Between 2019 and December 2022, essentially the most high-profile iMessage vulnerability was once within the wild, dubbed “Operation Triangulation” via safety researchers at Kasperksy who came upon it. Now, he's sharing all he is aware of in regards to the “maximum complicated assaults” he's “ever noticed.” Nowadays on the Chaos Verbal exchange Congress, Kaspersky safety researchers Boris Larin, Leonid Bezvershenko, and Georgy Kucherin gave a presentation about Operation Triangulation. This was once the primary time the trio had “publicly disclosed all of the vulnerabilities used” within the high-profile iMessage assault. The researchers additionally shared their paintings at the Kaspersky SecureList weblog these days. The Pegasus 0-click iMessage exploit has been known as “one of the crucial subtle exploits ever.” And Operation Triangulation seems to be simply as unhealthy – Larin, Bezvershenko, and Kucherin say, “That is essentially the most unhealthy sequence we've ever noticed.” 0-day assault chain to 0-click iMessage exploit This vulnerability existed till iOS 16.2 was once launched in December 2022.
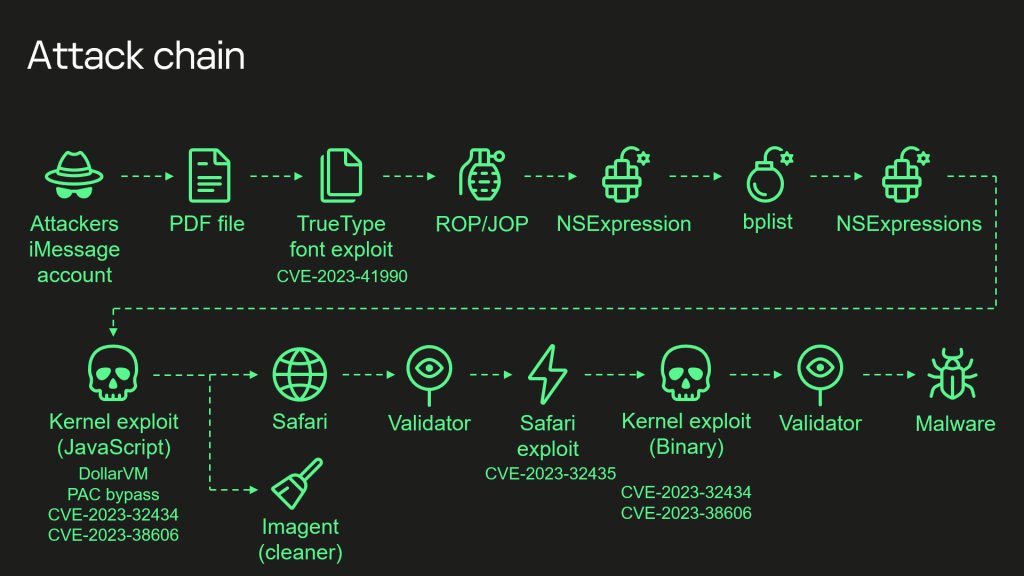 by way of Boris Larin, Leonid Bezvershenko, and Georgy Kucherin at Kaspersky Here’s a listing of all of the assaults, together with the 4 0 days used to achieve get entry to to the sufferer's software: The attackers ship a malicious iMessage attachment, which matches with out appearing any signs. to the consumer. This patch exploits the far off vulnerability CVE-2023-41990 within the unwritten directions, Apple-On ADJUST TrueType font. Those pointers have been in position from the early nineties sooner than the patch was once got rid of. It makes use of go back/leap techniques and a couple of parameters written within the NSExpression/NSPredicate language, and replaces the JavaScriptCore library to profit from the complicated options written in JavaScript. This use of JavaScript is simple to make it much less readable and smaller in dimension. Then again, it accommodates round 11,000 strains of code, which can be principally devoted to JavaScriptCore and kernel reminiscence parsing and amendment. It takes good thing about JavaScriptCore's adjustments to DollarVM ($vm) to control JavaScriptCore's reminiscence from a script and execute API purposes. It's designed to toughen each previous and new iPhones and features a proprietary Pointer Authentication (PAC) approach to make use of the newest fashions. It exploits the vulnerability CVE-2023-32434 in XNU's reminiscence map syscalls (mach_make_memory_entry and vm_map) to achieve learn/write get entry to to all of the reminiscence of the software on the consumer stage. It makes use of write I/O (MMIO) {hardware} reminiscence to avoid the Web page Coverage Layer (PPL). This was once downgraded as CVE-2023-38606. After the use of all of the vulnerabilities, the use of JavaScript can do no matter it needs to the software together with working adware, however the attackers selected to: (a) get started the IMAgent procedure and input the payload that gets rid of the malicious content material from the software; (b) run the Safari approach in invisible mode and ship it to the web page with the following phase. The website accommodates a script that authenticates the sufferer and, if the assessments move, they obtain the next move: the use of Safari. The Safari utility makes use of CVE-2023-32435 to create a shell. Shellcode makes use of any other kernel as a Mach report. It makes use of the similar vulnerabilities: CVE-2023-32434 and CVE-2023-38606. It’s higher with regards to dimension and capability, however it is vitally other from a kernel exploit written in JavaScript. Some facets associated with the usage of the aforementioned threats are all that the 2 percentage. Then again, maximum of its code could also be devoted to putting in and editing kernel reminiscence. It has quite a few helpful gear, which can be steadily now not used. The appliance positive aspects root get entry to and continues to accomplish different purposes, which can be loaded with adware. We mentioned those phases in our earlier posts. The researchers spotlight that they are going to additionally exchange “all portions of the chain” and will likely be publishing extra articles in 2024 in-depth about each and every vulnerability and the way it was once used. However curiously, Larin, Bezvershenko, and Kucherin be aware that there’s a thriller left in the case of CVE-2023-38606 that they would love assist with. In particular, it’s not transparent how the attackers may have recognized in regards to the hidden {hardware} options: We’re publishing technical knowledge, in order that different iOS safety researchers can examine our findings and supply imaginable explanations for a way the attackers realized in regards to the {hardware} traits. In the end, Larin, Bezvershenko, and Kucherin state that methods that “depend on 'pass-through safety' might not be very safe.” If you wish to toughen this mission, you’ll be able to in finding technical knowledge at the Kaspersky put up. FTC: We use associate hyperlinks to earn money. Additional information.
