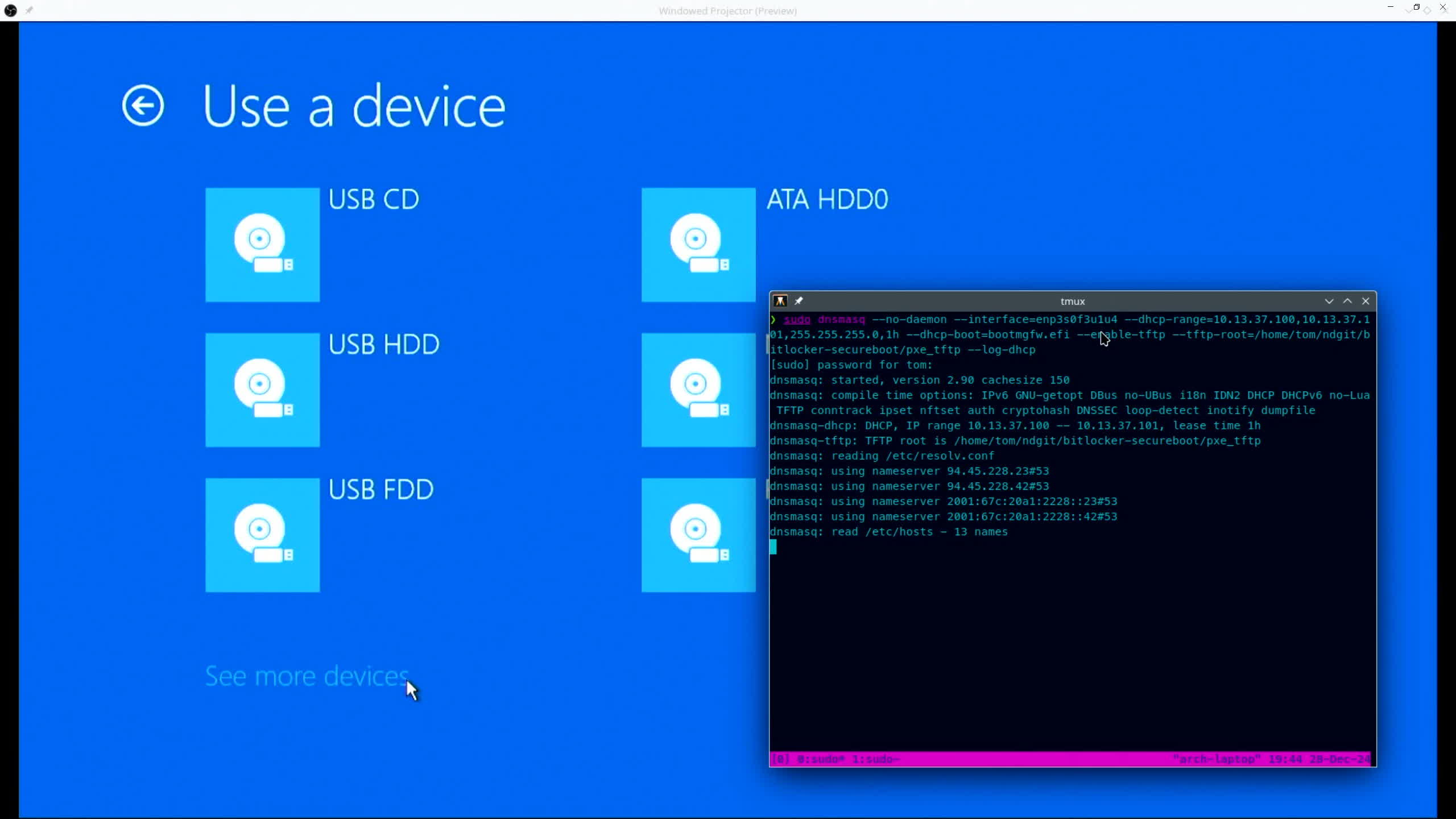
.webp)
Researchers have printed a strategy to bypass Home windows 11’s BitLocker encryption, which allows the elimination of Complete Quantity Encryption Keys (FVEKs) from reminiscence. The document highlights the dangers thinking about bodily assaults and highlights doable weaknesses in reminiscence coverage techniques. The assault revolves round recording the contents of the pc’s RAM throughout operation. If the attacker has get admission to to the instrument, they are able to all of sudden reboot it and unload the reminiscence to retrieve data, together with FVEKs. This guarantees that encryption keys are briefly saved in reminiscence whilst the machine is working. Alternatively, this talent isn’t foolproof. RAM content material degrades unexpectedly when energy is misplaced, which makes lowering downtime crucial. To cut back this harm, researchers stated attackers can use strategies comparable to cooling the RAM or storing energy the use of exterior resources. In a single demonstration, the attacker shorted the reset pins at the motherboard to restart the machine with out chopping energy, saving the reminiscence. Bypassing Safe Boot, a safety same old designed to stop unauthorized systems from working at boot time, supplies further coverage. Alternatively, it has recognized drawbacks and can also be bypassed the use of strategies comparable to shims or different strategies. Those strategies permit attackers to hold out reminiscence research gear. Step-by-Step Assault Manner 1. Create a Bootable USB Software: A USB stick higher than the RAM you need to focus on is ready with particular reminiscence unload elimination instrument. 2. Robotically Restart the Machine At once: The machine restarts at essential occasions—comparable to when Home windows opens however ahead of it reaches the login display—to report the encryption keys. 3. Boot from USB: The attacker enters the default UEFI shell from a USB instrument and exploits the bootloader within. 4. Analyze Reminiscence Dumps: Information dumps are analyzed the use of gear comparable to `xxd` and `searchMem` to search out cryptographic keys saved in reminiscence.
 Flashing By the use of USB Key Restoration The FVEK key used to be discovered beneath explicit Home windows kernel reminiscence pool tags, comparable to `dFVE`, which correspond to BitLocker’s crash unload filter out module (`dumpfve.sys`). This tag at all times unearths the encryption key preceded via metadata indicating the encryption means used (as an example, XTS-AES-128).
