A in the past unknown ransomware, referred to as ShrinkLocker, encrypts compromised information the usage of BitLocker constructed into the Home windows working gadget. BitLocker is a complete quantity encryptor that began in 2007 with the discharge of Home windows Vista. Customers use them to encrypt complete laborious drives to forestall folks from studying or converting information in the event that they achieve get admission to to the disk. Beginning with the discharge of Home windows 10, BitLocker via default has used 128-bit and 256-bit XTS-AES encryption algorithms, offering further coverage towards threats that depend on converting passwords to make incomprehensible adjustments in plaintext. Just lately, researchers from the protection corporate Kaspersky discovered an attacker the usage of BitLocker to encrypt information on machines situated in Mexico, Indonesia, and Jordan. The researchers referred to as the brand new resolution ShrinkLocker, as it makes use of BitLocker and as it reduces the scale of each and every non-boot partition via 100 MB and divides the unallocated area into new walls of the similar dimension. “Our reaction and research of the malware is proof that the attackers are making improvements to their techniques to steer clear of detection,” the researchers wrote on Friday. “At this level, we noticed the similar BitLocker exploit for unauthorized information encryption.” ShrinkLocker isn’t the primary malware to make use of BitLocker. In 2022, Microsoft reported that ransomware attackers with a nexus in Iran extensively utilized this instrument to encrypt information. That very same yr, Russian agribusiness Miratorg was once attacked via ransomware that used BitLocker to encrypt information saved on inflamed units. When put in on a tool, ShrinkLocker runs a VisualBasic script that invokes the Home windows Control Instrumentation and Win32_OperatingSystem categories to get details about the working gadget. “For each and every component throughout the seek effects, the script tests whether or not the present area differs from the required one,” Kaspersky researchers wrote. “If that is so, the script ends mechanically. After that, it tests if the working gadget title comprises 'xp,' '2000,' '2003,' or 'vista,' and if Home windows fits any of those, the script mechanically ends and deletes it.” simplest.”
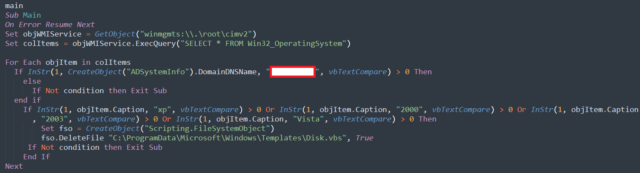 Amplify / Screenshot appearing the fundamentals of operation. Kaspersky script then continues to make use of WMI to question OS knowledge. It continues to accomplish disk alternative operations, which would possibly range relying at the model of the OS put in. The ransomware does this on native, laborious drives. The verdict to depart community drives on my own is also motivated via a want to introduce community safety. Commercial In any case, ShrinkLocker bypasses the protection measures designed to offer protection to BitLocker's personal key and proceeds to delete it. It then helps using passwords, as coverage towards any individual who can regulate BitLocker and as an encryptor of gadget information. The cause of casting off the default coverage is to forestall primary restoration pieces via the landlord of the instrument. ShrinkLocker then proceeds to generate a 64-character encryption key the usage of random multiplication and alternative: A alternative containing the digits 0-9; The well-known pangram, “The short brown wolf leaps on the lazy canine,” in decrease and uppercase letters, containing the English alphabet; Particular options. After a number of different steps, the information is encrypted. The following time the instrument restarts, the show will seem like this:
