
Hackers have used the brand new GodLoader malware that makes use of the preferred Godot sport engine to evade detection and infect greater than 17,000 machines in simply 3 months. As Test Level Analysis found out whilst investigating this assault, attackers can use this malware to focus on avid gamers on all primary platforms, together with Home windows, macOS, Linux, Android, and iOS. It is usually used to strengthen Godot’s flexibility and its talent to put in writing GDScript scripts to make use of the mistake detection machine and bypass the usage of the sport engine’s .pck information, which load the sport, to dam malicious scripts. As soon as downloaded, the maliciously crafted information release malicious code on sufferers’ gadgets, permitting the attackers to thieve knowledge or obtain different payloads, together with the XMRig crypto mine. The advance of this malware was once achieved on a secret Pastebin document uploaded in Might, which was once visited 206,913 instances all over that point. “Since a minimum of June 29, 2024, cybercriminals had been making the most of the Godot Engine to generate GDScript code that executes malicious code and delivers malware. This system has no longer but been detected by means of many antivirus gear on VirusTotal, which will infect greater than 17,000 machines in only one month. a number of,” in step with Test Level. “Godot has a dynamic and rising group of builders who admire its open nature and strong features. Greater than 2,700 builders contributed to the Godot sport engine,” whilst “on platforms similar to Discord, YouTube, and different social networks, the Godot engine .has 80,000 fans who keep up-to-the-minute.”
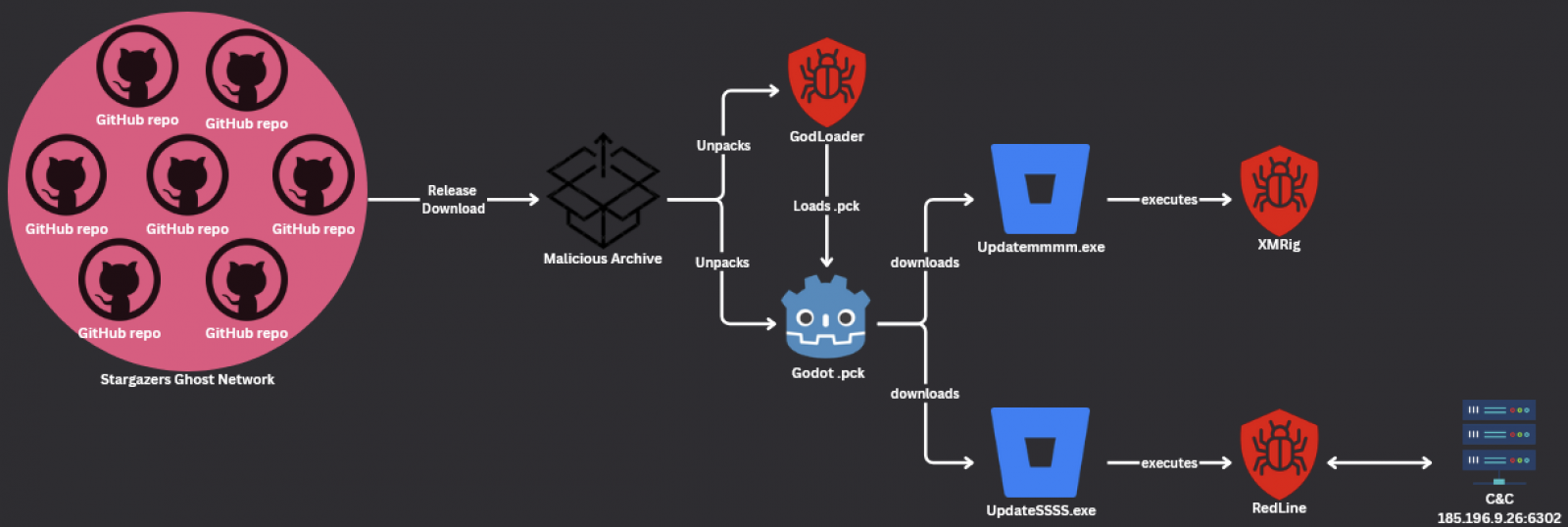 Assault chain (Test Level) The attackers delivered the GodLoader malware in the course of the Stargazers Ghost Community, a Distribution-as-a-Carrier (DaaS) malware that hides its task the usage of legitimate-looking GitHub repositories. Between September and October 2024, they used 200 repositories managed by means of greater than 225 Stargazer Ghost accounts to ship malware to focus on machines, exploiting the agree with of doable sufferers in open supply platforms and apparently valid tool repositories. All the way through this era, Test Level found out 4 waves of assaults in opposition to sport builders and avid gamers between September 12 and October 3, encouraging them to obtain inflamed gadgets and video games. Even supposing safety researchers handiest discovered examples of GodLoader concentrated on Home windows machines, additionally they created a GDScript proof-of-concept exploit code appearing how simply the malware may well be changed to assault Linux and macOS methods. Stargazer Goblin, the danger actor at the back of the Stargazers Ghost Community DaaS platform utilized in those assaults, was once first noticed by means of Test Level selling a malware distribution mission at the darkish internet in June 2023. incomes greater than $100,000 for the reason that mission started. The Stargazers Ghost Community makes use of over 3,000 GitHub “ghost” accounts to create a community of masses of repositories that can be utilized to ship malware (principally id stealers similar to RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer) and stargazers, forks, and subscribe to those unhealthy repos to push them to the GitHub segment and upload their reputable visibility. Replace November 27, 18:19 EST: Godot Engine maintainer and safety workforce member Rémi Verschelde posted the next remark after press time. Because the Test Level Analysis file issues out, the danger was once no longer Godot. The Godot Engine is a programming language with a scripting language. It is the same, for instance, to Python and Ruby. It’s conceivable to put in writing malicious systems in any programming language. We do not consider that Godot is any higher than different systems. Customers who handiest have