In a nutshell: CovertNetwork-1658 is a formidable reminder of the continuing cat-and-mouse sport between cyber safety professionals and risk actors. The usage of compromised gadgets as a part of a botnet additionally underscores the want to safe IoT gadgets and replace firmware on routers and different community gadgets. Microsoft has published a posh community of compromised equipment that Chinese language hackers are the usage of to release privateness assaults on Microsoft Azure consumers. This community, named CovertNetwork-1658 by way of Microsoft, has been stealing data from a number of Microsoft consumers since August 2023. The assaults use small house place of work (SOHO) routers, cameras, and different gadgets. attached to the Web. At its height, there have been greater than 16,000 gadgets within the botnet, maximum of which have been TP-Hyperlink routers. CovertNetwork-1658, often referred to as xlogin and Quad7 (7777), is thought to had been introduced and maintained by way of a risk actor based totally in China. The title of the community is derived from Microsoft’s classification machine, the place “CovertNetwork” refers to a selection of egress IPs with obfuscation or leasing equipment that can be utilized by way of a number of attackers.
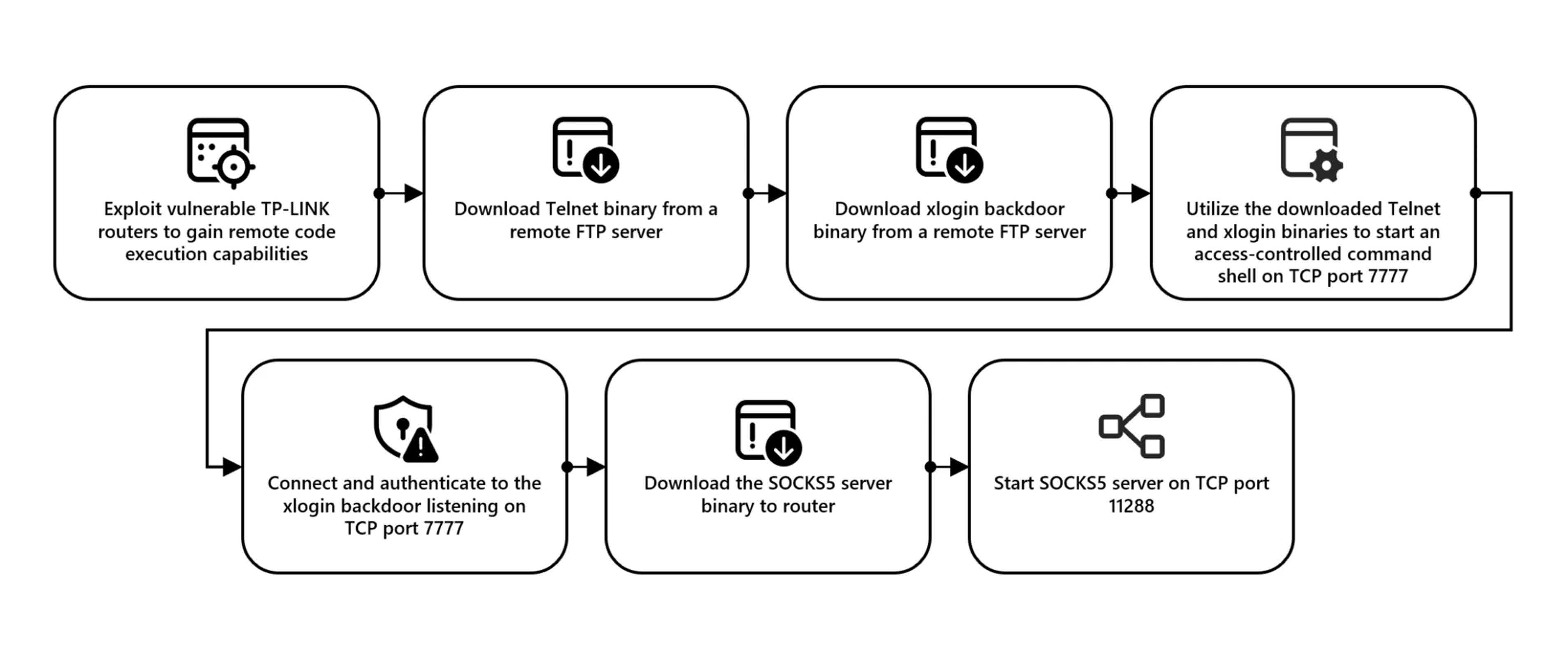
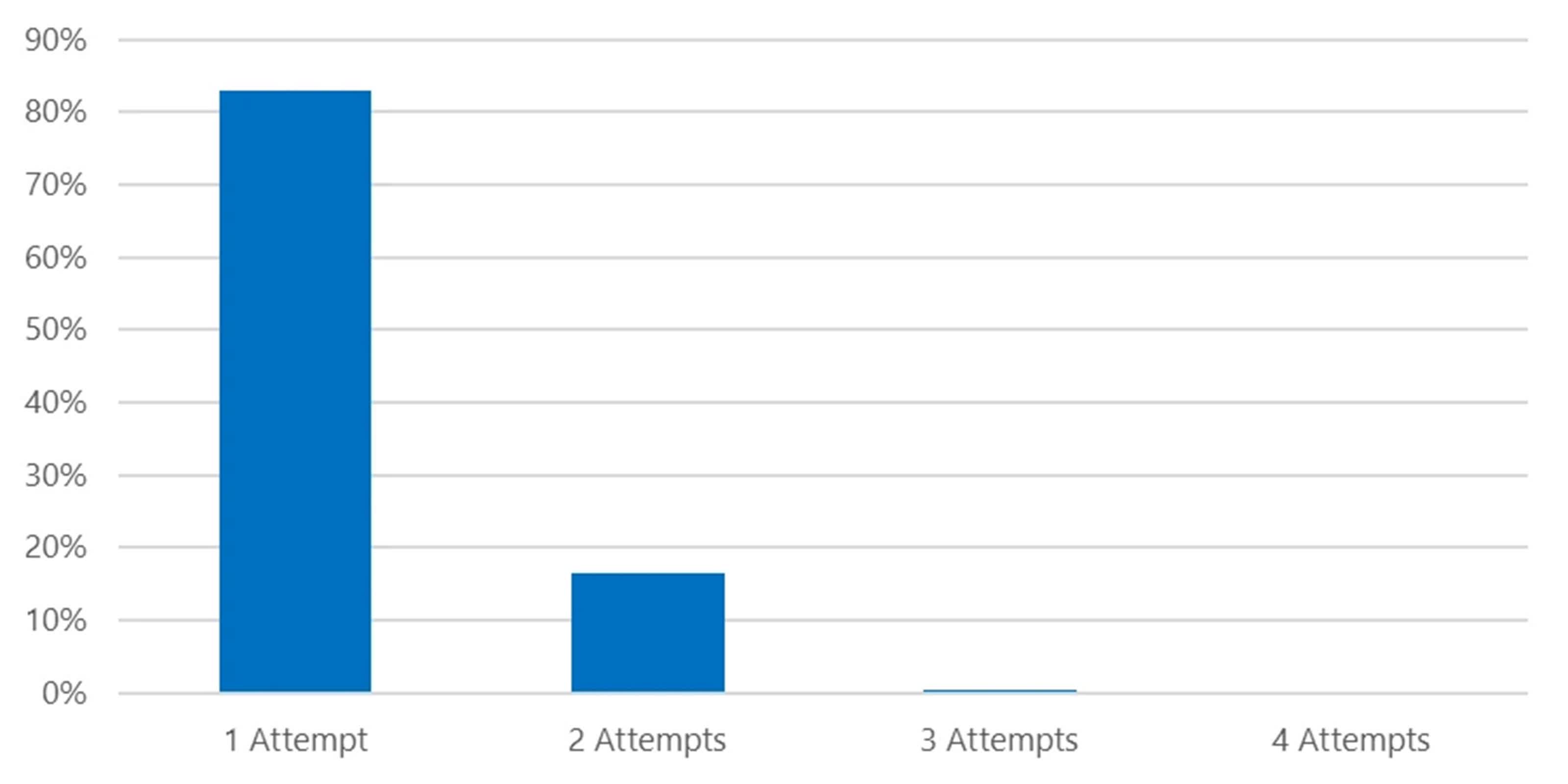
Hackers profit from vulnerabilities in routers to execute faraway code, even if the precise manner of use is being investigated. To succeed in this, attackers take a number of steps to organize a router for a secret injection operation. This comprises downloading Telnet and xlogin backdoor binaries from a faraway Document Switch Protocol (FTP) server, beginning a privilege-controlled shell on TCP port 7777, and putting in place a SOCKS5 server on TCP port 11288. CovertNetwork-1658 may be very stealthy, making it extraordinarily unhealthy. . Password spraying assaults are performed thru a proxy community, making sure that the makes an attempt originate from compromised gadgets. In about 80 p.c of instances, CovertNetwork-1658 simplest makes an attempt to log into one account in line with day, making it tricky to locate the usage of conventional safety features.