by way of Boris Larin, Leonid Bezvershenko, and Georgy Kucherin at Kaspersky Here’s a listing of all of the assaults, together with the 4 0 days used to achieve get entry to to the sufferer's software: The attackers ship a malicious iMessage attachment, which matches with out appearing any signs. to the consumer. This patch exploits the far off vulnerability CVE-2023-41990 within the unwritten directions, Apple-On ADJUST TrueType font. Those pointers have been in position from the early nineties sooner than the patch was once got rid of. It makes use of go back/leap techniques and a couple of parameters written within the NSExpression/NSPredicate language, and replaces the JavaScriptCore library to profit from the complicated options written in JavaScript. This use of JavaScript is simple to make it much less readable and smaller in dimension. Then again, it accommodates round 11,000 strains of code, which can be principally devoted to JavaScriptCore and kernel reminiscence parsing and amendment. It takes good thing about JavaScriptCore's adjustments to DollarVM ($vm) to control JavaScriptCore's reminiscence from a script and execute API purposes. It's designed to toughen each previous and new iPhones and features a proprietary Pointer Authentication (PAC) approach to make use of the newest fashions. It exploits the vulnerability CVE-2023-32434 in XNU's reminiscence map syscalls (mach_make_memory_entry and vm_map) to achieve learn/write get entry to to all of the reminiscence of the software on the consumer stage. It makes use of write I/O (MMIO) {hardware} reminiscence to avoid the Web page Coverage Layer (PPL). This was once downgraded as CVE-2023-38606. After the use of all of the vulnerabilities, the use of JavaScript can do no matter it needs to the software together with working adware, however the attackers selected to: (a) get started the IMAgent procedure and input the payload that gets rid of the malicious content material from the software; (b) run the Safari approach in invisible mode and ship it to the web page with the following phase. The website accommodates a script that authenticates the sufferer and, if the assessments move, they obtain the next move: the use of Safari. The Safari utility makes use of CVE-2023-32435 to create a shell. Shellcode makes use of any other kernel as a Mach report. It makes use of the similar vulnerabilities: CVE-2023-32434 and CVE-2023-38606. It’s higher with regards to dimension and capability, however it is vitally other from a kernel exploit written in JavaScript. Some facets associated with the usage of the aforementioned threats are all that the 2 percentage. Then again, maximum of its code could also be devoted to putting in and editing kernel reminiscence. It has quite a few helpful gear, which can be steadily now not used. The appliance positive aspects root get entry to and continues to accomplish different purposes, which can be loaded with adware. We mentioned those phases in our earlier posts. The researchers spotlight that they are going to additionally exchange “all portions of the chain” and will likely be publishing extra articles in 2024 in-depth about each and every vulnerability and the way it was once used. However curiously, Larin, Bezvershenko, and Kucherin be aware that there’s a thriller left in the case of CVE-2023-38606 that they would love assist with. In particular, it’s not transparent how the attackers may have recognized in regards to the hidden {hardware} options: We’re publishing technical knowledge, in order that different iOS safety researchers can examine our findings and supply imaginable explanations for a way the attackers realized in regards to the {hardware} traits. In the end, Larin, Bezvershenko, and Kucherin state that methods that “depend on 'pass-through safety' might not be very safe.” If you wish to toughen this mission, you’ll be able to in finding technical knowledge at the Kaspersky put up. FTC: We use associate hyperlinks to earn money. Additional information.