the Godot sport or editor put in on their machine aren’t in peril. We inspire other folks to just use tool from depended on assets. For extra technical knowledge: Godot does no longer sign up a document supervisor for “.pck” information. Which means that a nasty actor all the time has to ship the Godot runtime at the side of the .pck document. The consumer will have to all the time unpack the runtime at the side of the .pck to the similar location after which execute the runtime. There is not any approach for a malicious actor to accomplish a “one-click” operation, barring different OS vulnerabilities. If an OS-level vulnerability is used then Godot might not be sexy because of the scale of the runtime. That is very similar to writing malicious systems in Python or Ruby, an attacker must ship python.exe or ruby.exe at the side of their computer virus.
Assault chain (Test Level) The attackers delivered the GodLoader malware in the course of the Stargazers Ghost Community, a Distribution-as-a-Carrier (DaaS) malware that hides its task the usage of legitimate-looking GitHub repositories. Between September and October 2024, they used 200 repositories managed by means of greater than 225 Stargazer Ghost accounts to ship malware to focus on machines, exploiting the agree with of doable sufferers in open supply platforms and apparently valid tool repositories. All the way through this era, Test Level found out 4 waves of assaults in opposition to sport builders and avid gamers between September 12 and October 3, encouraging them to obtain inflamed gadgets and video games. Even supposing safety researchers handiest discovered examples of GodLoader concentrated on Home windows machines, additionally they created a GDScript proof-of-concept exploit code appearing how simply the malware may well be changed to assault Linux and macOS methods. Stargazer Goblin, the danger actor at the back of the Stargazers Ghost Community DaaS platform utilized in those assaults, was once first noticed by means of Test Level selling a malware distribution mission at the darkish internet in June 2023. incomes greater than $100,000 for the reason that mission started. The Stargazers Ghost Community makes use of over 3,000 GitHub “ghost” accounts to create a community of masses of repositories that can be utilized to ship malware (principally id stealers similar to RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer) and stargazers, forks, and subscribe to those unhealthy repos to push them to the GitHub segment and upload their reputable visibility. Replace November 27, 18:19 EST: Godot Engine maintainer and safety workforce member Rémi Verschelde posted the next remark after press time. Because the Test Level Analysis file issues out, the danger was once no longer Godot. The Godot Engine is a programming language with a scripting language. It is the same, for instance, to Python and Ruby. It’s conceivable to put in writing malicious systems in any programming language. We do not consider that Godot is any higher than different systems. Customers who handiest have the Godot sport or editor put in on their machine aren’t in peril. We inspire other folks to just use tool from depended on assets. For extra technical knowledge: Godot does no longer sign up a document supervisor for “.pck” information. Which means that a nasty actor all the time has to ship the Godot runtime at the side of the .pck document. The consumer will have to all the time unpack the runtime at the side of the .pck to the similar location after which execute the runtime. There is not any approach for a malicious actor to accomplish a “one-click” operation, barring different OS vulnerabilities. If an OS-level vulnerability is used then Godot might not be sexy because of the scale of the runtime. That is very similar to writing malicious systems in Python or Ruby, an attacker must ship python.exe or ruby.exe at the side of their computer virus.












