A brand new Linux port referred to as ‘WolfsBane’ has been found out, which is assumed to be a port of Home windows malware utilized by the Chinese language hacking staff ‘Gelsemium’. ESET safety researchers who analyzed WolfsBane reported that WolfsBane is a whole malware device that features a downloader, launcher, and backdoor, whilst additionally the use of an open supply rootkit to steer clear of detection. The researchers additionally discovered ‘FireWood,’ some other Linux malware that seems to be connected to the ‘Venture Wooden’ Home windows malware. On the other hand, FireWood is a shared device utilized by a number of Chinese language APT teams reasonably than a proprietary/personal device advanced through Gelsemium. ESET says the 2 malware households, which seemed on VirusTotal closing yr, are a part of a rising development of APT teams concentrated on Linux platforms as Home windows safety continues to enlarge. “The craze of APT teams that specialize in Linux malware is turning into extra obvious. We imagine that this transformation is because of adjustments in Home windows e-mail and endpoint safety, such because the unfold of end-point detection gear (EDR) and Microsoft’s resolution to dam Visible. Fundamental for Programs (VBA) random macros Due to this fact, attackers are in search of new strategies of assault, and are that specialize in exploiting the Web. methods, lots of which run on Linux.” ❖ ESET WolfsBane’s stealthy howl WolfsBane is presented on goal by way of a dropper referred to as ‘cron,’ which drops a program startup module disguised as a part of the KDE desktop. Relying at the privilege that includes it, it disables SELinux, creates gadget recordsdata, or adjustments person configuration recordsdata to set patience. The launcher carries the name of the game of the malware, ‘udevd,’ which rather a lot 3 hidden libraries that include its personal capability and management and management (C2) verbal exchange.
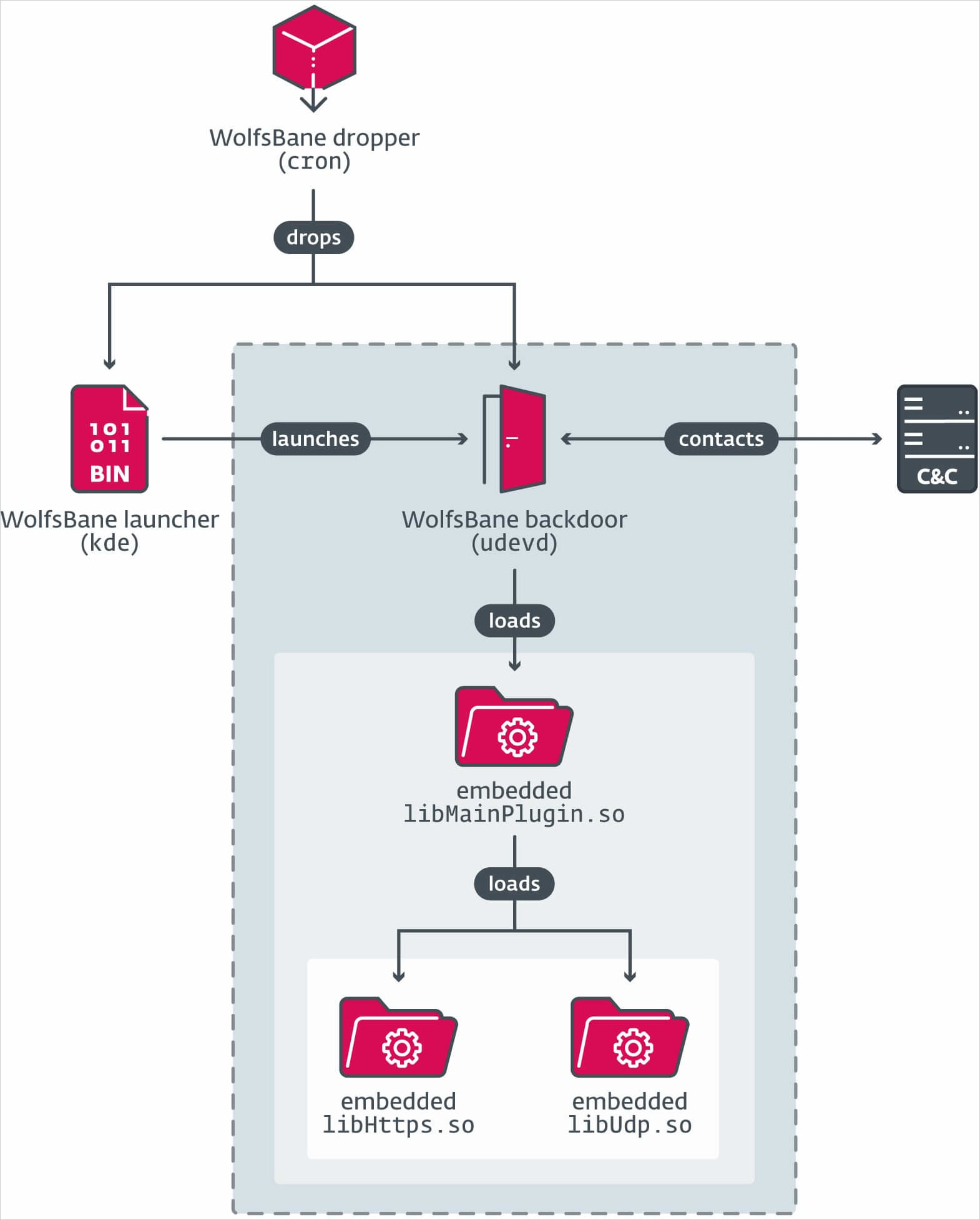 WolfsBane unlock
WolfsBane unlock
Supply: ESET In any case, a changed model of the BEURK userland rootkit is loaded by way of ‘/and so on/ld.so.preload’ to cover paths, recordsdata, and community visitors associated with WolfsBane’s actions. “WolfsBane Hider rootkit connects to many C library purposes corresponding to open, stat, readdir, and get entry to,” explains ESET. “Whilst this draws startups, it filters out any effects associated with the WolfsBane malware.” The primary activity of WolfsBane is to put in force the instructions won from the C2 server the use of a predefined map, which is identical manner used on Home windows. Those regulations come with record methods, knowledge extraction, and gadget adjustments, giving Gelsemium whole management over the gadget’s complexity.
