New knowledge has emerged a couple of phishing marketing campaign concentrated on the builders of the Chrome browser that resulted in a minimum of thirty-five further threats to go into a hacking code, together with knowledge from cybersecurity company Cyberhaven. Even if preliminary experiences centered handiest on Cyberhaven safety extensions, next analysis published that the similar code was once put in in 35 extensions utilized by roughly 2,600,000 folks. From LinkedIn and Google Teams experiences from their leads, the newest marketing campaign began on December 5, 2024. Alternatively, the former subdomains discovered by way of BleepingComputer had been from March 2024. all days we gained that it violates the Chrome Extension coverage within the shape: ‘Useless knowledge within the description’,” reads the Google put up. The Chromium Extension Crew. “The hyperlink on this e-mail seems like a web-based retailer however it is going to a fraudulent web site that may attempt to regulate your chrome and upload malware.” The OAuth phishing assault The assault begins with a phishing e-mail this is despatched to Chrome extension builders without delay or by way of a reinforce e-mail related to their identify. From the emails that BleepingComputer noticed, the next domain names had been used within the discussion board to ship phishing emails: supportchromestore.com forextensions.com chromeforextension.com The phishing e-mail, which seems to be from Google, claims that the extension violates the Chrome Internet Retailer regulations and is in peril of being got rid of. “We don’t permit content material this is deceptive, poorly structured, faulty, needless, over the top, or irrelevant, together with, however now not restricted to, the developer’s identify, identify, symbol, graphics, and promotional photographs,” reads the disclaimer. e-mail. Specifically, the developer of this information believes that their model of the app comprises false knowledge and will have to comply with the Chrome Internet Retailer’s phrases.
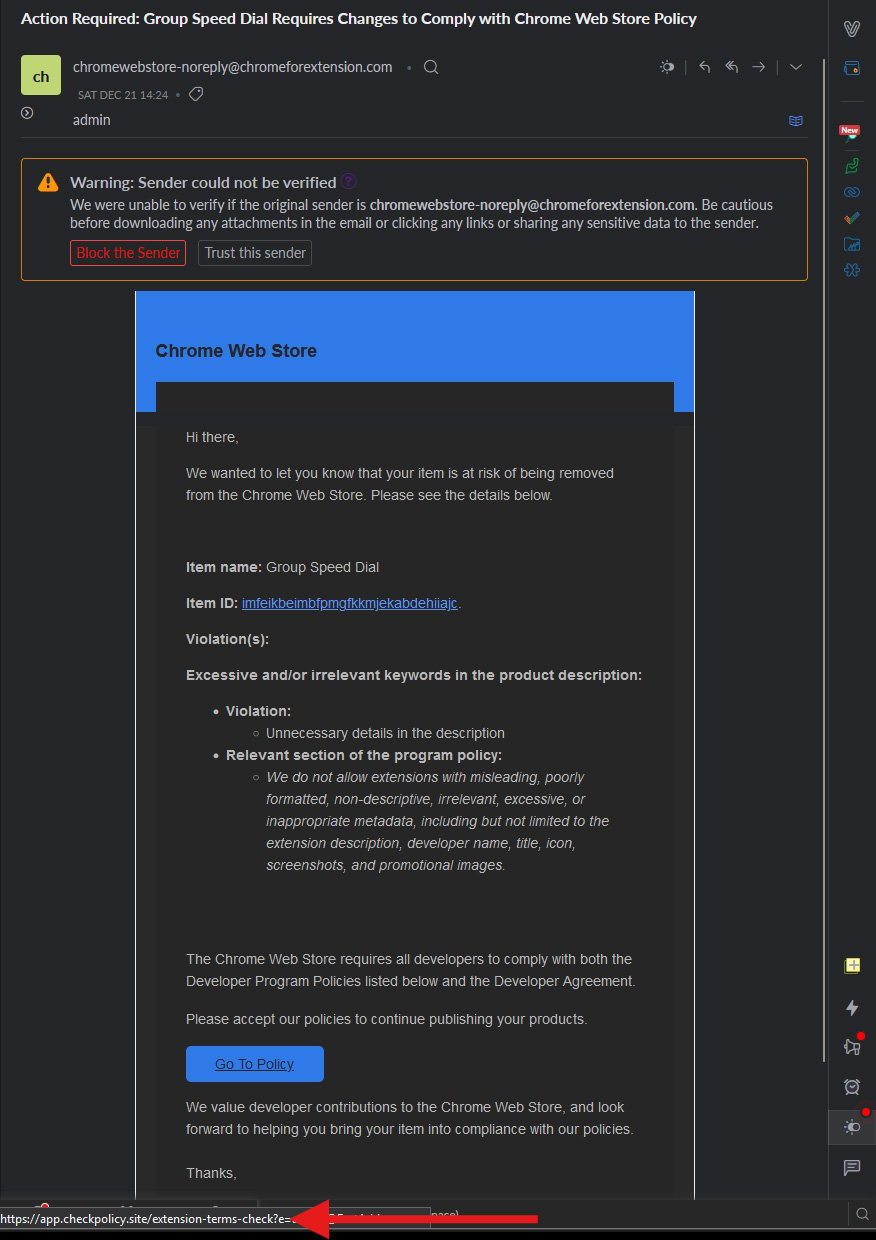 The phishing e-mail used within the assault
The phishing e-mail used within the assault
Supply: Google Groups If the developer clicks the integrated ‘Move To Coverage’ button to grasp the principles they have got violated, they’ll be taken to the authentic login web page on Google’s web site to milk OAuth. This website is a part of Google’s authorization gadget, designed to soundly authorize third-party programs with a Google account.
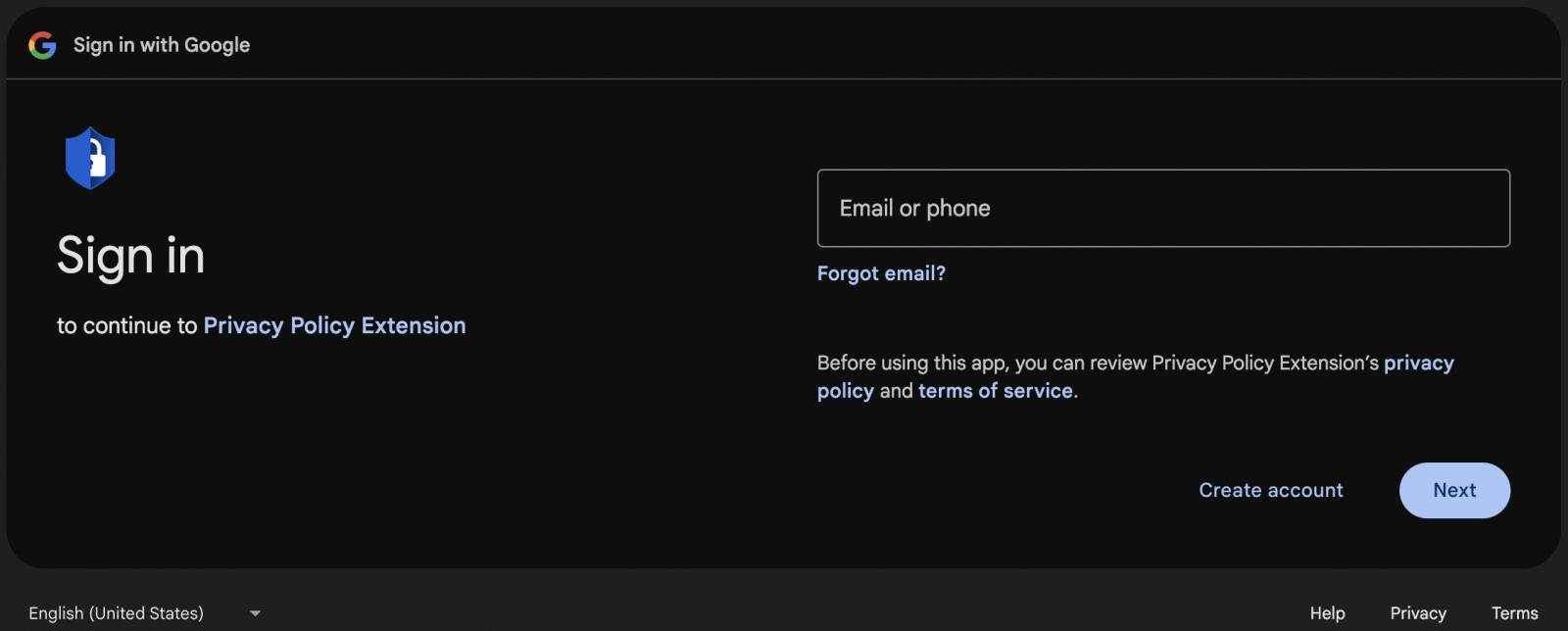 Dangerous permission request
Dangerous permission request
Supply: Cyberhaven At the platform, the attacker used an OAuth exploit known as “Privateness Coverage Extension” that requested the sufferer to grant permission to control Chrome Internet Retailer extensions thru their account. “Should you permit this, Privateness Coverage Extensions might: View, regulate, regulate, or post your Chrome Internet Retailer extensions, topics, apps, and licenses that you would be able to get right of entry to,” says the OAuth authentic web page.
