keyboard settings steadily and take away any suspicious or undesirable keyboards. You’ll be able to apply the stairs discussed above to do that. Replace your iOS to the most recent model and set up any safety patches that Apple releases. This may assist repair any vulnerabilities or insects that hackers would possibly exploit. Have excellent anti-virus tool on all of your gadgets. Blockading hackers out of your gadgets will also be have shyed away from when you have a excellent anti-virus tool. Having antivirus tool in your software will make sure that you might be stopped from clicking on any malicious hyperlinks that would possibly set up malware in your software, permitting hackers to realize get entry to on your knowledge. In finding my Perfect Antivirus Coverage evaluate right here. What to do if you’re suffering from a keyboard spyware and adware danger it has already came about, so you want to take quick motion to attenuate the wear and offer protection to your software. Listed below are the stairs you’ll apply: APPLE HAS RELEASED MOST IOS UPDATES DUE TO SECURITY1. Alternate your password. If hackers have recorded your passwords the use of a keylogger, they are able to get entry to your on-line accounts and scouse borrow your knowledge or cash. FOR SOMETHING (for instance, your pc or pc), you must exchange the passwords for all of your necessary accounts, similar to e mail, banking, social networks, and many others. You need to do that on any other software in order that the hacker does not report you. add your password in your hacked software. Use sturdy and distinctive passwords which might be tough to bet or crack. You’ll be able to additionally use a password supervisor to create and retailer your passwords securely.2. Arrange your accounts and actions. You must test your on-line accounts and transactions steadily for any suspicious or unauthorized process. If you happen to realize the rest abnormal, notify your healthcare supplier or the government once imaginable. You must additionally evaluate your credit score experiences and ratings for indicators of robbery or fraud.3. Touch your financial institution and bank card corporations. If hackers get your financial institution or bank card knowledge, they are able to use it to make purchases or withdraw cash with out your permission. You must touch your financial institution and bank card corporations and allow them to know what’s going on. They may be able to let you droop or cancel your playing cards, prosecute any fraud fees and factor new playing cards.4. Watch out with your pals. If hackers have get entry to on your e mail or social media accounts, they are able to use them to ship junk mail or phishing messages on your contacts. They may be able to additionally impersonate you and ask for cash or your knowledge. You should alert your contacts and warn them to not open or reply to any messages from you that seem suspicious or abnormal.5. Reset your software to manufacturing facility settings. If you wish to make certain your software is freed from malware or spyware and adware, you’ll repair it to manufacturing facility settings. This may increasingly erase all of your knowledge and settings and repair the unique model of iOS. You must again up your necessary knowledge ahead of doing this, and repair it from a relied on supply.6. Use knowledge safety: If hackers can report the entirety you kind in your keyboard, they are able to use that knowledge to open accounts for your identify, get entry to your financial institution and bank card accounts, and impersonate you on-line. That is the place knowledge safety corporations are available. They may be able to observe your knowledge similar to your house cope with, Social Safety Quantity (SSN), telephone quantity and e mail cope with and notify you if you’re the use of it to open an account. They may be able to additionally let you freeze your financial institution and bank card accounts to stop unauthorized use by means of criminals. Take a look at my guidelines and recommendation on how to offer protection to your self from scams.Kurt’s Giant TakeawaysThere are loads, if no longer 1000’s, of how other folks can scouse borrow your knowledge. You’ll be able to do your self a prefer by means of giving them much less of a possibility to scouse borrow from you by means of being cautious about the place you obtain your tool and tracking malware. CLICK HERE FOR THE FOX NEWS APP Do you assume tech corporations like Apple must take steps to offer protection to you from attainable malware, or do you consider it is a duty? your to offer protection to your apparatus? Tell us by means of writing to us at Cyberguy.com/ContactFor my tech guidelines & safety guidelines, subscribe to my loose CyberGuy Record by means of going to Cyberguy.com/NewsletterAsk Kurt a query or let us know a tale you need us to hide. Solutions to CyberGuy’s maximum regularly requested questions:CyberGuy Perfect Vacation Reward GuideCopyright 2023 CyberGuy.com. All rights reserved. Kurt “CyberGuy” Knutsson is an award-winning generation journalist who’s keen about generation, devices and gear that make lifestyles higher and he contributes to Fox Information & FOX Industry beginning within the morning on “FOX & Pals.” Have a technical query? Get Kurt’s CyberGuy Publication, percentage your phrases, tales or feedback on CyberGuy.com.
The brand new iPhone safety danger that permits hackers to secret agent in your telephone














