
Getty Images According to security firm Mandiant, Ars Technica was recently leveraged to spread a second piece of malware within a campaign using a network that has not been previously documented. As per researchers, a harmless pizza image was uploaded to a third-party site and then linked to a post on an Ars subscriber’s “about” page. The link contained a series of seemingly random characters, concealed within. The campaign also targeted video-sharing site Vimeo, with a malicious video upload and a hidden string within the video’s description, created using Base 64 encoding. This method, which converts text to ASCII string format, was utilized to install a second layer of malware on devices already affected by the campaign.
“This is another and unusual way we’re looking at abuses that are difficult to detect,” said Mandiant researcher Yash Gupta. “This is some of the most malicious software we’ve ever seen. It’s interesting to us and something we wanted to mention.”
The image posted on Ars appeared on the profile of a user who created the account on November 23. An Ars representative mentioned that the image displaying a pizza with the text “I love pizza” was removed by Ars staff on December 16 following a suggestion received via email from an anonymous group. The base 64 encoding was uncovered following the valid URL segment. This string does not cause errors or prevent the page from loading.
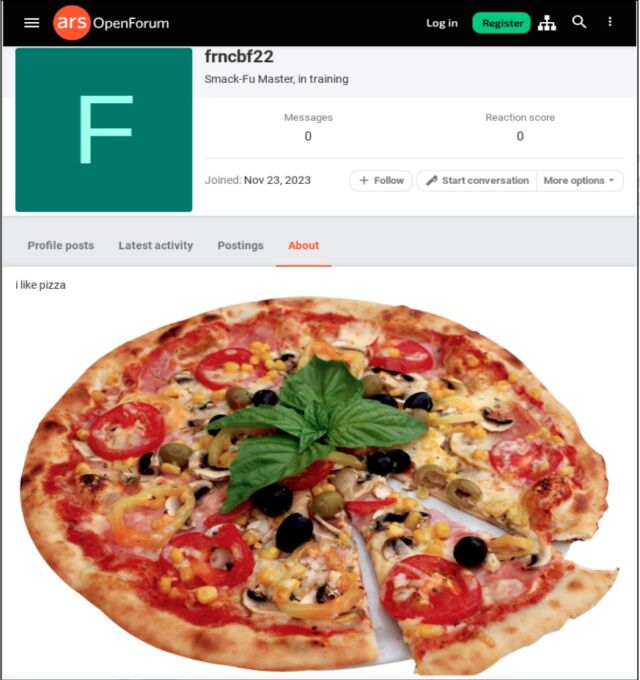 Enlarge / image of Pizza submitted by users.
Enlarge / image of Pizza submitted by users.
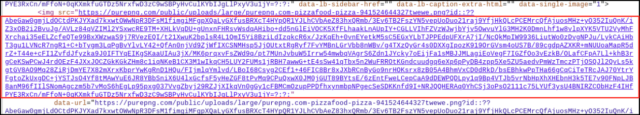 Expand / Malicious String in URL Mandiant researchers stated that there were no known repercussions for individuals who may have viewed the image on the Ars site or on the hosting site. It is also unknown whether Ars users visited the site. The malware only affected the Marketing Tool at the final part of the link, causing it to experience a second stage. The Vimeo video operated in a similar manner, with the string embedded in the video description. Ars representatives had no further comments, while Vimeo representatives did not immediately respond to an email.
Expand / Malicious String in URL Mandiant researchers stated that there were no known repercussions for individuals who may have viewed the image on the Ars site or on the hosting site. It is also unknown whether Ars users visited the site. The malware only affected the Marketing Tool at the final part of the link, causing it to experience a second stage. The Vimeo video operated in a similar manner, with the string embedded in the video description. Ars representatives had no further comments, while Vimeo representatives did not immediately respond to an email.
The campaign is linked to Mandiant’s threat actor UNC4990, which has been active since 2020 and shows signs of motivation and financial gain. The group has previously utilized a different method to remain undetected. The method spread in the second stage using a file that appeared empty to browsers and standard editors. Opening the same file in a hex editor revealed a code made of mixed tabs, spaces, and newlines, arranged in a way that made it executable. The use of such a file related to Ars and Vimeo is a new development, as per Mandiant researchers. Previously, UNC4990 had used Github and Gitlab. The initial phase of the malware was distributed via infected USB drives, which installed a payload named explorerps1. Infected devices would access a malicious file or link posted on Ars or a video on Vimeo. The first 64 strings in the image URL or video description would cause the malware to link to a page containing the second part. The second stage, known as Emptyspace, continuously scanned the command-and-control server, and when instructed, would download and execute the third stage.
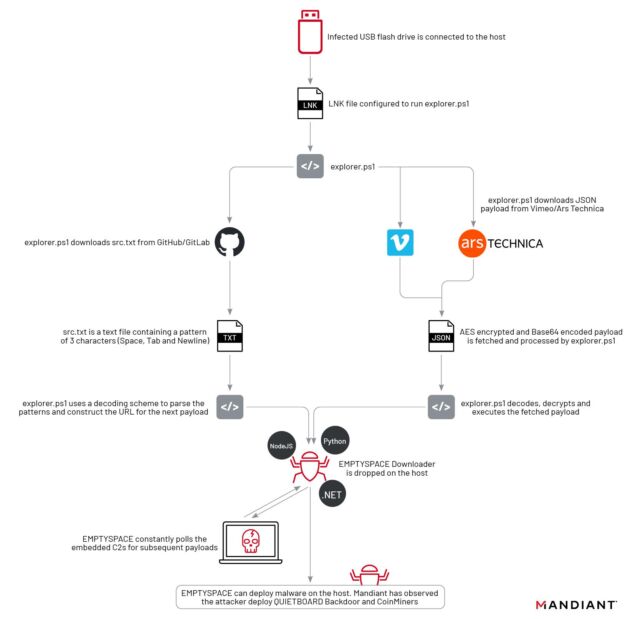 Mandiant Mandiant observed the implementation of this third phase in only one instance. This malware acts as a back door and continues to establish a cryptocurrency mine. Those concerned about being infected with the malware mentioned by Mandiant can look for signs of a compromise in Tuesday’s post.
Mandiant Mandiant observed the implementation of this third phase in only one instance. This malware acts as a back door and continues to establish a cryptocurrency mine. Those concerned about being infected with the malware mentioned by Mandiant can look for signs of a compromise in Tuesday’s post.













