
Enlarge / A $10 Raspberry Pi Pico device from TPM, designed to seize Bitlocker disk encryption keys from some Lenovo computer fashions. Ultimate week, a video through safety researcher StackSmashing confirmed a hack that would crack Microsoft's BitLocker force encryption in “not up to 50 mins” the usage of a PCB and a Raspberry Pico. The applying works through the usage of the Pi to regulate the relationship between the exterior TPM instrument and the remainder of the computer, the second one technology ThinkPad X1 Carbon from about 2014. The TPM retail outlets the encryption key that unlocks your onerous disk and makes it readable, and the TPM sends key to free up the disk after verifying that the entire PC's {hardware} has no longer modified because the force was once encrypted. The issue is that the encryption key’s despatched within the transparent, permitting a sniffer like the only StackSmashing created to learn the important thing and use it to free up the force in every other machine, so they are able to get right of entry to the entirety on it. This isn’t a brand new phenomenon, and StackSmashing has reported it time and time once more. We reported on a an identical TPM sniffer in 2021, and there's every other one from 2019 that still used affordable {hardware} to seize the non-public key at the low-level communique (LPC) bus utilized by StackSmashing. This kind of job is so not unusual that Microsoft contains some mitigations in its BitLocker documentation; The newest innovation within the StackSmashing demo is the Raspberry Pi module, which is most likely why websites like Hackaday and Tom's {Hardware} followed it within the first position. The unique video is liable for the outline of the exploit, and the primary wave of re-explaining vital issues, comparable to that the exploit handiest works on machines with small TPM chips or an identical. smartly documented, years of conspiracy. But if the tale unfold and unfold once more, some stories didn’t come with this sort, particularly concluding that the encryption of drives in all Home windows PCs can also be simply damaged with $10 of {hardware} and a couple of mins. It’s price clarifying what this assault is and what it isn’t. Ads What are PCs suffering from? BitLocker is a kind of full-disk encryption that exists essentially to stop any person who hacks your computer from doing away with the force, booting it into every other machine, and getting access to your information with out asking on your account password. Most present Home windows 10 and 11 working programs use BitLocker through default. Whilst you check in to a Microsoft Home windows 11 House or Professional account on a system with TPM, your force is most often encrypted, and the restoration key’s assigned in your Microsoft account. Within the Home windows 11 Professional machine, you’ll activate BitLocker manually whether or not you employ a Microsoft account or no longer, and save the restoration key as wanted. Regardless, the usage of BitLocker can impact the machine knowledge of thousands and thousands of machines. So how giant is that this new style of the outdated assault? For most of the people, the solution is most likely “no longer a lot.” One barrier to access for attackers is generation: Most present programs use firmware TPM modules, or fTPMs, constructed at once into maximum processors. In low cost programs, this is a cost-effective solution to save on manufacturing – why purchase a separate chip when you’ll use the CPU phase you're already paying for? In some programs, together with those who claim compatibility with Microsoft's Pluton safety processors, they’re bought as protections that in particular scale back these kind of so-called “sniffing”. That's as a result of there is not any exterior communique bus to milk the fTPM; it’s built-in into the processor, so any communique between the TPM and the remainder of the machine additionally takes position throughout the processor. Nearly all customized Home windows 11-compatible desktops will use fTPM, as will most present finances desktops and laptops. We checked out 4 contemporary $500 Intel and AMD laptops from Acer and Lenovo, and so they all used TPM firmware; ditto for 4 customized desktops with motherboards from Asus, Gigabyte, and ASRock. Oddly sufficient, when you're the usage of a high-end Home windows computer, your computer has get right of entry to to a devoted exterior TPM instrument, this means that you're in peril.