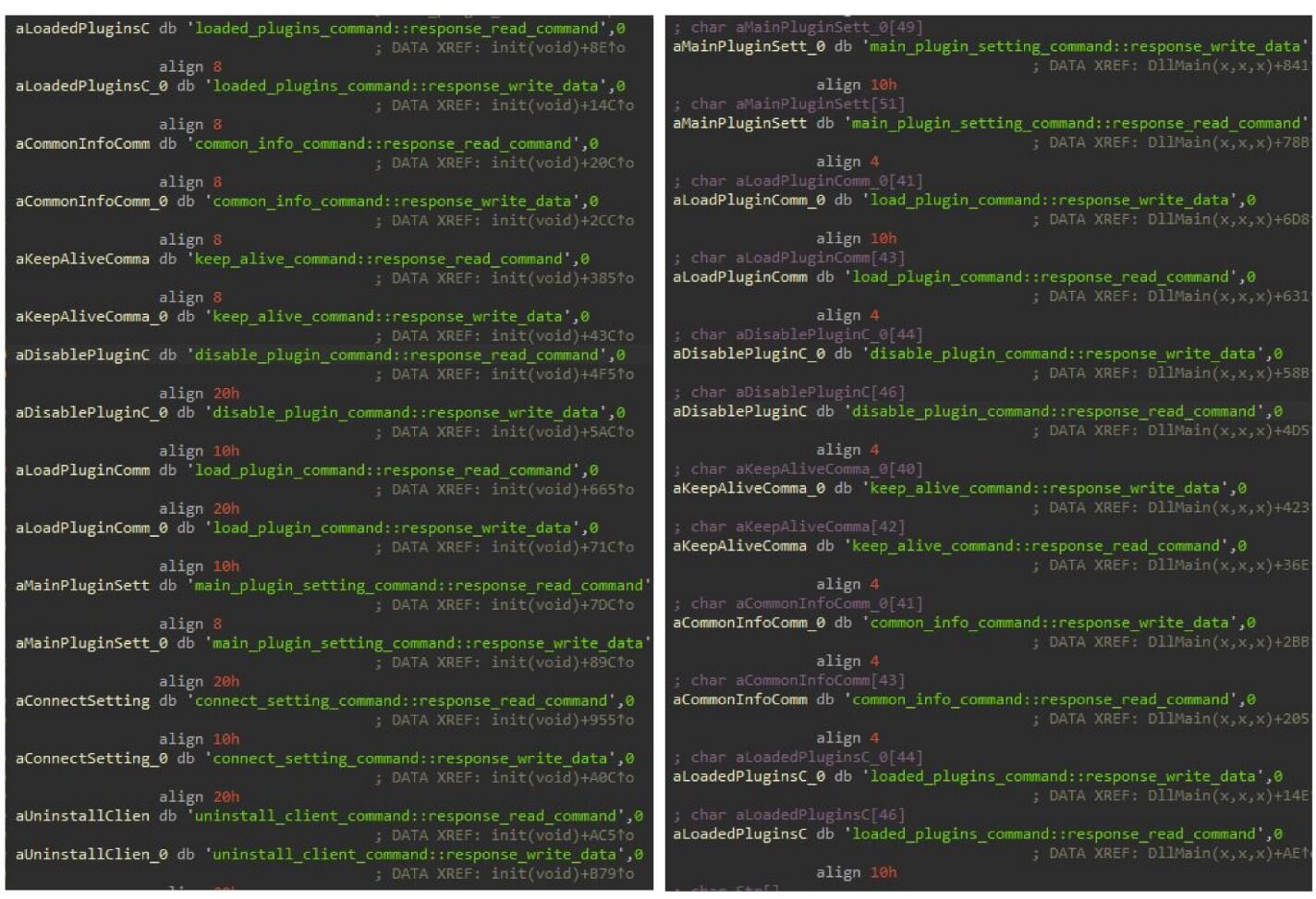 Command names for Linux (left) and Home windows backdoors (proper)
Command names for Linux (left) and Home windows backdoors (proper)
Supply: ESET Even if loosely connected to Gelsemium, FireWood is some other Linux house that may run a long-term espionage marketing campaign. Its built-in features permit customers to accomplish record operations, command shell instructions, load/sell off libraries, and extract knowledge. ESET has known a record named ‘usbdev.ko,’ which is believed to behave as a kernel-level rootkit, which supplies FireWood the facility to cover processes. The malware installs its patience at the host through growing an autostart record (gnome-control.desktop) in ‘.config/autostart/,’ the place it will possibly additionally come with instructions on this record to execute routinely at device startup. A whole listing of unrelated signs for the 2 new Linux malware households and the most recent Gelsemium campaigns is to be had on this GitHub repository.