Mar 18, 2024 NewsroomCyber Struggle / Malware
A Russian-linked risk actor referred to as APT28 has been related to ongoing phishing campaigns that use misleading paperwork impersonating authorities and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, North and South The us. “The leaked cables come with inner and publicly to be had paperwork, in addition to paperwork that can be created through actors associated with the monetary, infrastructure, main occasions, cyber safety, maritime safety, well being care, trade, and production protection industries,” IBM X -Power mentioned in a document revealed closing week. The generation corporate is following the craze beneath the moniker ITG05, which is often referred to as Blue Athena, BlueDelta, Fancy Endure, Preventing Ursa, Wooded area Snowstorm (previously Strontium), FROZENLAKE, Iron Twilight, Pawn Typhoon, Sednit, Sofacy, TA422, and UAC- 028.

The revelation comes 3 months after the adversary was once noticed the use of deception associated with the continuing Israel-Hamas struggle to supply a again door referred to as HeadLace. APT28 has additionally been focused on Ukrainian authorities businesses and Polish organizations with phishing emails designed to ship recognized implants and id robbery reminiscent of MASEPIE, OCEANMAP, and STEELHOOK. Some campaigns have incorporated exploiting a safety flaw in Microsoft Outlook (CVE-2023-23397, CVSS ranking: 9.8) to thieve NT LAN Supervisor (NTLM) v2 hashes, elevating the likelihood that the attacker may just exploit different vulnerabilities to extract NTLMv2 hashes. for use in opposition to relays.
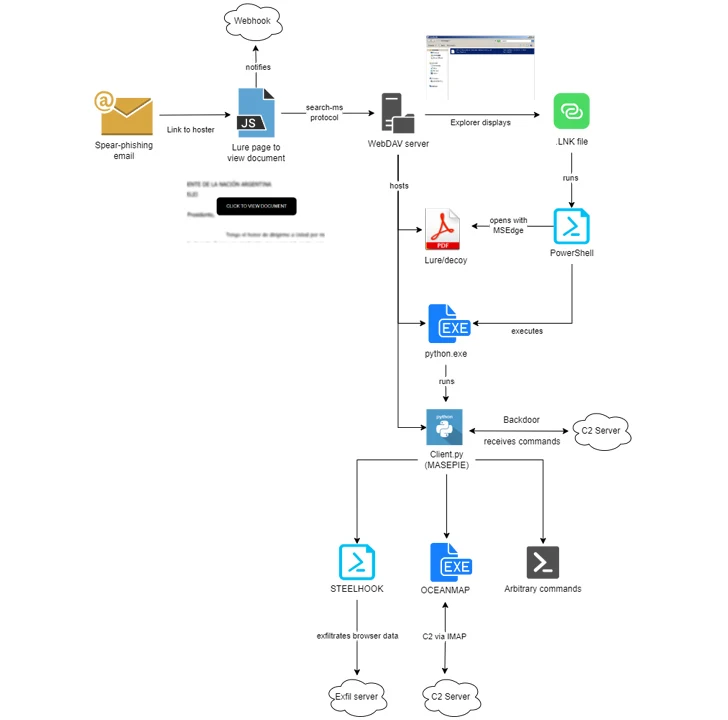
Fresh campaigns through IBM X-Power between the tip of November 2023 and February 2024 enhance the “search-ms:” URI protocol supervisor in Microsoft Home windows to trick sufferers into downloading malware hosted on servers hosted through WebDAV avid gamers. There may be proof that each one WebDAV servers, in addition to MASEPIE C2 servers, might include Ubiquiti routers, a botnet that was once taken down through the United States authorities closing month.

The fraudulent assault objectives organizations from a number of nations reminiscent of Argentina, Ukraine, Georgia, Belarus, Kazakhstan, Poland, Armenia, Azerbaijan, and the United States, the use of a mixture of publicly to be had authorities and non-government paperwork to release the an infection. chain. “By way of converting their strategies, ITG05 is the use of the freely to be had firstcloudit[.]com to arrange bills to stay operations going,” safety researchers Joe Fasulo, Claire Zaboeva, and Golo Mühr mentioned. The climax of the APT28 assault ends with the execution of MASEPIE, OCEANMAP, and STEELHOOK, which can be designed to extract recordsdata, working in unison. oCEANMAP has been recognized that this is a model of CredoMap, which is already recognized for use through the gang. “ITG05 stays in keeping with converting alternatives through providing new diagnostic strategies and the use of advertising and marketing equipment, whilst all the time evolving. liberating the facility of the malware,” the researchers concluded.
Did you to find this newsletter attention-grabbing? Observe us on Twitter and LinkedIn to learn extra of our content material.