Phishing assaults making the most of what seems to be a flaw in Apple's privateness coverage are on the upward push, in keeping with a document via KrebsOnSecurity. Various Apple customers had been coping with tense notifications or multi-factor authentication (MFA) messages to get them to just accept Apple ID password adjustments.
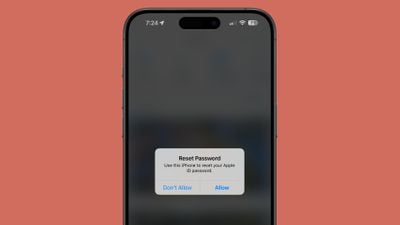
An attacker could cause a goal's iPhone, Apple Watch, or Mac to time and again show a password-change authorization script, in hopes that the objective will mistakenly settle for the request or tire of the notifications and click on. at the settle for button. If the request is accredited, the attacker can exchange the Apple ID password and lock the Apple consumer out in their account. As a result of privateness requests are in response to an Apple ID, they seem on the entire consumer's gadgets. The notifications make all hooked up Apple merchandise unusable till the popups are got rid of separately from each and every software. Twitter consumer Parth Patel just lately shared his revel in with the assault, and says he may now not use his gadgets till he clicked “Don’t permit” on greater than 100 notifications. When attackers fail to get the consumer to click on “Permit” on password exchange notifications, the objectives steadily make telephone calls that seem if they’re from Apple. In those calls, the attacker claims to grasp that the sufferer is being attacked, and makes an attempt to procure the password this is despatched to the consumer's telephone quantity in an try to exchange the password. In Patel's case, the attacker used data leaked from a public seek web site, which incorporated title, present deal with, earlier deal with, and contact quantity, giving the attacker get admission to to his account data to make use of. The attacker's title was once unsuitable, and he changed into suspicious as a result of he was once requested for a one-time code that Apple obviously sends with a affirmation message that Apple doesn't ask for the ones codes. The assault seems to be in response to the attacker having the ability to get admission to the e-mail deal with and contact quantity related to the Apple ID. KrebsOnSecurity seemed into the topic, and located that the attackers appear to be the usage of Apple's site to disregard their Apple ID password. This web page calls for an Apple ID e-mail or telephone quantity, and incorporates a CAPTCHA. When an e-mail is entered, the web site shows the remaining two digits of the telephone quantity related to the Apple account, and typing within the lacking digits and hitting ship sends a caution. It’s not transparent how the attackers are abusing the program to ship a couple of messages to Apple customers, however it sort of feels like a malicious program is being exploited. It’s not likely that Apple's device must be used to ship greater than 100 requests, so most likely the restrict is being bypassed. Apple software homeowners who’re centered via this sort must you should definitely kind “Do No longer Permit” on all requests, and must remember that Apple won’t name to request a one-time password reset quantity.
Caution: Apple Customers Centered in Complicated Phishing Assault Involving Password Reset Requests