
Getty Photographs The United States Cybersecurity and Infrastructure Safety Company has added a big safety vulnerability in Linux to its record of vulnerabilities recognized to be exploited within the wild. The vulnerability, which is coded as CVE-2024-1086 and has a 7.8 out of 10 conceivable, lets in individuals who have already logged into the affected device to extend their get entry to. It’s the results of a later use error, a category of vulnerability that happens in techniques written within the C and C++ languages when a technique continues to get entry to reminiscence after it’s been launched or offered. A post-freeware crash would possibly lead to far off code or larger privilege. The vulnerability, which impacts Linux kernel variations 5.14 to six.6, is living in NF_tables, a kernel module that helps Netfilter, which helps more than a few purposes, together with packet filtering, community cope with. [and port] translation (NA[P]T), slicing on packets, consumer packet queues, and shedding different packets. It was once up to date in January, however as CISA recommendation displays, some producers nonetheless haven't put in it. On the time of this Ars submit, there was once little recognized concerning the alleged rape. Commercial A radical write-up of the vulnerability means that this gives “the most important vintage with out duality the place the precise strategies were hit.” Double unfastened assaults are a subset of runtime mistakes that happen when the unfastened() serve as to unfastened reminiscence is named greater than as soon as on the similar location. The report lists a number of techniques to search out the vulnerability, together with the code to take action. The double unfastened error is because of the failure to fulfill the entries within the netfilter statements when nf_tables and the non-utilized fields are opened. Some complicated exploits permit killing code within the kernel and will also be designed to crash all of the root shell. The creator equipped the next symbol to offer a conceptual review:
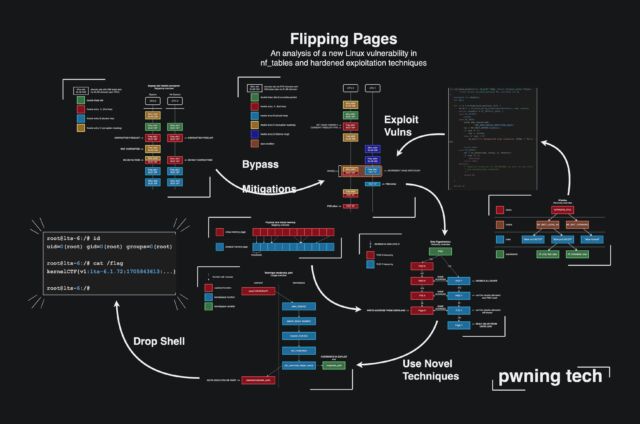 pwning tech CISA has given executive businesses beneath its jurisdiction till June 20 to factor a patch. The company urges all organizations that experience no longer but applied the up to date device to take action once conceivable.
pwning tech CISA has given executive businesses beneath its jurisdiction till June 20 to factor a patch. The company urges all organizations that experience no longer but applied the up to date device to take action once conceivable.













