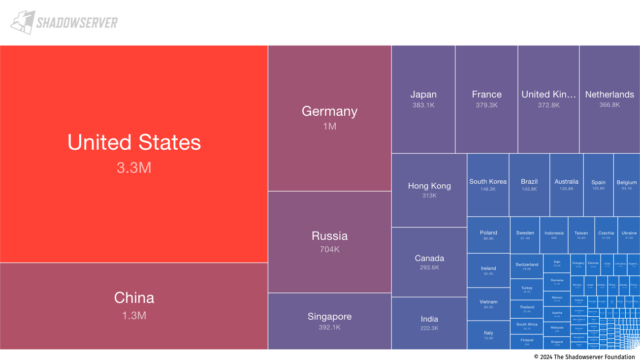
Getty Photographs About 11 million Web servers stay at risk of a just lately found out vulnerability that permits attackers to compromise within the affected networks. As soon as in, attackers compromise the integrity of SSH classes that shape the lynchpin for directors to soundly keep up a correspondence with computer systems within the cloud and different important environments. Terrapin, because the danger has been known as, used to be recognized two weeks in the past in a analysis paper revealed by means of instructional researchers. Coded as CVE-2023-48795, the assault evolved by means of the researchers works when the attackers have an enemy-in-the-middle (additionally abbreviated as AitM and often referred to as man-in-the-middle or MitM), corresponding to after they' also are put in at the similar community and it could actually encrypt messages and bet the id of the recipient and the sender. In such circumstances, Terrapin permits the attackers to switch or corrupt the tips transmitted within the SSH knowledge move all over the handshake – the preliminary segment of the verbal exchange, when the 2 events speak about what they’ll use to determine a safe connection. As such, Terrapin represents the primary encryption assault that objectives the integrity of the SSH protocol itself. It really works by means of having a look at BPP (Binary Packet Protocol), which is designed to make sure that AitMs can not upload or drop changed messages all over the handshake. This authentic assault works if the set up helps “ChaCha20-Poly1305” or “CBC with Encrypt-then-MAC,” cipher varieties, which, on the time the paper used to be revealed, had been present in 77 p.c of SSH servers. A community research performed on Tuesday, the final day knowledge used to be to be had on the time of reporting, confirmed that greater than 11 million IP addresses pointing to the SSH server stay at risk of Terrapin. A couple of 3rd of those addresses, 3.3 million, are positioned in the United States, adopted by means of China, Russia, Germany, Russia and Singapore. The entire unmodified Shadowserver tracks supported the desired cipher varieties. Promoting
 Enlarge/Inventive for CVE-2023-48795.
Enlarge/Inventive for CVE-2023-48795.
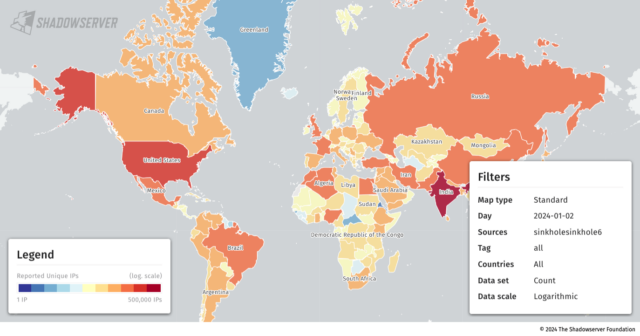 Enlarge / World map of nations now not deployed in opposition to CVE-2023-48795.Shadowserver Most effective 53 of the vulnerabilities depended at the implementation of AsyncSSH, the one program identified to be critically suffering from Terrapin. The 2 vulnerabilities that the researchers present in AsyncSSH allowed Terrapin to (1) obtain safety improvements in order that organizations can exchange the extra message despatched by means of the server, permitting the attacker to regulate the content material or (2) regulate the tip of the SSH shopper consultation both. injecting or extracting packets or copying a collection shell. AsyncSSH launched two vulnerabilities, indexed as CVE-2023-46445 and CVE-2023-46446, together with CVE-2023-48795, a Terrapin vulnerability affecting the SSH protocol. It kind of feels that many of the AsyncSSH customers have patched it. The significance of AitM's location and the loss of recently identified threats to Terrapin are essential mitigating components that some critics say were misplaced in different tales. That mentioned, at this