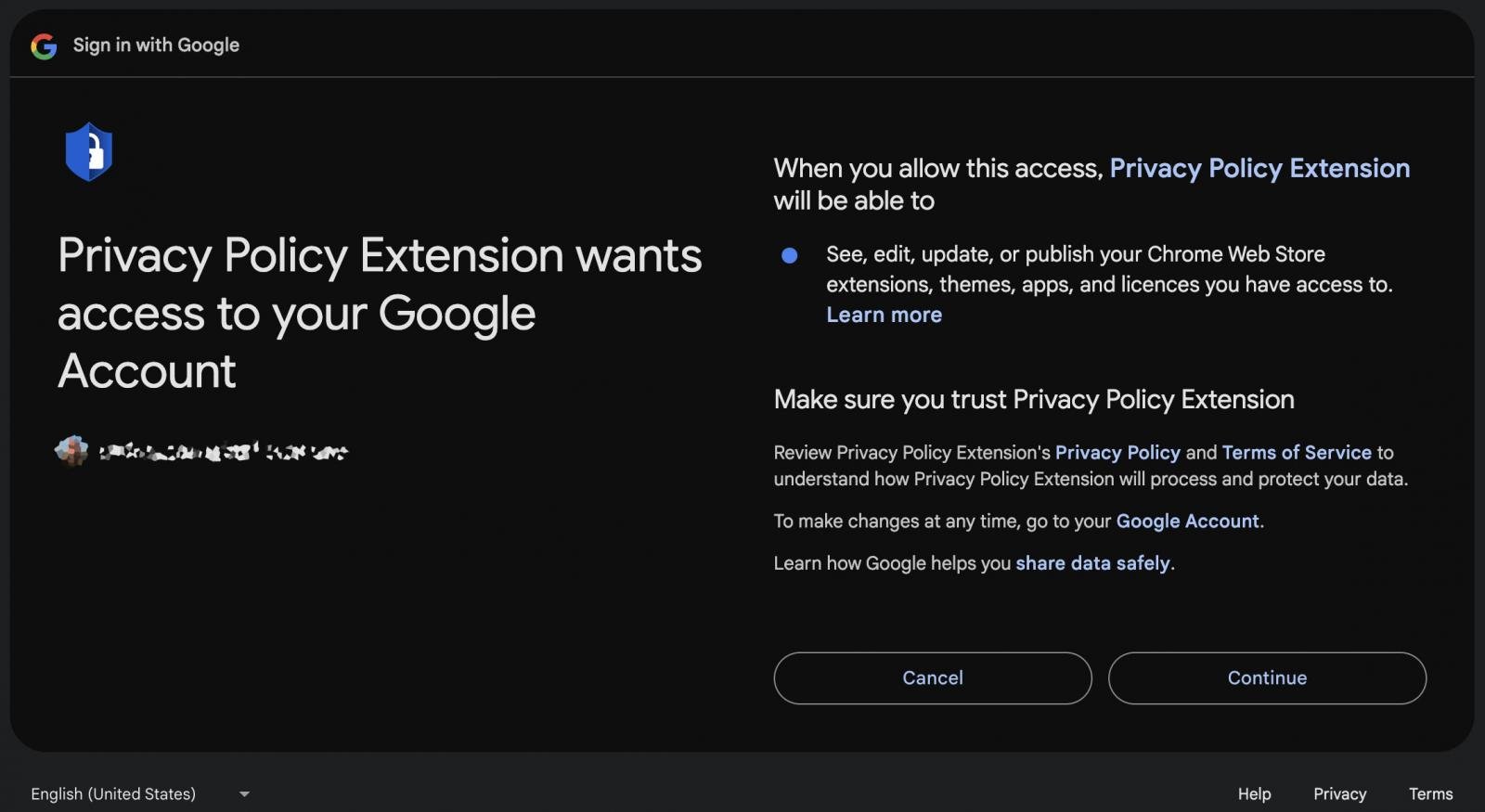 Legitimate knowledge
Legitimate knowledge
Supply: Cyberhaven Multi-factor authentication didn’t assist to offer protection to the account since direct authorization within the OAuth authorization procedure isn’t required, and the method assumes that the person understands the level of the permissions they’re giving. “The worker adopted swimsuit and unwittingly agreed to make use of someone else,” explains Cyberhaven in an obituary. “The worker had complex Google safety and had MFA get right of entry to to his account. The worker didn’t obtain an MFA notification. The worker’s Google profile was once now not compromised.” After the attackers won get right of entry to to the extension developer’s account, they changed the extension to include two malicious information, particularly ’employee.js’ and ‘content material.js,’ which contained code to scouse borrow knowledge from Fb accounts. The hijacked extension was once printed as a “new” model at the Chrome