Flashing By the use of USB Key Restoration The FVEK key used to be discovered beneath explicit Home windows kernel reminiscence pool tags, comparable to `dFVE`, which correspond to BitLocker’s crash unload filter out module (`dumpfve.sys`). This tag at all times unearths the encryption key preceded via metadata indicating the encryption means used (as an example, XTS-AES-128).
 Temporary Restoration This vulnerability displays that even essentially the most complex encryption techniques like BitLocker aren’t immune from assault. Even though Microsoft makes use of strategies comparable to destroying keys throughout shutdown, residual keys stay in reminiscence in some instances. Chance mitigation: Customers must permit hardware-based safety gear such because the Relied on Platform Module (TPM). Organizations must put into effect safety features to stop unauthorized get admission to. Microsoft would possibly wish to make stronger key control to cut back publicity to risky reminiscence. The invention is a reminder that no safety measure is foolproof, particularly when bodily connectivity is concerned. Scan the International for Unhealthy Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Check out it for Loose
Temporary Restoration This vulnerability displays that even essentially the most complex encryption techniques like BitLocker aren’t immune from assault. Even though Microsoft makes use of strategies comparable to destroying keys throughout shutdown, residual keys stay in reminiscence in some instances. Chance mitigation: Customers must permit hardware-based safety gear such because the Relied on Platform Module (TPM). Organizations must put into effect safety features to stop unauthorized get admission to. Microsoft would possibly wish to make stronger key control to cut back publicity to risky reminiscence. The invention is a reminder that no safety measure is foolproof, particularly when bodily connectivity is concerned. Scan the International for Unhealthy Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Check out it for Loose





:max_bytes(150000):strip_icc():focal(746x727:748x729)/Pregnant-California-Teacher-Dies-Hiking-Trip-Greece-010425-01-536f5e95c7244fb6b5d26a10fa4dac38.jpg)





