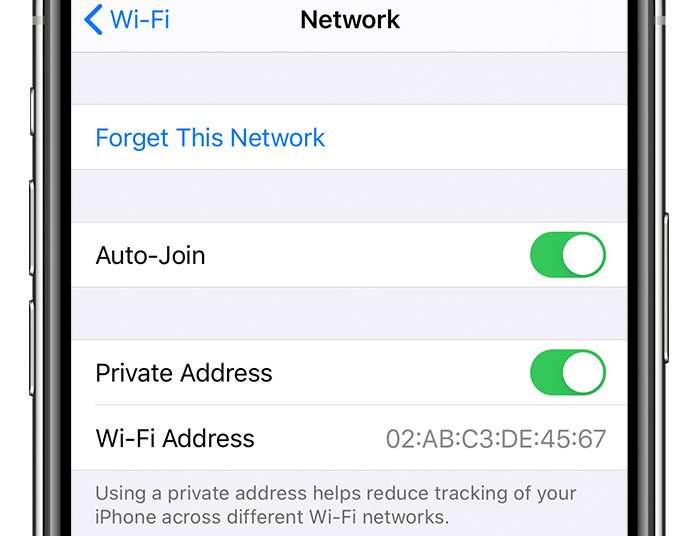
Amplify / Set the name of the game Wi-Fi deal with at the iPhone.Apple 3 years in the past, Apple offered a product to extend the privateness that hides the Wi-Fi addresses of iPhones and iPads once they input the community. On Wednesday, the sector came upon that this section by no means labored as marketed. Even supposing they promised that this default deal with can be hidden and changed with a secret one who was once distinctive for every SSID, Apple units endured to turn the actual factor, which was once broadcast to each and every different instrument hooked up to the Web. The issue is {that a} Wi-Fi media get right of entry to regulate deal with – referred to as a media get right of entry to regulate deal with or just MAC – can be utilized to trace other folks from community to community, simply as a registration number plate quantity can be utilized to trace a automotive because it strikes round the city. Instance: In 2013, a researcher found out a tool that verified the MAC deal with of all units it encountered. The theory was once to proportion details about a area or town and create a profile of iPhone customers, together with the social media websites they discuss with and the selection of puts they discuss with every day. As I wrote on the time: Input CreepyDOL, a cheap, dispensed Wi-Fi gadget that shoots other folks as they stroll round or whole towns. At 4.5 inches by means of 3.5 inches by means of 1.25 inches, every node is sufficiently small to plug right into a wall socket close to the fitness center, cafe, or smash room. And with everybody’s talent to proportion the Web site visitors they accumulate with every other nodes, the gadget can accumulate detailed private data, together with schedules, e-mail addresses, private pictures, and present or previous places. or the folks they supervise. In 2020, Apple launched iOS 14 with a characteristic that, by means of default, concealed Wi-Fi MACs when units had been hooked up to the community. As an alternative, the instrument displayed what Apple referred to as a “non-public Wi-Fi deal with” that was once other for every SSID. Through the years, Apple has expanded the characteristic, for instance, by means of permitting customers to assign a personal Wi-Fi deal with to a given SSID. On Wednesday, Apple launched iOS 17.1. A number of the quite a lot of fixes was once a patch for a vulnerability, codenamed CVE-2023-42846, that avoided encryption from running. Tommy Mysk, one of the most two safety researchers that Apple is understood to have found out and reported at the vulnerability (Talal Haj Bakry was once the opposite), instructed Ars that he examined all of the newest iOS units and located that the flaw reappeared at the 14th, which was once launched in September 2020.” From the start, this was once rendered pointless on account of this mistake,” he stated. “Now we have no longer been in a position to stop units from sending those requests, even with VPN. Even in Lockdown Mode.” When an iPhone or every other instrument enters the community, it initiates a printed message this is despatched to all different units at the community. By way of necessity, this message will have to comprise a MAC. Beginning with iOS 14, this price was once, by means of default, other for every SSID. To informal observers, the characteristic seemed to paintings as marketed. The “supply” indexed within the request was once the personal Wi-Fi deal with. A bit extra digging, alternatively, printed it. that the actual, fastened MAC was once nonetheless broadcast to all different hooked up units, in a separate request phase. Mysk printed a brief video appearing a Mac the use of a Wireshark sniffer packet to observe site visitors at the native community the Mac was once hooked up to. An iPhone working pre-release iOS 17.1, it stocks its actual Wi-Fi MAC on port 5353/UDP.Improve to iOS 17.1 to offer protection to your iPhone from being tracked on Wi-Fi networks. The fallout for many iPhone and iPad customers might be minimum, if no longer non-existent. However for other folks with severe privateness considerations, the lack of those units to cover actual MAC addresses for 3 years generally is a actual downside, particularly on account of Apple’s promise that the use of the characteristic “is helping cut back the monitoring of your iPhone on other Wi-Fi networks.” Apple he didn’t provide an explanation for how the most important failure like this might move undetected for goodbye. An advisory issued by means of the corporate on Wednesday stated best that the repair had “got rid of the inclined code.”