Getty Photographs Ransomware attackers have been fast to milk an easy-to-use vulnerability within the PHP programming language that spews malicious code onto internet servers, safety researchers stated. As of Thursday, Web screens by way of safety company Censys discovered 1,000 servers susceptible to a ransomware assault referred to as TellYouThePass, down from 1,800 found out on Monday. The servers, which can be positioned in China, not display their location; as an alternative, many listing the positioning report, which signifies that each one information are given the .locked extension, indicating that they’re locked. The following liberate calls for about $6,500 to interchange the interpretation keys.
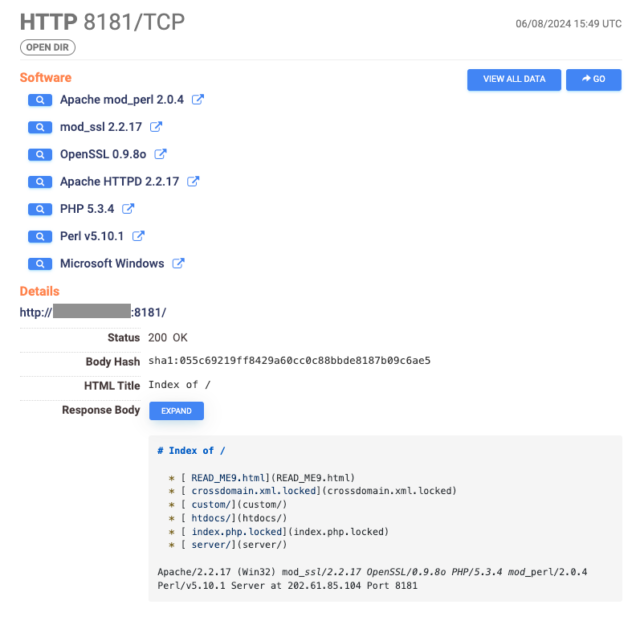 Growth / Liberate of PHP servers containing TellYouThePass ransomware.Censys
Growth / Liberate of PHP servers containing TellYouThePass ransomware.Censys
 Extend / Subsequent Redemption.Censys Vulnerability, which is tracked as CVE-2024-4577 and has a ranking of 9.8 out of 10, comes from mistakes in the way in which PHP converts Unicode characters into ASCII. A function in Home windows referred to as Highest Have compatibility permits attackers to make use of a method referred to as argument injection to transform person enter into characters that factor malicious instructions to the primary PHP program. The exploit permits attackers to avoid CVE-2012-1823, a crucial vulnerability incorporated in PHP in 2012. CVE-2024-4577 impacts PHP simplest when it’s working in a procedure referred to as CGI, wherein a internet server splits HTTP requests and passes them via. them to the PHP script to mend it. Even supposing PHP isn’t set to CGI mode, the vulnerability can nonetheless be used if PHP executables akin to php.exe and php-cgi.exe are within the information accessed by way of the internet server. This configuration could be very uncommon, except for for the XAMPP platform, which makes use of it by way of default. Any other requirement seems to be that Home windows – which is used to localize the OS – will have to be set to Chinese language or Eastern. Commercial A significant vulnerability was once revealed on June 6, at the side of a safety patch. Inside of 24 hours, attackers have been exploiting its vulnerability to put in TellYouThePass, researchers at safety company Imperva stated Monday. The code used used the mshta.exe Home windows binary to execute an HTML report saved on a server managed by way of the attackers. Using this technique demonstrates a method referred to as layering, the place attackers use OS methods and take a look at equipment to imitate customary, non-malicious situations. In a file revealed on Friday, Censys researchers stated that the hacking of the TellYouThePass crew began on June 7 and confirmed earlier job that randomly scans the Web for susceptible units by way of following the risk profile and pointing to any server that may be discovered. Most of the inflamed servers have IP addresses assigned to China, Taiwan, Hong Kong, or Japan, perhaps as a result of China and Japan are the one areas showed to be susceptible, Censys researchers stated in an e mail. Since then, the choice of inflamed websites – that have been recognized by way of taking a look on the HTTP reaction of the general public to an open crew appearing the server's information, in addition to a listing of recognized ransom information – has dropped from 670 in June. 8 to best 1,800 on Monday.