Amplify / Screenshot appearing the fundamentals of operation. Kaspersky script then continues to make use of WMI to question OS knowledge. It continues to accomplish disk alternative operations, which would possibly range relying at the model of the OS put in. The ransomware does this on native, laborious drives. The verdict to depart community drives on my own is also motivated via a want to introduce community safety. Commercial In any case, ShrinkLocker bypasses the protection measures designed to offer protection to BitLocker's personal key and proceeds to delete it. It then helps using passwords, as coverage towards any individual who can regulate BitLocker and as an encryptor of gadget information. The cause of casting off the default coverage is to forestall primary restoration pieces via the landlord of the instrument. ShrinkLocker then proceeds to generate a 64-character encryption key the usage of random multiplication and alternative: A alternative containing the digits 0-9; The well-known pangram, “The short brown wolf leaps on the lazy canine,” in decrease and uppercase letters, containing the English alphabet; Particular options. After a number of different steps, the information is encrypted. The following time the instrument restarts, the show will seem like this:
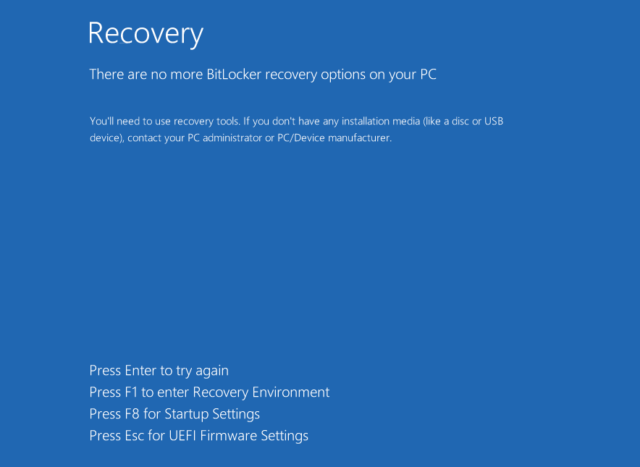 Amplify / Screenshot appearing the BitLocker restoration display.Kaspersky Decrypting drives and not using a key supplied via the attacker is tricky and will not be imaginable generally. Despite the fact that it’s imaginable to get better the password with the usual values used to generate the keys, the scripts use other values which can be other for each and every inflamed instrument. Those adjustments are simple to restart. There aren’t any defenses for ShrinkLocker to forestall a success assaults. Kaspersky recommends the next: Use robust, well-established endpoint coverage to come across threats that try to misuse BitLocker; Allow Systematic Detection and Reaction (MDR) to investigate threats; If BitLocker is enabled, make certain it makes use of a password and that restoration keys are saved in a safe location; Be certain customers have restricted get admission to. This prevents them from enabling encryption or converting registry keys themselves; Get started community visitors logging and tracking. Configure logging for each GET and POST requests. Within the match of an infection, requests made to the attacker would possibly include passwords or keys; Track occasions associated with the execution of VBS and PowerShell, then save scripts and instructions to exterior garage units that may be got rid of in the neighborhood; Make common backups, stay them on-line, and take a look at them. Friday's document additionally contains signs that organizations can use to decide whether or not they’re being centered via ShrinkLocker. Symbol courtesy of Getty Photographs
Amplify / Screenshot appearing the BitLocker restoration display.Kaspersky Decrypting drives and not using a key supplied via the attacker is tricky and will not be imaginable generally. Despite the fact that it’s imaginable to get better the password with the usual values used to generate the keys, the scripts use other values which can be other for each and every inflamed instrument. Those adjustments are simple to restart. There aren’t any defenses for ShrinkLocker to forestall a success assaults. Kaspersky recommends the next: Use robust, well-established endpoint coverage to come across threats that try to misuse BitLocker; Allow Systematic Detection and Reaction (MDR) to investigate threats; If BitLocker is enabled, make certain it makes use of a password and that restoration keys are saved in a safe location; Be certain customers have restricted get admission to. This prevents them from enabling encryption or converting registry keys themselves; Get started community visitors logging and tracking. Configure logging for each GET and POST requests. Within the match of an infection, requests made to the attacker would possibly include passwords or keys; Track occasions associated with the execution of VBS and PowerShell, then save scripts and instructions to exterior garage units that may be got rid of in the neighborhood; Make common backups, stay them on-line, and take a look at them. Friday's document additionally contains signs that organizations can use to decide whether or not they’re being centered via ShrinkLocker. Symbol courtesy of Getty Photographs












