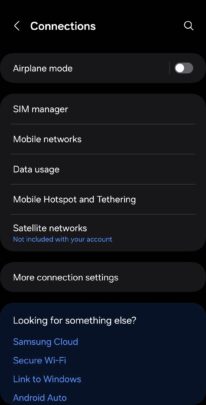
Susceptible actors extensively use Scalable Vector Graphics (SVG) attachments to show fraudulent paperwork or ship malware whilst evading detection. Maximum pictures at the Web are JPG or PNG recordsdata, that are made up of small devices known as pixels. Each and every pixel has its personal colour price, and in combination, those pixels make up all the symbol. SVG, or Scalable Vector Graphics, shows pictures in a different way, as as a substitute of the usage of pixels, pictures are created via strains, shapes, and textual content which are outlined in mathematical textual content in code. As an example, the next textual content will create a rectangle, circle, hyperlink, and different textual content: Hi, SVG! When opened within the browser, the record will generate the photographs described above.

Supply: BleepingComputer Since those are vector pictures, they robotically resize with out dropping anything else to the picture’s high quality or look, making them ultimate to be used in browsers with other resolutions. The use of SVG stickers to steer clear of detection The usage of SVG stickers in phishing campaigns isn’t unusual, with BleepingComputer reporting on their use in earlier Qbot malware campaigns and with the intention to cover malicious scripts. Then again, attackers are an increasing number of the usage of SVG recordsdata of their phishing campaigns consistent with safety researcher MalwareHunterTeam, who shared fresh examples. [1, 2] and BleepingComputer. Those examples, and others noticed by means of BleepingComputer, display how flexible SVG interfaces will also be as a result of they now not best help you show pictures however may also be used to show HTML, manipulate the item, and execute JavaScript when the picture is loaded. This permits attackers to create SVG stickers that now not best show pictures but in addition create fraudulent paperwork to thieve knowledge. As noticed underneath, the newest SVG connector [VirusTotal] presentations a pretend Excel spreadsheet with a login shape, which when submitted, sends information to the attackers.
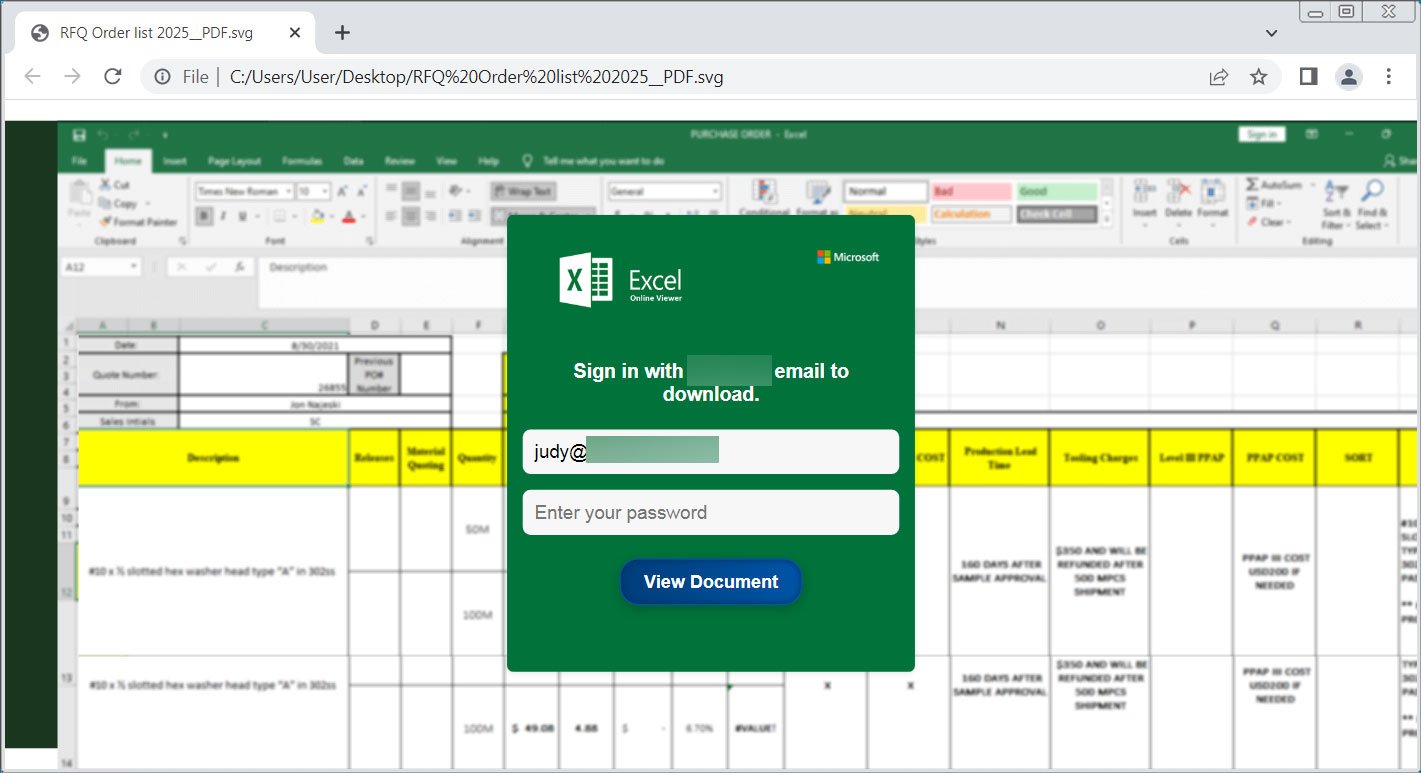 SVG decal appearing cheat shape
SVG decal appearing cheat shape
Supply: BleepingComputer Some SVG stickers utilized in the newest model [VirusTotal] fake to be official paperwork or requests for info, prompting you to click on a obtain button, after which obtain malware from a far off web site.