The community additionally makes use of SOHO IP addresses, spherical IP addresses, and a low-level password injection machine. On reasonable, Microsoft has observed about 8,000 compromised gadgets operating with the CovertNetwork-1658 community at any given time, and about 20 p.c of those gadgets use passwords. Microsoft has connected the supply of those privateness threats to a number of Chinese language threats. Specifically, a bunch referred to as Typhoon-0940 has been noticed the usage of data bought from CovertNetwork-1658. The connection between CovertNetwork-1658 and Typhoon-0940 seems to be shut, as Microsoft seen Typhoon-0940 the usage of compromised data bought from CovertNetwork-1658 at the identical day. When Typhoon-0940 reveals a spot {that a} sufferer makes use of, it makes use of quite a lot of the way to develop. This comprises logging and detection equipment to navigate the community, looking for community gadgets and set up venture equipment and faraway get entry to trojans (RATs) to persist, and seeking to extract information. The size of the operation is especially relating to, since any individual threatening CovertNetwork-1658 customers can behavior a large-scale password spraying marketing campaign. This, mixed with the top quantity of compromised data between CovertNetwork-1658 and the Chinese language risk actors, implies that accounts can also be briefly compromised in a couple of domain names and geographies. Despite the fact that fresh experiences from safety distributors like Sekoia and Group Cymru have resulted in a lower in the usage of the unique CovertNetwork-1658 gadgets, Microsoft believes that the community remains to be energetic and that attackers can in finding new gadgets with changed keys to steer clear of detection. Microsoft has without delay notified consumers who’ve been centered or compromised. Despite the fact that Redmond didn’t supply explicit recommendation on how customers of TP-Hyperlink routers and different affected gadgets can save you or locate infections, some professionals say that restarting those gadgets once in a while can quickly kill the virus.













