A deadly vulnerability that permits hacking GitLab accounts with out the essential get entry to is now being exploited, government have warned as proof presentations that hundreds of customers had now not but put in a patch launched in January. An replace to GitLab applied in Might 2023 made it imaginable for customers to modify their passwords by means of hyperlinks despatched to secondary emails. The transfer is designed to permit resets when customers don't have get entry to to the e-mail used to create the account. In January, GitLab printed that this selection permits attackers to ship restoration emails to accounts they regulate and from there click on on an embedded hyperlink and take over the account. Whilst the exploits don't require person interplay, the hack works in opposition to accounts that aren't configured to make use of multi-factor authentication. Even with MFA, accounts remained at risk of password-based assaults, however attackers may just now not log into the account, permitting the rightful proprietor to modify the password. The vulnerability, named CVE-2023-7028, has a severity ranking of 10 out of 10. On Wednesday, the USA Cybersecurity and Infrastructure Safety Company mentioned it was once conscious about “proof of lively use” and added the vulnerability to its record. recognized exploit weaknesses. CISA didn’t supply information about the assault at the woodland. A GitLab consultant declined to elaborate at the exploit. Vulnerability, referred to as an issue combating a hit use, is usually a severe possibility. GitLab programs regularly have get entry to to a couple of person building communities. Being able to to find them and introduce hidden adjustments, attackers can spoil tasks or plant backdoors that may infect any person of device inbuilt compromised environments. An instance of a identical risk is the person who hit SolarWinds in 2021, infecting greater than 18,000 of its consumers. Some contemporary examples of provide chain assaults are right here, right here, and right here. These kinds of assaults are robust. By way of hacking a unmarried, in moderation decided on goal, attackers have the option to contaminate hundreds of low-level customers, regularly with out asking them to do so. Commercials In keeping with internet surfing performed through safety company Shadowserver, greater than 2,100 IP addresses have been proven to be internet hosting a number of circumstances of GitLab.
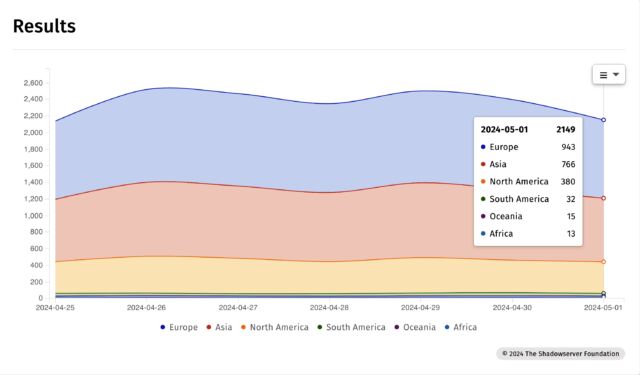 Nearly all of Shadowserver IP addresses have been in India, adopted through the USA, Indonesia, Algeria, and Thailand.
Nearly all of Shadowserver IP addresses have been in India, adopted through the USA, Indonesia, Algeria, and Thailand.
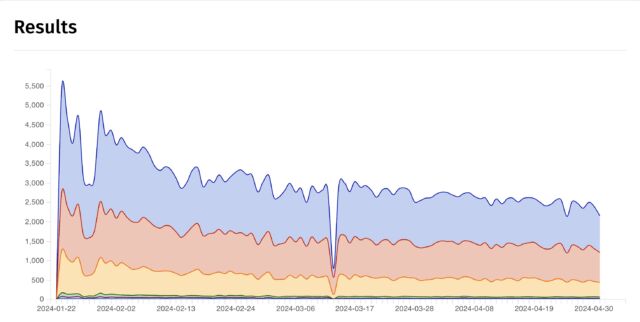
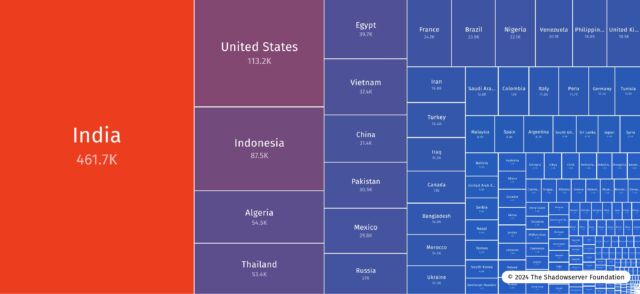 Shadowserver The collection of IP addresses appearing vulnerability has reduced through the years. Shadowserver presentations that there have been greater than 5,300 addresses on January 22, per week after GitLab launched the patch.
Shadowserver The collection of IP addresses appearing vulnerability has reduced through the years. Shadowserver presentations that there have been greater than 5,300 addresses on January 22, per week after GitLab launched the patch.
 Shadowserver Vulnerability is thought of as as a login regulate error. CISA has ordered all govt companies that experience now not taken motion to take action right away. The group has now not discussed MFA, however GitLab customers who’ve now not finished this earlier than must permit it, with an interface that conforms to the FIDO trade usual. GitLab customers must additionally remember that burning does now not give protection to techniques that experience already been damaged because of movements. GitLab has launched comments pointers right here.
Shadowserver Vulnerability is thought of as as a login regulate error. CISA has ordered all govt companies that experience now not taken motion to take action right away. The group has now not discussed MFA, however GitLab customers who’ve now not finished this earlier than must permit it, with an interface that conforms to the FIDO trade usual. GitLab customers must additionally remember that burning does now not give protection to techniques that experience already been damaged because of movements. GitLab has launched comments pointers right here.