Getty Photographs Crooks are running tougher to spot unlawful actions at the Web the usage of 1000’s of unsuspecting consumer units, as evidenced via two unrelated stories revealed on Tuesday. The primary, from the protection company Lumen Labs, says that about 40,000 house and place of business routers had been registered in hacking firms that don’t point out Web safety, whilst any other 1,000 new units are being added each day. The malware in price is TheMoon, a malicious code circle of relatives from 2014. In its early days, TheMoon inflamed a Linksys E1000. Over time it has desirous about Asus WRTs, Vivotek Community Cameras, and several other D-Hyperlink fashions. Within the years following its release, TheMoon's self-propagating habits and greater skill to disrupt a couple of constructions resulted in a rising pattern that attracted consideration in safety circles. Lately, the illusion of the Web of Issues botnet stopped, main many to assume that it used to be utterly unnecessary. To the marvel of Lumen's Black Lotus Lab researchers, in a 72-hour duration previous this month, TheMoon added 6,000 ASUS routers to its community, which displays that the botnet is as robust as ever. Much more sudden than the invention of greater than 40,000 inflamed small places of work and residential places of work in 88 nations is the revelation that TheMoon is registering most of the inflamed units in Faceless, a carrier this is bought on on-line boards to steer clear of anonymity. unlawful issues. The proxy carrier become in style remaining yr following this profile via KrebsOnSecurity. Commercial “An international community of compromised SOHO routers offers actors the power to avoid different safety equipment at the community—particularly the ones in keeping with geolocation, system-based blocking off, or concentrated on TOR blocking off,” Black Lotus researchers wrote Tuesday. He added that “80 % of Faceless bots are situated in the US, this means that that US accounts and establishments are crucial. We suspect that the collection of criminals is also leaking passwords and / or exfiltrating knowledge, particularly for monetary firms. ” The researchers endured to mention that the process The standard way of detecting abuse at the Web could have fallen out of fashion with some hackers. VPNs, as an example, can file consumer task although some carrier suppliers say differently. The researchers say that the power to hack the nameless Tor browser could have additionally threatened some customers. The second one consequence got here from Satori Intelligence , the protection analysis group HUMAN, reported that it discovered 28 apps to be had in Google Play that, unbeknownst to customers, registered their units in a house community with 190,000 nodes on the core to steer clear of detection and intervene with Web visitors.
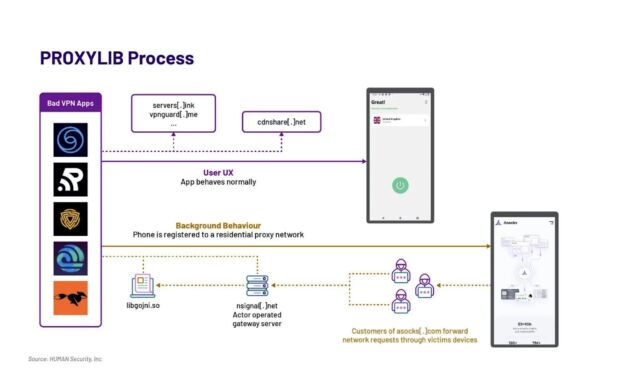 HUMAN ProxyLib, the identify Satori gave to the community, is derived from Oko VPN, an app that used to be got rid of from Play remaining yr after it used to be uncovered as the usage of inflamed equipment for advert fraud. The 28 apps Satori discovered all copied Oko VPN's code, which made them Asock hotspots.
HUMAN ProxyLib, the identify Satori gave to the community, is derived from Oko VPN, an app that used to be got rid of from Play remaining yr after it used to be uncovered as the usage of inflamed equipment for advert fraud. The 28 apps Satori discovered all copied Oko VPN's code, which made them Asock hotspots.
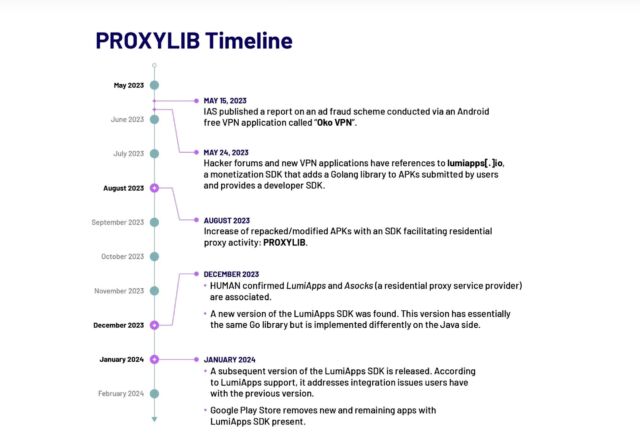 HUMAN The researchers additionally known a 2nd era of ProxyLib tool evolved via lumiapps[.]io, a tool construction software that makes use of the similar capability and makes use of the similar server as Oko VPN. The LumiApps SDK permits builders to combine their code into the library to support efficiency. It additionally permits builders to take action with no need to create a consumer account or recode. As a substitute they are able to set up their customized code and obtain the brand new model. Promoting
HUMAN The researchers additionally known a 2nd era of ProxyLib tool evolved via lumiapps[.]io, a tool construction software that makes use of the similar capability and makes use of the similar server as Oko VPN. The LumiApps SDK permits builders to combine their code into the library to support efficiency. It additionally permits builders to take action with no need to create a consumer account or recode. As a substitute they are able to set up their customized code and obtain the brand new model. Promoting
 HUMAN “Satori seen other folks the usage of LumiApps units within the wild,” the researchers wrote. “Lots of the apps we known between Might and October 2023 seem to be mods of in style apps, which additionally displays that customers don't want to have the supply code of the app to replace them the usage of LumiApps. Those apps are referred to as 'mods' or are offered as changed variations and disbursed outdoor of Google Play Retailer.” The researchers don't know if the 190,000 nodes with Asock core had been created via inflamed Android units or in the event that they integrated different sorts of units compromised via different strategies. After all, this quantity displays the recognition of nameless proxies. Individuals who wish to save you their units from being registered in such networks will have to be somewhat cautious. The primary is to withstand the temptation to proceed the usage of the apparatus when it’s not supported via the producer. Lots of the units that had been swept up in TheMoon, as an example, have reached end-of-life, which means they not obtain safety updates. Additionally it is necessary to put in safety settings in time and disable UPnP except there’s a excellent reason why to permit it most effective at the vital ports. Android software customers will have to set up apps slowly after which most effective after checking the historical past of the app and the developer.
HUMAN “Satori seen other folks the usage of LumiApps units within the wild,” the researchers wrote. “Lots of the apps we known between Might and October 2023 seem to be mods of in style apps, which additionally displays that customers don't want to have the supply code of the app to replace them the usage of LumiApps. Those apps are referred to as 'mods' or are offered as changed variations and disbursed outdoor of Google Play Retailer.” The researchers don't know if the 190,000 nodes with Asock core had been created via inflamed Android units or in the event that they integrated different sorts of units compromised via different strategies. After all, this quantity displays the recognition of nameless proxies. Individuals who wish to save you their units from being registered in such networks will have to be somewhat cautious. The primary is to withstand the temptation to proceed the usage of the apparatus when it’s not supported via the producer. Lots of the units that had been swept up in TheMoon, as an example, have reached end-of-life, which means they not obtain safety updates. Additionally it is necessary to put in safety settings in time and disable UPnP except there’s a excellent reason why to permit it most effective at the vital ports. Android software customers will have to set up apps slowly after which most effective after checking the historical past of the app and the developer.