A brand new Android malware referred to as NGAte can thieve cash from fee playing cards by means of sending information learn by means of a Close to-field Conversation (NFC) software to an attacker’s software. Particularly, NGate permits attackers to take sufferers’ bank cards and make unlawful bills or withdraw cash from ATMs. The mission has been energetic since November 2023 and is in keeping with a contemporary document from ESET in regards to the expanding use of internet programs (PWAs) and complicated WebAPKs to thieve banking data from Czech customers. In a learn about launched lately, the cybersecurity company mentioned the NGAte malware used to be extensively utilized all the way through the marketing campaign in some circumstances to without delay thieve cash. Stealing card data by way of an NFC software Assaults get started with malicious scripts, computerized calls with pre-recorded messages, or tricking sufferers into putting in malicious PWAs, then WebAPKs, on their units. Those on-line systems are promoted as fast safety updates and use the authentication token and login type of the objective financial institution to thieve buyer data.
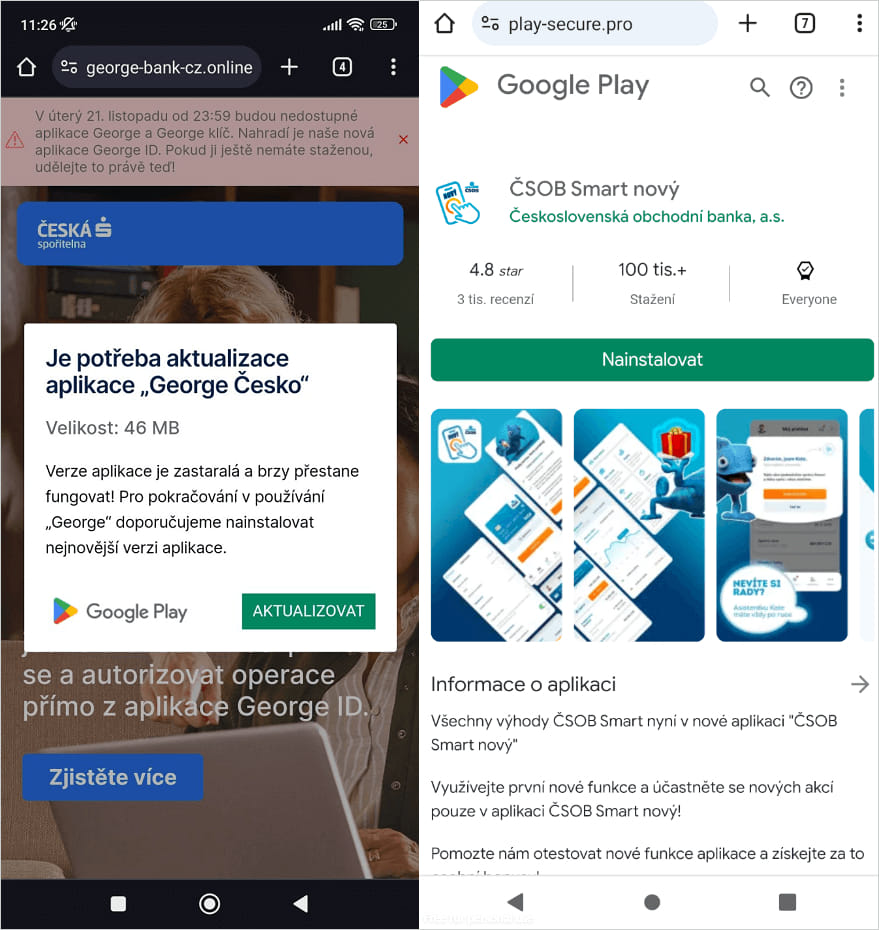 Faux Play Retailer pages the place WebAPK is put in
Faux Play Retailer pages the place WebAPK is put in
Supply: ESET Those systems don’t require permission to put in. As an alternative, they abuse the API of the browser they run in to achieve get right of entry to to the software’s {hardware}. As soon as the phishing section is completed by way of WebAPK, the sufferer is tricked into putting in NGAte via the next move in the second one assault section. As soon as put in, the malware opens an open supply referred to as ‘NFCGate’ which used to be advanced by means of college researchers for NFC trying out and trying out. This device helps software recording, restoration, restoration, and formatting, and does no longer at all times require the software to be “rooted” to paintings. NGate makes use of a tool to seize NFC information from fee playing cards close to an inflamed software after which sends it to the software, both without delay or via a server. An attacker can retailer those as digital playing cards on their software and show the token at ATMs that use NFC for money withdrawals, or bills on the level of sale (PoS).