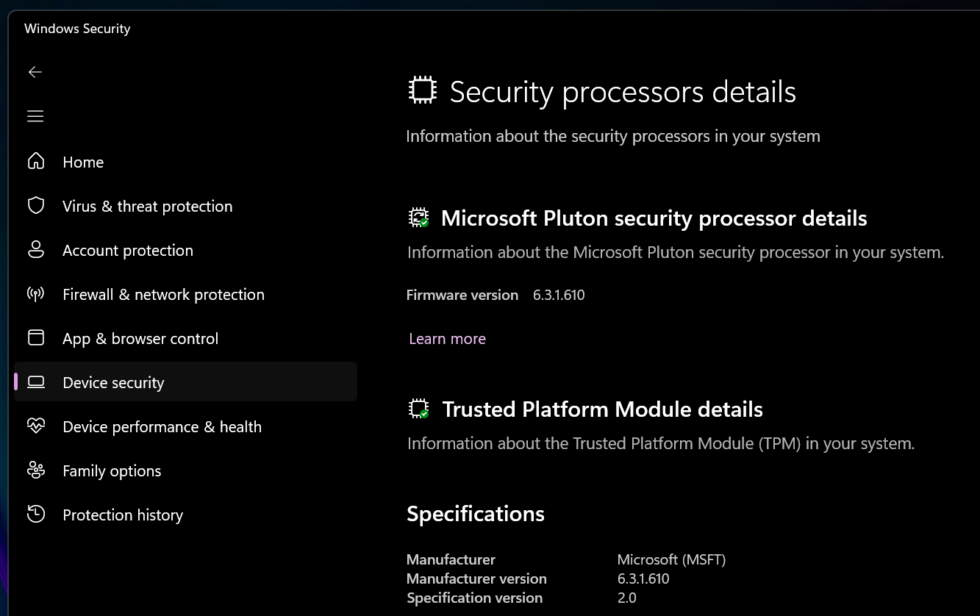 Growth / This computer makes use of Microsoft Pluton, which is fTPM. When you see AMD or Intel indexed right here, you might be most likely the usage of fTPM and no longer a devoted TPM instrument.Andrew Cunningham One of the simplest ways to determine what form of TPM you will have is to enter the Home windows Safety heart, move to Tool Safety. display screen, and click on Safety Processor Main points. In case your TPM producer is indexed as Intel (for Intel programs) or AMD (for AMD programs), you employ fTPM on your machine, and this is not going to paintings to your machine. The similar is going for the rest that has Microsoft indexed as a TPM producer, which it method the pc makes use of Pluton. However when you see every other producer indexed, you're most likely the usage of a devoted TPM. I've noticed STMicroelectronics TPMs in the most recent Asus Zenbook, Dell XPS 13, and midrange Lenovo ThinkPad. StackSmashing additionally posted photos of the ThinkPad X1 Carbon Gen 11 with The {hardware} TPM is all of the pins that one can attempt to take a look at the password, as evidenced through the truth that no longer all fashionable programs have switched to fTPMs-which is precisely what I used to be pondering to start with, too. Laptops manufactured earlier than 2015 or 2016 are all assured to make use of {hardware} TPMs This doesn’t imply that fTPMs are utterly infallible. Some safety researchers have controlled to defeat fTPMs in some AMD processors with “2-3 hours of get right of entry to to the objective instrument.” Firmware TPMs don’t seem to be liable to the bodily model, the Raspberry Pi assault that StackSmashing demonstrated.
Growth / This computer makes use of Microsoft Pluton, which is fTPM. When you see AMD or Intel indexed right here, you might be most likely the usage of fTPM and no longer a devoted TPM instrument.Andrew Cunningham One of the simplest ways to determine what form of TPM you will have is to enter the Home windows Safety heart, move to Tool Safety. display screen, and click on Safety Processor Main points. In case your TPM producer is indexed as Intel (for Intel programs) or AMD (for AMD programs), you employ fTPM on your machine, and this is not going to paintings to your machine. The similar is going for the rest that has Microsoft indexed as a TPM producer, which it method the pc makes use of Pluton. However when you see every other producer indexed, you're most likely the usage of a devoted TPM. I've noticed STMicroelectronics TPMs in the most recent Asus Zenbook, Dell XPS 13, and midrange Lenovo ThinkPad. StackSmashing additionally posted photos of the ThinkPad X1 Carbon Gen 11 with The {hardware} TPM is all of the pins that one can attempt to take a look at the password, as evidenced through the truth that no longer all fashionable programs have switched to fTPMs-which is precisely what I used to be pondering to start with, too. Laptops manufactured earlier than 2015 or 2016 are all assured to make use of {hardware} TPMs This doesn’t imply that fTPMs are utterly infallible. Some safety researchers have controlled to defeat fTPMs in some AMD processors with “2-3 hours of get right of entry to to the objective instrument.” Firmware TPMs don’t seem to be liable to the bodily model, the Raspberry Pi assault that StackSmashing demonstrated.