Internet Retailer. Whilst Extension Overall is monitoring thirty-five extensions which have been suffering from this rip-off marketing campaign, IOCs from the vulnerability point out that extra were focused. In line with VirusTotal, the attackers have already registered domain names to be added, even supposing they have got now not fallen sufferer to the assault. Even if lots of the domain names had been created in November and December, BleepingComputer discovered that the attackers are attempting this in March 2024.
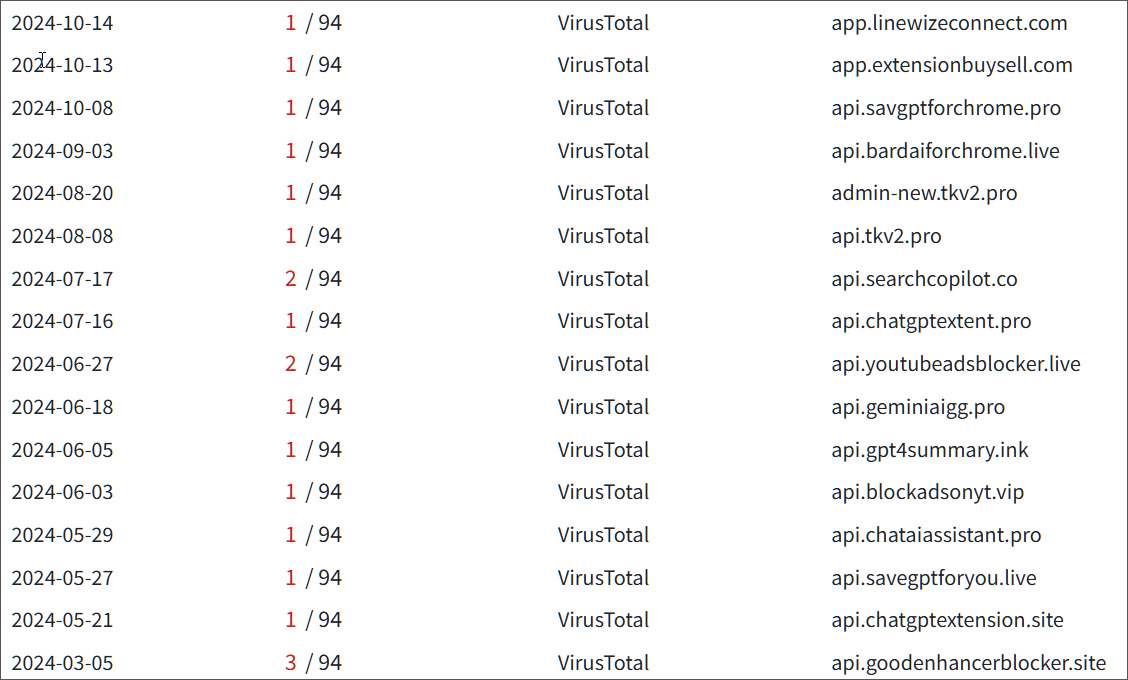 Previous subdomains utilized in phishing campaigns
Previous subdomains utilized in phishing campaigns
Supply: BleepingComputer Focused on Fb accounts An research of the compromised gadget published that the attackers focused the Fb accounts of customers of the poison add-on. Particularly, the knowledge robbery code tried to seize a person’s Fb ID, login credentials, account knowledge, industry account knowledge, and industry accounts.