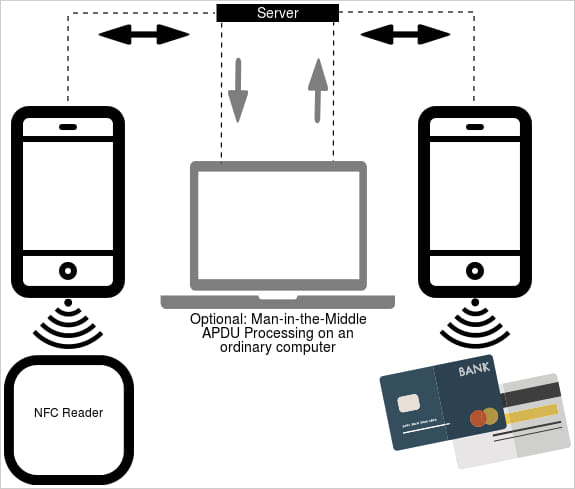 NFC information switch manner
NFC information switch manner
Supply: ESET In a video presentation, ESET crime researcher Lukas Stefanko additionally demonstrates how the NFCGate module in NGAte can be utilized to scan and document card information in wallets and handbags. On this case, the shop attacker can obtain the knowledge during the server and make a fee with out connecting to the sufferer’s card. Stefanko says the malware will also be used to compare the original identifiers of different NFC get right of entry to playing cards and tokens to achieve access into limited spaces. Acquiring the cardboard’s PIN Withdrawals from maximum ATMs require the cardboard’s PIN code, which the researchers say is acquired by means of the sufferer. After the PWA / WebAPK phishing step is done, the attackers name the sufferer, pretending to be a financial institution worker, to inform them about their safety considerations. They then ship an SMS with a hyperlink to obtain NGAte, which they are saying is an app that can be utilized to make sure their fee card and PIN. When the sufferer scans the cardboard with their software and enters a PIN to “authenticate” the phishing malware, delicate data is supplied to the attacker, prompting them to take away it.
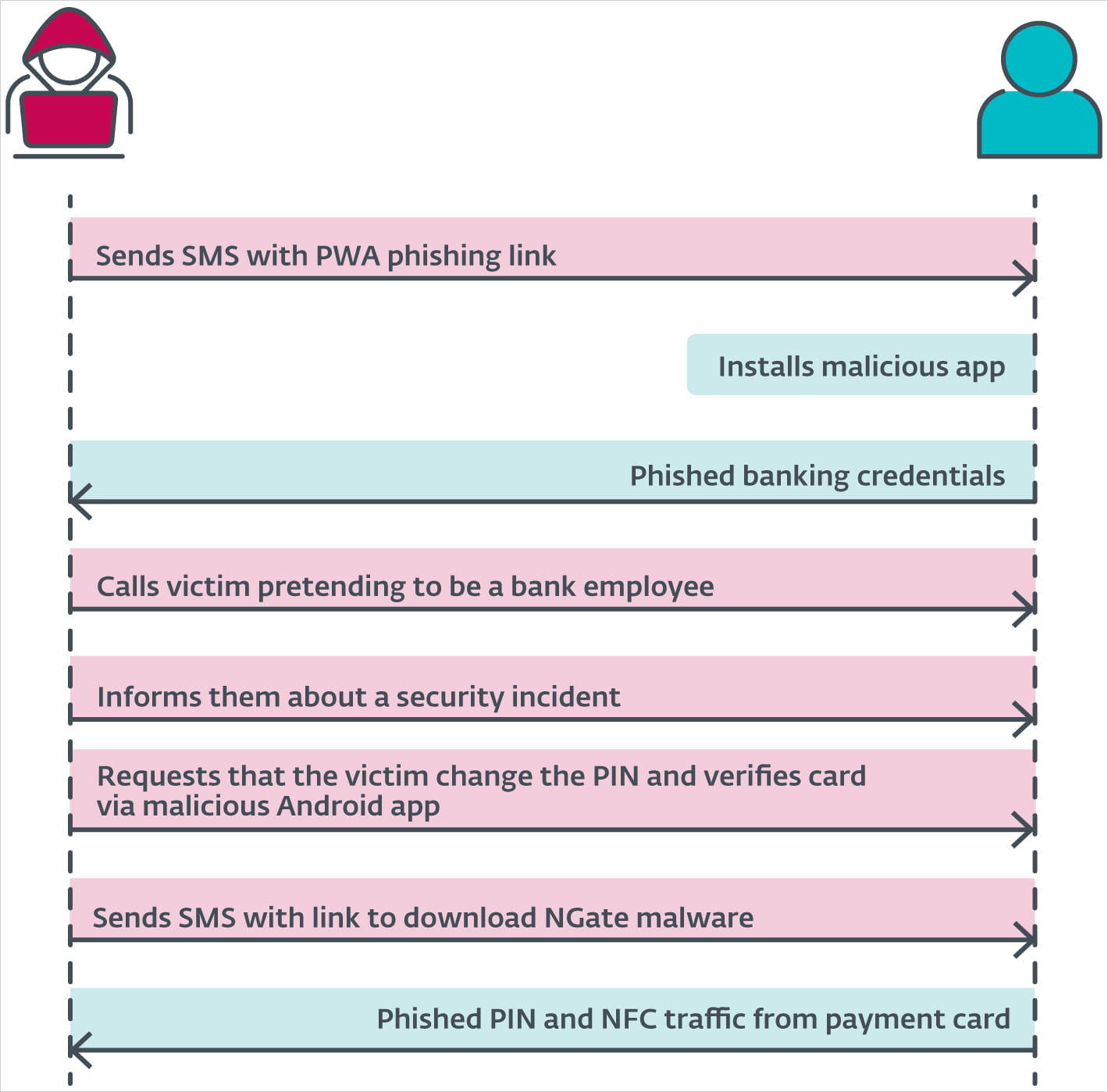 Complete assault in a nutshell
Complete assault in a nutshell
Supply: ESET The Czech police have already stuck one of the crucial cybercriminals who pull this out in Prague, however because the gadget may also be affected, it poses a significant possibility to Android customers. ESET additionally displays the potential for making verbal exchange tags, shuttle tickets, ID badges, club playing cards, and different NFC-enabled applied sciences, so shedding cash without delay isn’t the one unfavorable downside. If you do not use NFC often, you’ll be able to cut back the danger by means of disabling your NFC software. On Android, pass to Settings > Hooked up units > Connectivity settings > NFC and toggle this transfer to off.
