Getty Photographs researchers have came upon greater than 280 malicious Android apps that use facial reputation to thieve cryptocurrency wallets from inflamed units. Those techniques seem to be applicable from banks, executive products and services, TV viewing products and services, and utilities. As an alternative, they scan inflamed telephones for all saved textual content messages, textual content messages, and pictures and secretly ship them to faraway servers managed by way of tool builders. Those techniques are bought from malicious web sites and dispensed in fraudulent messages despatched to goals. There is not any indication that any apps had been to be had via Google Play. The most typical characteristic of the newly came upon malware marketing campaign is that the risk actors are the use of trend reputation tool in an try to extract cryptocurrency wallets displayed on pictures saved on inflamed units. Many wallets permit customers to offer protection to their wallets with a random choice of phrases. Mnemonic symbols are more uncomplicated for most of the people to bear in mind than the jumble of letters that seem on this secret park. Phrases also are more uncomplicated for other folks to acknowledge in photos. SangRyol Ryu, a researcher at safety company McAfee, came upon this after gaining unauthorized get admission to to servers that won knowledge stolen by way of malicious tool. That get admission to was once because of a susceptible safety configuration that the servers had been deployed on. With this, Ryu was once ready to learn the pages to be had to the server directors. One web page, proven within the symbol under, was once specifically fascinating. It displayed an inventory of phrases close to the highest and a corresponding symbol, taken from an inflamed telephone, under. The phrases proven within the image are very similar to the similar phrases.
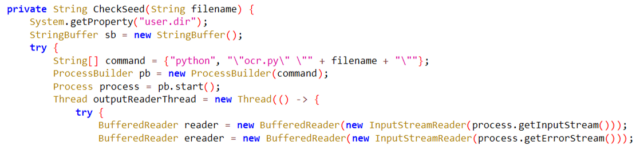 Magnify / Python code for changing textual content displayed on a display screen into machine-readable textual content.McAfee People who find themselves involved that they are going to have put in any such malicious techniques will have to test McAfee’s submit for an inventory of related web sites and cryptographic hashes. The crime program has won a number of updates over the years. Whilst it used to make use of HTTP to keep in touch with keep an eye on servers, it now communicates by the use of WebSockets, one way that is more challenging for safety tool to intercept. WebSockets have the additional advantage of being a versatile medium.
Magnify / Python code for changing textual content displayed on a display screen into machine-readable textual content.McAfee People who find themselves involved that they are going to have put in any such malicious techniques will have to test McAfee’s submit for an inventory of related web sites and cryptographic hashes. The crime program has won a number of updates over the years. Whilst it used to make use of HTTP to keep in touch with keep an eye on servers, it now communicates by the use of WebSockets, one way that is more challenging for safety tool to intercept. WebSockets have the additional advantage of being a versatile medium.
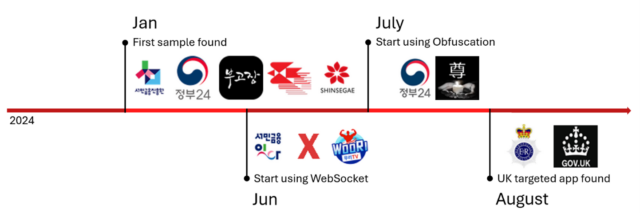 Magnify / A timeline of apps’ evolution. McAfee builders have additionally changed those apps to thwart their malicious actions. Obfuscation ways come with striking strings inside of code to cause them to much less readable by way of people, including pointless code, and refactoring purposes and adjustments, all of which confuse professionals and make detection tough. Even supposing the malware is restricted to South Korea, it has just lately unfold to the United Kingdom. “This building is vital as it displays that risk actors are expanding their focal point on knowledge and house,” Ryu wrote. “The transfer to the United Kingdom displays a planned try by way of the risk actors to enlarge their operations, perhaps the objective of latest malware teams.”
Magnify / A timeline of apps’ evolution. McAfee builders have additionally changed those apps to thwart their malicious actions. Obfuscation ways come with striking strings inside of code to cause them to much less readable by way of people, including pointless code, and refactoring purposes and adjustments, all of which confuse professionals and make detection tough. Even supposing the malware is restricted to South Korea, it has just lately unfold to the United Kingdom. “This building is vital as it displays that risk actors are expanding their focal point on knowledge and house,” Ryu wrote. “The transfer to the United Kingdom displays a planned try by way of the risk actors to enlarge their operations, perhaps the objective of latest malware teams.”