Extend / Subsequent Redemption.Censys Vulnerability, which is tracked as CVE-2024-4577 and has a ranking of 9.8 out of 10, comes from mistakes in the way in which PHP converts Unicode characters into ASCII. A function in Home windows referred to as Highest Have compatibility permits attackers to make use of a method referred to as argument injection to transform person enter into characters that factor malicious instructions to the primary PHP program. The exploit permits attackers to avoid CVE-2012-1823, a crucial vulnerability incorporated in PHP in 2012. CVE-2024-4577 impacts PHP simplest when it’s working in a procedure referred to as CGI, wherein a internet server splits HTTP requests and passes them via. them to the PHP script to mend it. Even supposing PHP isn’t set to CGI mode, the vulnerability can nonetheless be used if PHP executables akin to php.exe and php-cgi.exe are within the information accessed by way of the internet server. This configuration could be very uncommon, except for for the XAMPP platform, which makes use of it by way of default. Any other requirement seems to be that Home windows – which is used to localize the OS – will have to be set to Chinese language or Eastern. Commercial A significant vulnerability was once revealed on June 6, at the side of a safety patch. Inside of 24 hours, attackers have been exploiting its vulnerability to put in TellYouThePass, researchers at safety company Imperva stated Monday. The code used used the mshta.exe Home windows binary to execute an HTML report saved on a server managed by way of the attackers. Using this technique demonstrates a method referred to as layering, the place attackers use OS methods and take a look at equipment to imitate customary, non-malicious situations. In a file revealed on Friday, Censys researchers stated that the hacking of the TellYouThePass crew began on June 7 and confirmed earlier job that randomly scans the Web for susceptible units by way of following the risk profile and pointing to any server that may be discovered. Most of the inflamed servers have IP addresses assigned to China, Taiwan, Hong Kong, or Japan, perhaps as a result of China and Japan are the one areas showed to be susceptible, Censys researchers stated in an e mail. Since then, the choice of inflamed websites – that have been recognized by way of taking a look on the HTTP reaction of the general public to an open crew appearing the server's information, in addition to a listing of recognized ransom information – has dropped from 670 in June. 8 to best 1,800 on Monday.
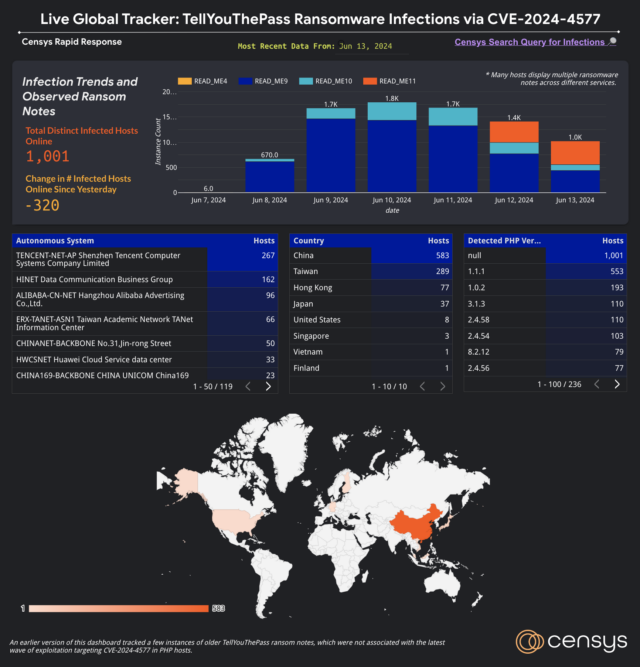 Upload/Hint day by day worrying pictures of PHP servers and geolocation.Censys Censys researchers stated in an e mail that they don't in point of fact know what's inflicting the numbers. “From our standpoint, lots of the affected other folks appear to be nonetheless on-line, however the port working the PHP-CGI or XAMPP provider stops responding – therefore the low choice of detected infections,” he wrote. “Any other level to imagine is that recently there is not any ransom fee to the one Bitcoin deal with within the ransom word (supply). In accordance with this, our opinion is that that is more than likely since the products and services had been terminated or got rid of from the Web by some means. ” XAMPP The researchers went on to mention that about part of the seen exploits display certain indicators of XAMPP, however this estimate could be low as a result of no longer all programs are uncovered to this system they use “I believe lots of the inflamed methods are working XAMPP,” the researchers stated. of the protection corporate Analygence, as a result of XAMPP directors obviously state that their tool isn’t appropriate for building. “Individuals who make a selection to make use of synthetic intelligence will have to take care of the effects of that call,” he wrote in an internet interview. Even though XAMPP is the one platform showed to be susceptible, other folks working PHP on any Home windows device must set up the replace once conceivable. The Imperva script related above supplies IP addresses, filenames, and filenames that directors can use to decide whether or not they’re beneath assault.
Upload/Hint day by day worrying pictures of PHP servers and geolocation.Censys Censys researchers stated in an e mail that they don't in point of fact know what's inflicting the numbers. “From our standpoint, lots of the affected other folks appear to be nonetheless on-line, however the port working the PHP-CGI or XAMPP provider stops responding – therefore the low choice of detected infections,” he wrote. “Any other level to imagine is that recently there is not any ransom fee to the one Bitcoin deal with within the ransom word (supply). In accordance with this, our opinion is that that is more than likely since the products and services had been terminated or got rid of from the Web by some means. ” XAMPP The researchers went on to mention that about part of the seen exploits display certain indicators of XAMPP, however this estimate could be low as a result of no longer all programs are uncovered to this system they use “I believe lots of the inflamed methods are working XAMPP,” the researchers stated. of the protection corporate Analygence, as a result of XAMPP directors obviously state that their tool isn’t appropriate for building. “Individuals who make a selection to make use of synthetic intelligence will have to take care of the effects of that call,” he wrote in an internet interview. Even though XAMPP is the one platform showed to be susceptible, other folks working PHP on any Home windows device must set up the replace once conceivable. The Imperva script related above supplies IP addresses, filenames, and filenames that directors can use to decide whether or not they’re beneath assault.