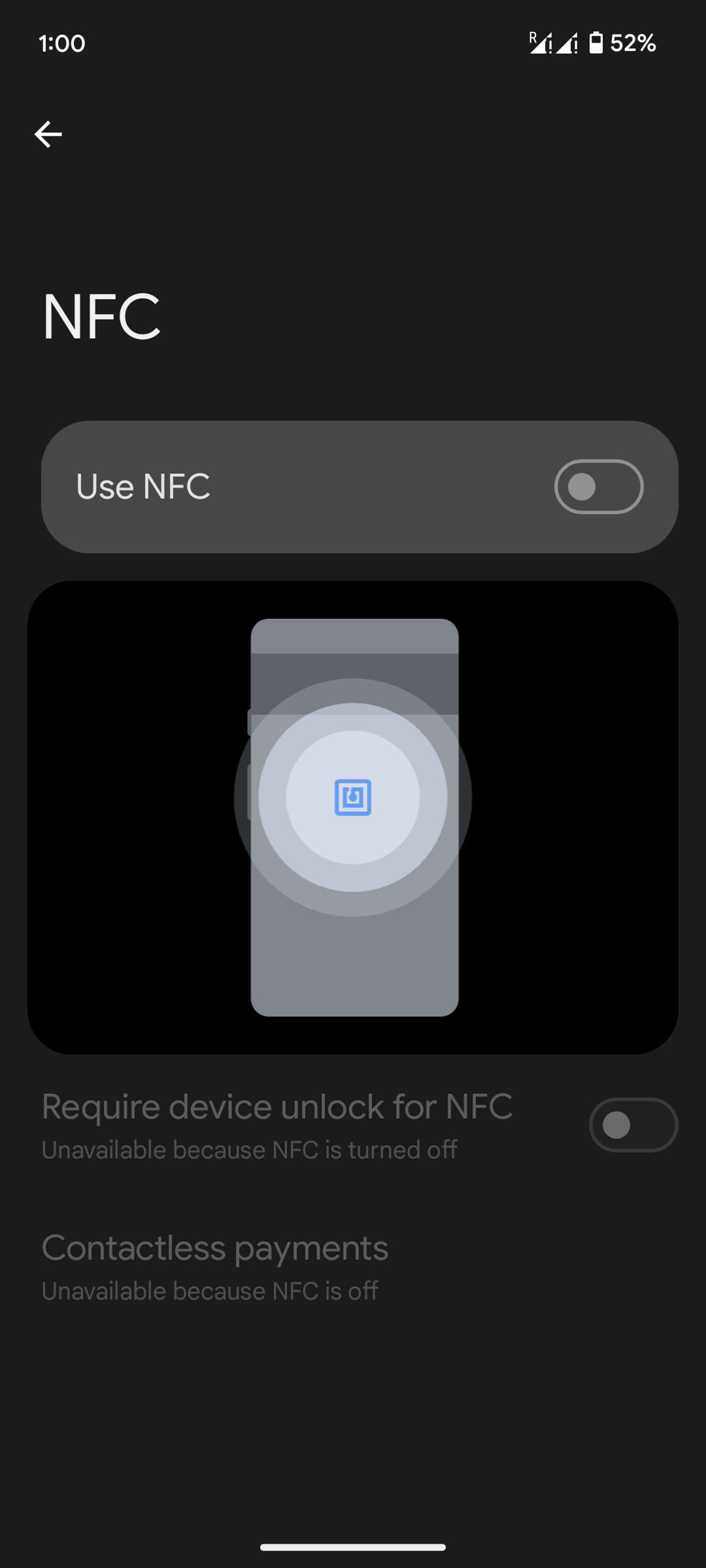
If you need NFC to be at all times on, test all of the app’s permissions and block get right of entry to to people who want it; set up banking apps best from the respectable web page of the group or Google Play, and make certain that the app you might be the usage of isn’t a WebAPK. WebAPKs are most often very small in measurement, are put in without delay from the browser’s homepage, don’t seem underneath ‘/information/app’ like commonplace Android apps, and display restricted data in Settings > Apps.