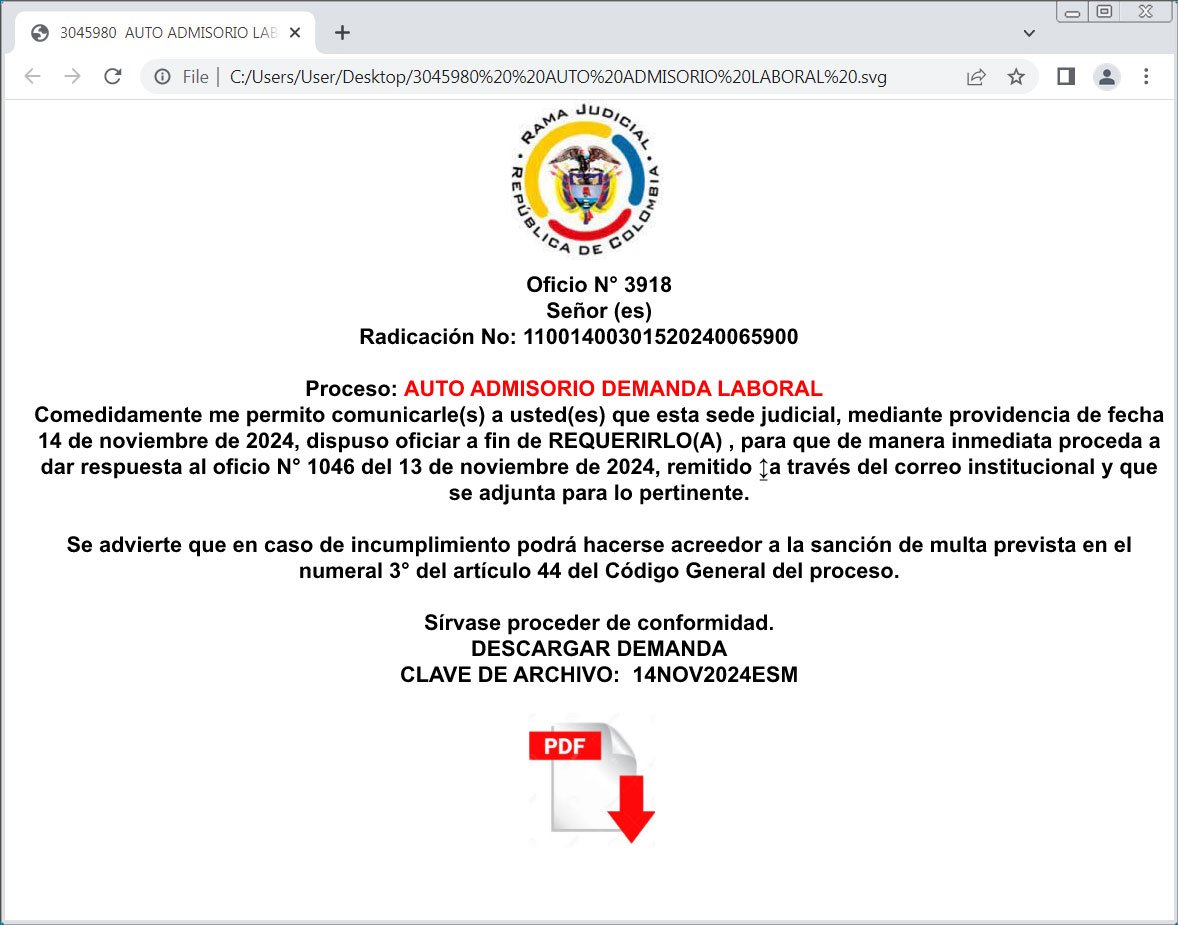 An SVG record used to distribute malware
An SVG record used to distribute malware
Supply: BleepingComputer Some campaigns use SVG tags and embed JavaScript to redirect browsers to internet pages that generate cookie paperwork when the picture is opened. The issue is that since those recordsdata in most cases best constitute pictures, they aren’t visual to safety device usually. From the examples noticed by means of BleepingComputer and uploaded to VirusTotal, on the whole, they’ve one or two stories with safety device. With that stated, receiving an SVG attachment isn’t unusual in professional emails, and must be thought to be right away. Except you are a developer and be expecting to obtain some of these attachments, it is a good suggestion to delete any emails that comprise them.