
A brand new UEFI Safe Boot bypass vulnerability tracked as CVE-2024-7344 that has effects on instrument signed by way of Microsoft can be utilized to put in bootkits even if Safe Boot coverage is enabled. Inclined UEFI instrument is to be had in numerous real-time restoration gear from different third-party instrument builders. Bootkits constitute a significant safety danger this is tricky to stumble on as a result of they act sooner than the working gadget is in a position, and live on OS reinstallation. The principle drawback This drawback comes from the PE Loader application, which permits downloading any UEFI Binary, even sooner than it’s signed. Specifically, the inclined UEFI instrument does now not depend on accept as true with purposes similar to ‘LoadImage’ and ‘StartImage’ which make sure that the statistics are in line with the accept as true with database (db) and the deletion database (dbx). On this case, ‘reloader.efi’ manually reloads and replaces reminiscence from ‘cloak.dat’, which incorporates an encrypted XOR PE symbol. This can also be exploited by way of an attacker by way of eliminating the default OS bootloader from the EFI partition and putting in a inclined ‘reloader.efi’ and planting a malicious ‘cloak.dat’ record in its paths. On gadget boot, the bootloader will delete and execute the mistake with out verifying Boot Safety.
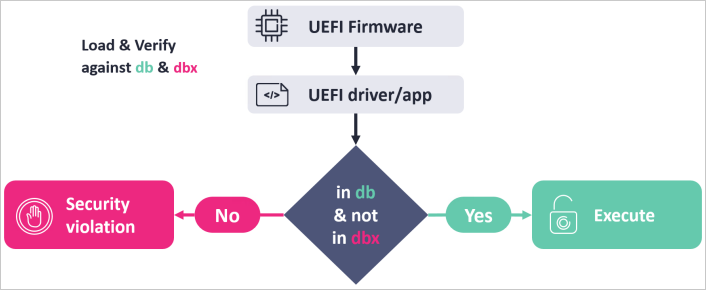 UEFI Secure Boot procedure
UEFI Secure Boot procedure
Supply: ESET Scope of affect The vulnerability impacts UEFI instrument this is designed to give a boost to restoration, disk upkeep, or backup and isn’t a UEFI application. The ESET record lists the next merchandise and variations in peril: Howyar SysReturn sooner than model 10.2.023_20240919 Greenware Greenware sooner than 10.2.023-20240927 Radix SmartRecovery sooner than 11.2.023-20240927 Sanfong model 10.3.024-20241127 WASAY eRecoveryRX sooner than 8.4.022-20241127 CES NeoImpact sooner than 10.1.024-20241127 SignalComputer HDD King sooner than the discharge of model 10.3.021-2024 in order that the attackers aren’t affected. CVE-2024-7344 even supposing the above instrument isn’t to be had at the goal pc. Hackers can perform the assault by way of sending inclined other folks a ‘reloader’. efi’ binary from the ones techniques. Alternatively, the ones the usage of the above instrument and affected variations must transfer to a brand new location once imaginable to get to the bottom of the problem. ESET printed a video appearing how this vulnerability can be utilized on methods with Bootstrap Safety Updates and Mitigations Microsoft has launched a patch for CVE-2024-7344 ESET found out the vulnerability on July 8, 2024, and notified CERT. Coordination Heart (CERT/CC) to expose data to affected events. The affected distributors mounted the problem of their merchandise and Microsoft got rid of the certificate for the January 14th Patch Tuesday replace. Later, on January 14, 2025, Microsoft got rid of the licenses for the inclined UEFI instrument, which must have avoided any try to use their buttons. This limitation simplest applies to customers who’ve put in the most recent Home windows updates. ESET additionally shared PowerShell instructions that admins of crucial methods can use to manually take a look at if the uninstallation has been effectively implemented.