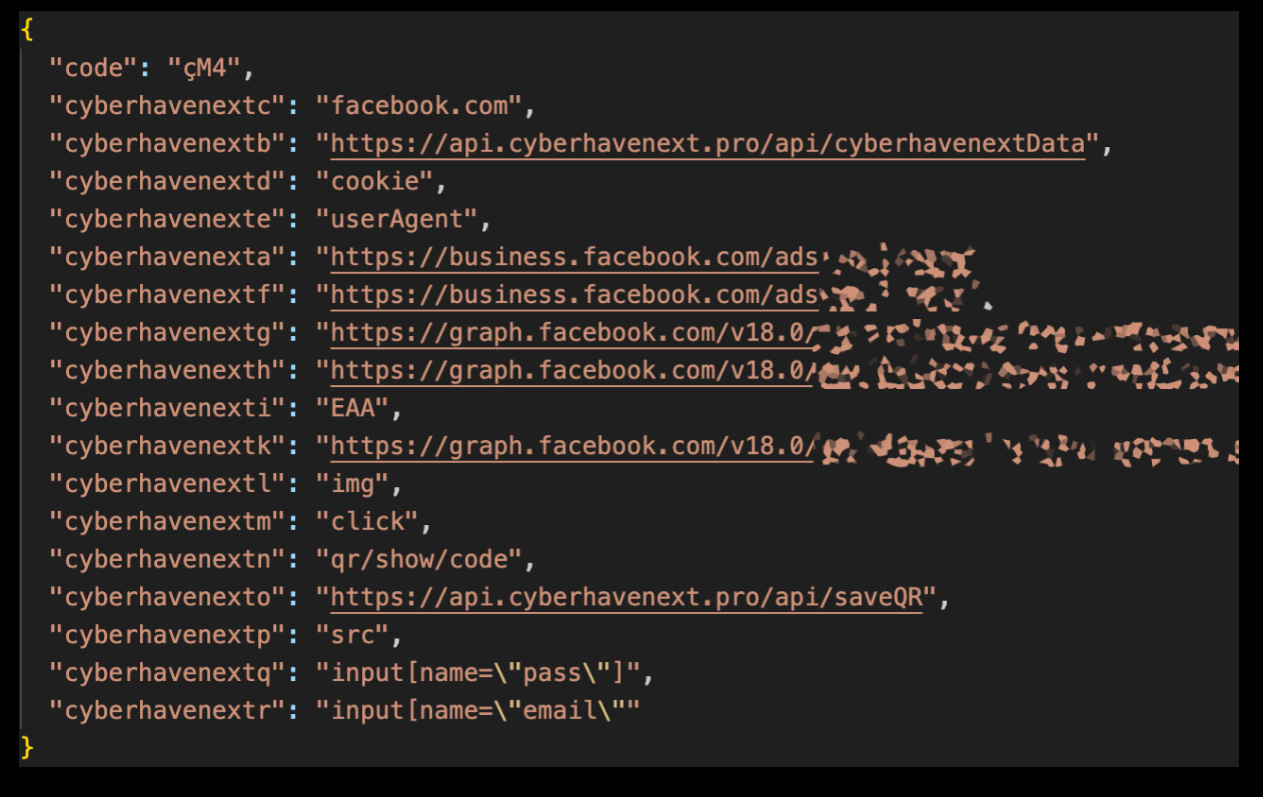 Fb knowledge has been stolen by way of the extension
Fb knowledge has been stolen by way of the extension
Supply: Cyberhaven As well as, the malicious code added a mouse-click listener in particular to the sufferer’s Fb.com job, in search of QR code photographs associated with two-factor authentication or CAPTCHA strategies. That is meant to circumvent the 2FA coverage of the Fb account and make allowance attackers to hack it. The stolen knowledge can also be packaged along with Fb cookies, person reinforce string, Fb ID, and mouse click on occasions and disclosed to the attacker’s server and controlled (C2). Attackers were concentrated on industry Fb accounts thru numerous assault learn how to make bills without delay from the sufferer’s bank card to their account, run faux knowledge or trap folks on-line, or make cash by way of promoting to others.