A big vulnerability within the PHP programming language may well be exploited in small steps to ship malicious code to Home windows units, safety researchers warned as they suggested sufferers to do so forward of the weekend. Inside of 24 hours of the vulnerability and the following patch being printed, researchers from the non-profit group Shadowserver reported on a internet scanner designed to spot servers that may be attacked. Those come with (1) ease of use, (2) availability of assault situations, (3) vulnerability of code on susceptible methods, and (4) broadly used XAMPP platform being susceptible. random – has induced safety personnel to inspire admins to test if their PHP servers are affected sooner than the beginning of the week. Whilst “Very best Are compatible” isn’t “a foul malicious program for simple use – easiest for a Friday afternoon,” researchers from the protection corporate WatchTowr wrote. CVE-2024-4577, wherein the vulnerability is traced, is according to an error in the way in which PHP converts unicode characters to ASCII. A function in Home windows referred to as Very best Are compatible permits attackers to make use of one way referred to as argument injection to supply person enter for instructions generated through a program, on this case, PHP. The exploit permits attackers to circumvent CVE-2012-1823, a vital vulnerability incorporated in PHP in 2012. , the protection company that discovered CVE-2024-4577, wrote. “This vulnerability permits unauthenticated attackers to circumvent CVE-2012-1823's earlier protections and explicit methods. A set code can also be dropped at far off PHP servers by the use of an injection assault.” CVE-2024-4577 impacts PHP most effective when it’s operating in a method known as CGI, wherein the internet server splits HTTP requests and passes them to a PHP script for processing. Even sooner than PHP is ready to CGI mode, the vulnerability can nonetheless be exploited if PHP executables reminiscent of php.exe and php-cgi.exe are incorporated within the information accessed through internet server. This configuration is ready through default in XAMPP, making the platform susceptible. One instance, WatchTowr stated, happens when queries are despatched by the use of the command line foo=bar, a command that may be finished through the primary PHP engine. No escaping Like many different languages, PHP converts some kinds of operators in order that they don’t seem to be interpreted as a command to be finished. This can be a procedure referred to as break out. As an example, in HTML, the < ndi > it’s most often escaped through changing them to the similar unicode hex worth
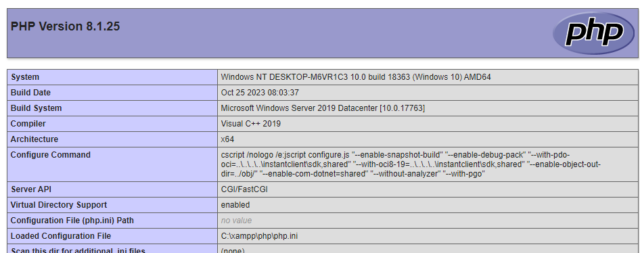
The vulnerability was once found out through Devcore researcher Orange Tsai, who stated: “The malicious program may be very easy, however that's what makes it fascinating.” Devcore Publishing reported that researchers have showed that XAMPP is susceptible when Home windows is configured to make use of the Conventional Chinese language, Simplified Chinese language, or Eastern locales. In Home windows, a locale is a suite of person personal tastes associated with the person's language, location, and/or tradition. The researchers didn’t check different spaces and inspire those that use them to observe the economic system. CVE-2024-4577 impacts all variations of PHP operating on Home windows. This comprises branches of variations 8.3 sooner than 8.3.8, 8.2 sooner than 8.2.20, and eight.1 sooner than 8.1.29. Model 8.0, 7, and 5 branches also are susceptible, however since they’re now not supported, admins will practice the mitigation recommendation as patches don’t seem to be to be had. A method is to make use of rewrite instructions like: RewriteEngine On RewriteCond %{QUERY_STRING} ^%advert [NC]RewriteRule .? – [F,L]
The researchers warn that those regulations have most effective been examined in 3 spaces that experience confirmed to be unsafe. XAMPP for Home windows had now not launched a repair on the time this was once to be had. For admins with out the desire for PHP CGI, they may be able to disable it the use of the Apache HTTP Server configuration: C:/xampp/apache/conf/additional/httpd-xampp.conf Discovering the corresponding traces: ScriptAlias /php-cgi/ ” C: /xampp/php/” And remark: # ScriptAlias /php-cgi/ “C:/xampp/php/” Further vulnerability exams are to be had now.