Suspected Russian hackers had been stuck the use of a recently-exploited Home windows vulnerability as a day by day assault towards Ukrainian organizations. The protection flaw (CVE-2024-43451) is an NTLM Hash Disclosure spoofing vulnerability reported through ClearSky safety researchers, which can be utilized to thieve the NTLMv2 hash of a login through forcing a connection to a server controlled through far off attackers. ClearSky spotted this marketing campaign in June after seeing phishing emails designed to make use of it. The e-mails contained links that might obtain a compressed on-line report situated at the up to now compromised server (osvita-kp.gov).[.]ua) of the Division of Schooling and Science of the Kamianets-Podilskyi Town Council. “When a consumer interacts with a URL report through right-clicking, deleting, or transferring it, the vulnerability is brought on,” ClearSky mentioned. When this occurs, a connection to the far off server is made to obtain the felony payloads, together with the SparkRAT release instrument and plenty of platforms that lend a hand attackers keep watch over compromised methods remotely. Whilst investigating the incident, the investigators had been additionally alerted to an try to thieve the NTLM hash by way of the Server Message Block (SMB) protocol. This password can be utilized to “pass-the-hash” or crack to search out the consumer’s password. ClearSky shared this data with Ukraine’s Laptop Emergency Reaction Staff (CERT-UA), which related the attackers to a terrorist staff believed to be of Russian foundation and referred to as UAC-0194.
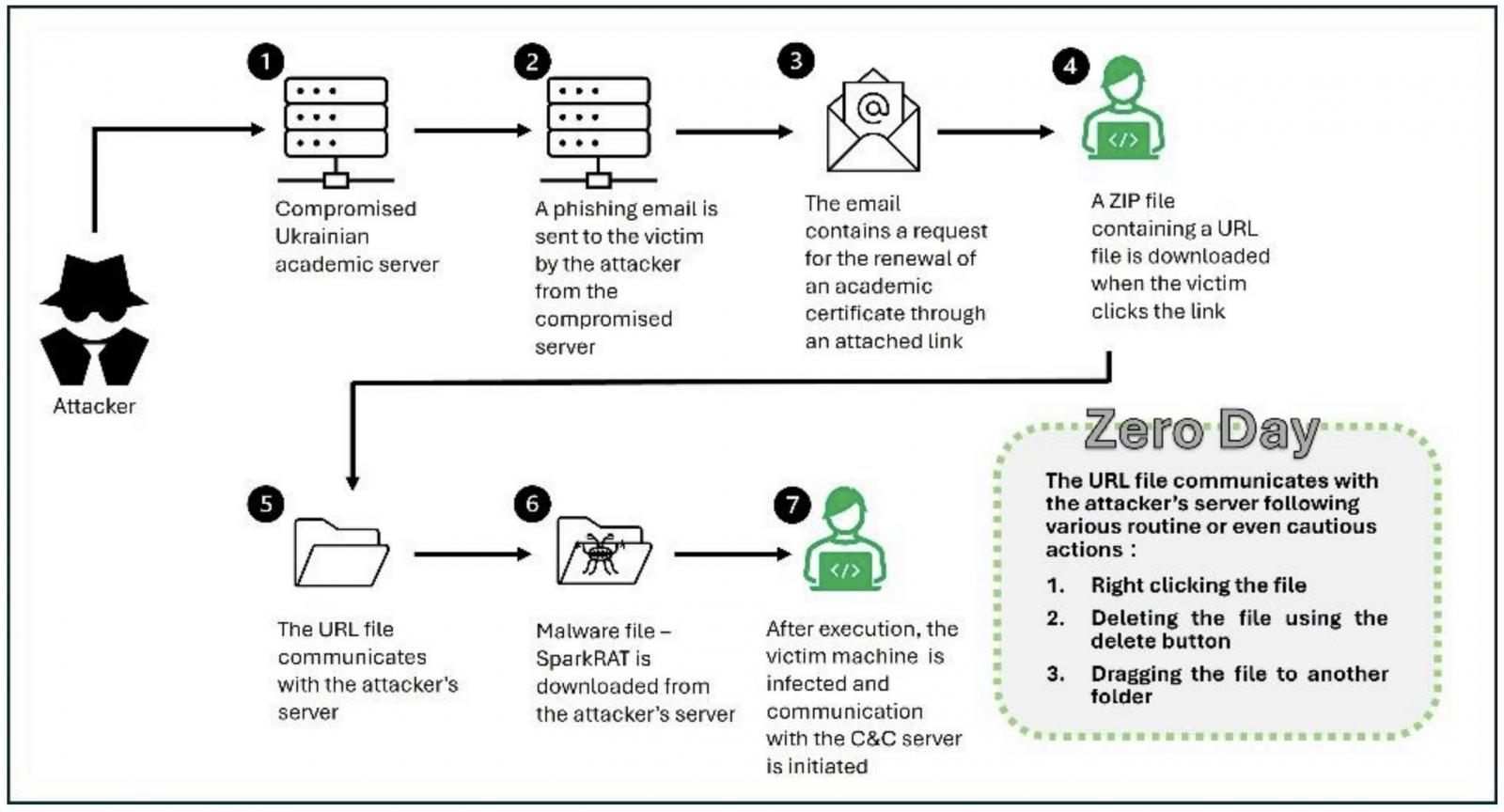 Assault float (ClearSky) The day past, Microsoft posted the vulnerability as a part of the November 2024 Patch Tuesday and showed ClearSky’s findings, announcing that consumer interplay is very important for a hit use. “This vulnerability exposes the NTLMv2 hash to an attacker who can use this to authenticate as a consumer,” Redmond’s advisory defined. “Small movements with the malicious report through the consumer reminiscent of deciding on (single-clicking), surfing (right-clicking), or doing one thing as opposed to opening or executing could cause this drawback.” The corporate says CVE-2024-43451 impacts all supported variations of Home windows, together with Home windows 10 or later and Home windows Server 2008 and up. CISA added the risk to the Recognized Exploited Risk Catalog on Tuesday, ordering them to offer protection to susceptible methods on their networks through December 3, in step with Binding Operational Directive (BOD) 22-01. “Threats of this kind are a widespread assault for cyber criminals and pose a vital possibility to trade,” the cybersecurity company warned.
Assault float (ClearSky) The day past, Microsoft posted the vulnerability as a part of the November 2024 Patch Tuesday and showed ClearSky’s findings, announcing that consumer interplay is very important for a hit use. “This vulnerability exposes the NTLMv2 hash to an attacker who can use this to authenticate as a consumer,” Redmond’s advisory defined. “Small movements with the malicious report through the consumer reminiscent of deciding on (single-clicking), surfing (right-clicking), or doing one thing as opposed to opening or executing could cause this drawback.” The corporate says CVE-2024-43451 impacts all supported variations of Home windows, together with Home windows 10 or later and Home windows Server 2008 and up. CISA added the risk to the Recognized Exploited Risk Catalog on Tuesday, ordering them to offer protection to susceptible methods on their networks through December 3, in step with Binding Operational Directive (BOD) 22-01. “Threats of this kind are a widespread assault for cyber criminals and pose a vital possibility to trade,” the cybersecurity company warned.