
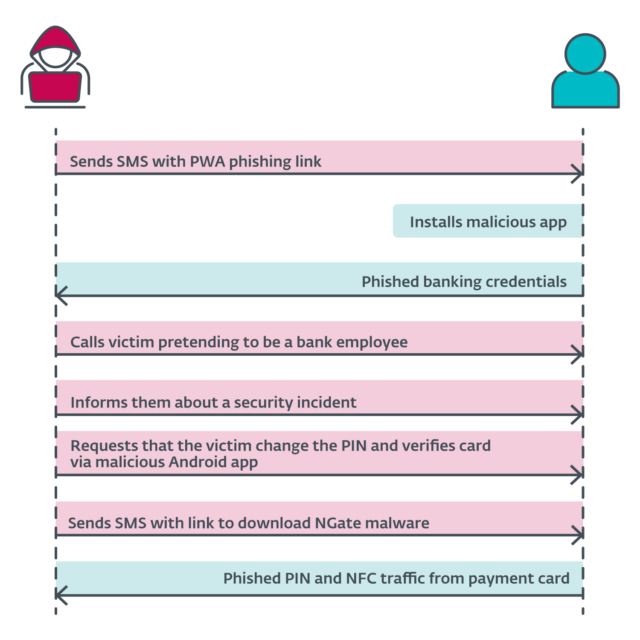
A newly found out Android malware steals bank card knowledge the use of an inflamed NFC reader and passes it directly to attackers, a brand new method that effectively syncs the cardboard for use at an ATM or level of sale, safety company ESET mentioned. ESET researchers named the malware NGate as it comprises NFCGate, an open supply software for taking pictures, inspecting, or editing NFC visitors. Brief for Close to-Box Communique, NFC is a protocol that permits two units to keep in touch wirelessly over quick distances. “It is a new Android situation, and it is the first time now we have noticed Android malware getting used within the wild,” ESET researcher Lukas Stefanko mentioned in a video appearing the findings. “The malware is in a position to ship NFC knowledge from the sufferer’s card thru a compromised software to the attacker’s cell phone, which will seize the cardboard and withdraw money from the ATM.” Lukas Stefanko—Opening the Nest. The malware is in keeping with previous scams, akin to the ones that concentrate on customers via sending textual content messages and tricking them into depositing NGAte from transient spaces that mimic banks or reputable cell banking apps to be had on Google Play. Performing like a goal financial institution’s authentication app, NGate activates the person to go into the financial institution’s buyer ID, date of start, and PIN code related to the cardboard. The app then proceeds to invite the person to activate NFC and scan the cardboard. ESET mentioned it discovered NGate getting used in opposition to 3 Czech banks since November and recognized six NGate systems that circulated in mid-March this yr. One of the programs used within the later months of the marketing campaign got here within the type of PWAs, quick for Modern Internet Apps, that have been introduced on Thursday will also be put in on each Android and iOS units even supposing the settings (obligatory on iOS) save you the set up of programs. to be had to non-governmental organizations. The explanation the NGate marketing campaign resulted in March, ESET mentioned, was once the arrest via Czech police of a 22-year-old who they mentioned was once stuck dressed in a masks whilst retreating cash from ATMs in Prague. The investigators mentioned the suspect “deliberate a brand new approach to get cash from other folks” the use of the similar approach as Ngate. Stefanko and fellow ESET researcher Jakub Osmani defined how the assault labored: A press release via the Czech police published that the incident started when the attackers despatched SMS messages to possible sufferers about tax refunds, together with a hyperlink to a fraudulent web page posing as a checking account. Those hyperlinks can have presented malicious PWAs. After the sufferer put in the app and entered their credentials, the attacker accessed the sufferer’s account. The assailant then known as the sufferer, pretending to be a financial institution worker. The sufferer was once informed that their account were compromised, perhaps on account of the preliminary message. The attacker was once telling the reality – the sufferer’s tale was once distorted, however this fact resulted in every other lie. To “offer protection to” their cash, the sufferer was once requested to switch their PIN and check their credit card the use of a cell app – the NGate malware. The obtain hyperlink has been despatched by way of SMS. We suspect that inside the NGate app, sufferers input their outdated PIN to create a brand new one and insert their card into the again of the smartphone to make sure or use the alternate. Because the attacker had get entry to to the compromised account, they had been ready to switch the withdrawal restrict. If the NFC switch approach does now not paintings, they may be able to merely switch the cash to every other account. Then again, the use of NGAte makes it simple for the attacker to get the sufferer’s cash with no need to withdraw it to the attacker’s checking account. A diagram of the assault series is proven in Determine 6.
 Amplify / NGate assault evaluation.ESET The researchers mentioned that NGate or equivalent systems might be used for different functions, akin to developing sensible playing cards which can be used for different functions. The assault would paintings via exploiting the NFC tag’s distinctive ID, abbreviated as UID. “All over the take a look at, we effectively transmitted the UID from the MIFARE Vintage 1K tag, which is used as public delivery tickets, ID badges, club or pupil playing cards, and so forth.,” the researchers wrote. “The usage of NFCGate, it’s conceivable to accomplish an NFC assault to learn the NFC tag in a single position, and, in actual time, you’ll be able to input different puts in keeping with its UID, as proven in Determine 7.”
Amplify / NGate assault evaluation.ESET The researchers mentioned that NGate or equivalent systems might be used for different functions, akin to developing sensible playing cards which can be used for different functions. The assault would paintings via exploiting the NFC tag’s distinctive ID, abbreviated as UID. “All over the take a look at, we effectively transmitted the UID from the MIFARE Vintage 1K tag, which is used as public delivery tickets, ID badges, club or pupil playing cards, and so forth.,” the researchers wrote. “The usage of NFCGate, it’s conceivable to accomplish an NFC assault to learn the NFC tag in a single position, and, in actual time, you’ll be able to input different puts in keeping with its UID, as proven in Determine 7.”
 Amplify / Determine 7. An Android smartphone (proper) that learn and despatched the UID of an exterior NFC tag to every other software (left). Card in unattended baggage, wallets, backpacks, or smartphones that include playing cards. Executing and imitating such assaults calls for the attacker to have an absolutely practical and solid Android software. The telephones captured via Ngate didn’t have this requirement.
Amplify / Determine 7. An Android smartphone (proper) that learn and despatched the UID of an exterior NFC tag to every other software (left). Card in unattended baggage, wallets, backpacks, or smartphones that include playing cards. Executing and imitating such assaults calls for the attacker to have an absolutely practical and solid Android software. The telephones captured via Ngate didn’t have this requirement.








:max_bytes(150000):strip_icc()/GettyImages-2226490793-c5e9f8c574474ef69232a57d4031cedf.jpg)



