Normally, Safety Coverage prevents UEFI from working all next recordsdata except they’ve a virtual signature to end up that the recordsdata are depended on by means of the tool producer. The exploit bypasses this safety by means of putting a hidden shell code right into a malicious bitmap symbol displayed by means of UEFI throughout boot. The extracted code embeds a cryptographic key that indicators the malicious GRUB document together with a background symbol of the Linux kernel, either one of which run throughout the preliminary startup segment of the Linux gadget. Silently surroundings this key reasons UEFI to regard the malicious GRUB and kernel symbol as depended on units, bypassing the Safety Boot coverage. The general result’s a backdoor that used to be constructed into the Linux kernel earlier than some other safety features had been applied.
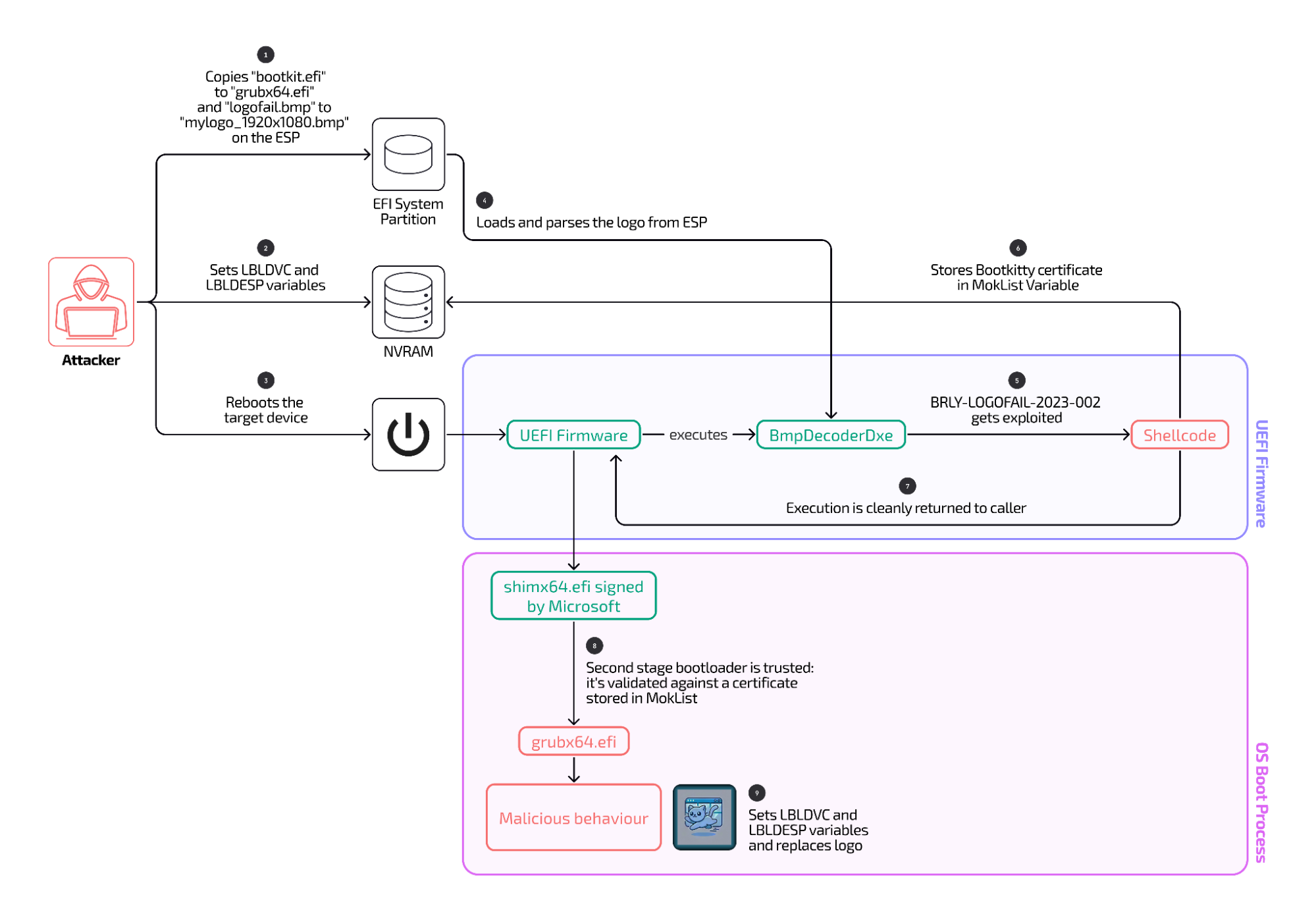
A diagram appearing the stairs of the LogoFAIL exploit Binary discovered within the wild. Credit score: Binarly In an internet interview, HD Moore, CTO and co-founder at runZero and knowledgeable on firmware-based malware, described Binarly’s document as follows: . it bypasses protected boot (firmware) by means of tricking the firmware into accepting their self-signing key (which is saved within the firmware because the MOK variable). The malicious code remains to be restricted to UEFI customers, however using LogoFAIL lets them upload their signature keys to the firmware’s whitelist (however does now not distribute the firmware another way). It is nonetheless a GRUB-based kernel backdoor as opposed to a firmware backdoor, however it makes use of a firmware error (LogoFAIL) to permit set up with out consumer interplay (registration, reboot, and accepting a brand new MOK signing key). In a regular boot setup, the administrator creates a neighborhood key, makes use of this to signal their kernel/GRUB bundle, tells the firmware to sign up the important thing they created, then after a reboot, the administrator will have to settle for the brand new key by the use of the console. (or remotely by the use of bmc/ipmi/ilo/drac/and many others bios console). On this setup, the attacker can change the usual GRUB+ kernel with a backend model by means of registering their very own signing key with out the usage of the LogoFAIL manner, however it’s nonetheless a GRUB-based bootkit, and isn’t strong. BIOS firmware or no matter. Prone machines come with fashions bought by means of Acer, HP, Fujitsu, and Lenovo that send with UEFI evolved by means of developer Insyde and run Linux. Proof discovered within the exploit code means that exploits will also be evolved for different {hardware} configurations of such techniques. Insyde issued a patch previous this 12 months that stops the app from operating. Unsigned units stay prone. Gadgets from those producers that use non-Insyde UEFIs aren’t affected.