Might 19, 2024 NewsroomBanking Troja / E mail Safety
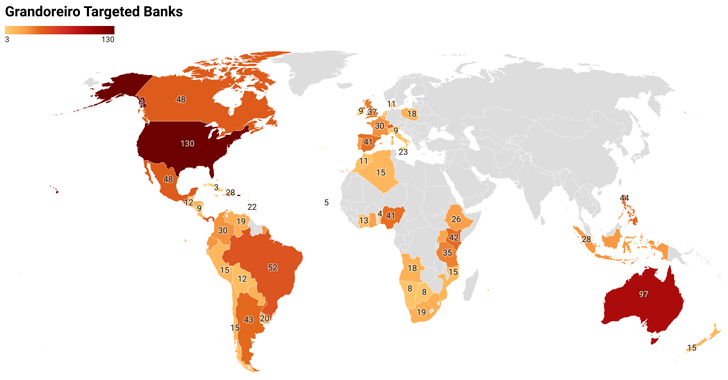
The attackers in the back of the Home windows-based Grandoreiro banking trojan are again in a world marketing campaign from March 2024 following the removing of the foundations in January. The huge fraud assaults, most likely performed via different cybercriminals the usage of malware-as-a-service (MaaS), focused greater than 1,500 banks international, happening in additional than 60 international locations in Central and South The us, Africa, Europe, and the Indo-Pacific, IBM X-Power mentioned. Even though Grandoreiro is understood to concentrate on Latin The us, Spain, and Portugal, the growth needed to trade direction after makes an attempt to near the development via the Brazilian government. Going hand in hand with the rising pattern is the greater management of the malware itself, which presentations a gentle construction.

“The research of the malware printed important adjustments inside the string obtain and extraction set of rules (DGA), in addition to the facility to make use of Microsoft Outlook shoppers at the inflamed to unfold different fraudulent emails,” safety researchers Golo Mühr and Melissa Frydrych mentioned. The assault starts with phishing emails that advise recipients that they have got clicked on a hyperlink to view an bill or make a fee relying at the nature of the bait and the federal government company receiving the messages.
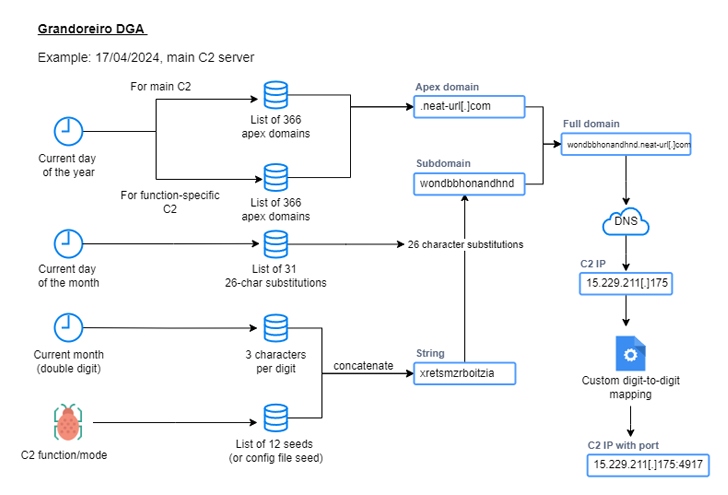
Customers who finally end up clicking at the hyperlink are redirected to the PDF symbol record, which results in the obtain of the ZIP archive that the Grandoreiro loader will execute. The recording record is uploaded to over 100 MB to avoid anti-malware tool. It is usually answerable for making sure that the host isn’t in a sandbox, accumulating the important knowledge for the command-and-control (C2) server, and downloading and putting in the primary trojan. It’s value bringing up that the verification procedure may be carried out to avoid techniques shipped to Russia, Czechia, Poland, and the Netherlands, in addition to Home windows 7 techniques situated in america with out antivirus put in. The trojan part begins running via putting in place patience in the course of the Home windows Registry, and then it makes use of the DGA replace to ascertain connections with the C2 server to obtain different directions.

Grandoreiro helps numerous instructions that let attackers to remotely observe the device, carry out record operations, and management particular options, together with a brand new function that collects Microsoft Outlook knowledge and abuses the sufferer's e-mail account to blast junk mail messages to different objectives. “To hook up with the usual Outlook shopper, Grandoreiro makes use of the Outlook Safety Supervisor software, a program used to create add-ons for Outlook,” the researchers mentioned. “The principle explanation why for that is that Outlook Object Style Guard triggers safety signals if it features get entry to to safe items.”
“Via the usage of the usual Outlook shopper to ship junk mail, Grandoreiro is in a position to unfold via inflamed e-mail inboxes, contributing to the prime quantity of junk mail that Grandoreiro receives.”
Did you to find this newsletter attention-grabbing? Apply us on Twitter and LinkedIn to learn extra of our content material.







:max_bytes(150000):strip_icc()/GettyImages-22249455902-f07fac1ef5484fa0a84d6b3c03094667.jpg)



![Pixel 10 Professional Fold leaks in official-looking renders with most effective Google’s two highest Professional colours [Gallery] Pixel 10 Professional Fold leaks in official-looking renders with most effective Google’s two highest Professional colours [Gallery]](https://9to5google.com/wp-content/uploads/sites/4/2025/07/Pixel-10-Pro-Fold-render-leak-header.jpg?quality=82&strip=all&w=1400)