level, there's little reason why to seek out protocol insects at this level, since patches turned into to be had a couple of week or two in the past. “This assault calls for a large number of complexity as a result of MitM is essential, in order that it reduces using the gear we would like,” Piotr Kijewski, a researcher at Shadowserer, wrote in an e-mail to Ars. “It’s not going that many of us will use this. Alternatively, the selection of folks in danger presentations that this vulnerability will likely be with us for future years and that during itself makes it horny from time to time.” complicated assaults, corresponding to the ones supported by means of international locations. Even if earlier variations of AsyncSSH had been the one identified approach at risk of Terrapin assaults, the researchers had little time to research the others. Attackers with extra time, sources, and motivation can determine different prone methods. Kijewski indexed the highest 50 indicators displayed by means of prone IP addresses as: serverid_software rely openssh_7.4 2878009 openssh_7.6p1 956296 openssh_8.2p1 802582 openssh_8.0 758138 openssh_41457p openssh_41457p _8.9p 1 460595 openssh_7.2p2 391769 openssh_7.4p1 320805 openssh_8.5 316462 openssh_9.3 298626 openssh_8.7 219381 openssh_6.7p1 156758 openssh_9.2p1 141010 openssh_6.6.1p1 openssh_1364. 05423 dropbear_2020.80 93154 openssh_8.8 88284 openssh_7.5 76034 aws_sftp_1.1 75157 openssh_9.0p1 70305 openssh_8.2 59887 openssh_7.9 59301 dropbear 51374 openssh 35408 openssh _7.2 34494 openssh_7.8 33955 dropbear_2020_2020_519. 6748 openssh_8.1 23188 lancom 22267 openssh_6.4 18483 openssh_8.4 18158 openssh_8.9 17310 openssh_7.6 17235 openssh_for_windows_8.1 17150 openssh_for_windows_7.7 15603 openssh_8.6 1401 8 openssh_6.9 13601 openssh_80202be602 drops8. 22.83 12036 openssh_7.7 11645 openssh_for_windows_8.0 11089 openssh_7.3 10083 mod_sftp 9937 openssh_8.3p1 9163 cisco-1.25 8301 Kuyika Terrapin sizowongoka, chifukwa cha kuchuluka kwa zomwe zachitika zomwe zakhudzidwa komanso kufunikira koti mapulogalamu omwe akugwira ntchito pa kasitomala onse ndi seva azilumikizidwa. The researchers indexed the next vulnerabilities and incorporated hyperlinks to patches when to be had. Asterisks point out builders that had been contacted previous to the discharge of the analysis paper: Implementation Affected Variations Patched Model(s) AsyncSSH* 2.14.1 and previous 2.14.2 Bitvise SSH* 9.31 and previous 9.33 ConnectBot* 1.9.9 and previous 1.9.10 CrushFTPFTP 10.5.6 and previous 10.6.0 CycloneSSH* 2.3.2 and previous 2.3.4 Dropbear* 2022.83 and previous Unencumber Erlang/OTP SSH* OTP 26.2 and previous
Enlarge / World map of nations now not deployed in opposition to CVE-2023-48795.Shadowserver Most effective 53 of the vulnerabilities depended at the implementation of AsyncSSH, the one program identified to be critically suffering from Terrapin. The 2 vulnerabilities that the researchers present in AsyncSSH allowed Terrapin to (1) obtain safety improvements in order that organizations can exchange the extra message despatched by means of the server, permitting the attacker to regulate the content material or (2) regulate the tip of the SSH shopper consultation both. injecting or extracting packets or copying a collection shell. AsyncSSH launched two vulnerabilities, indexed as CVE-2023-46445 and CVE-2023-46446, together with CVE-2023-48795, a Terrapin vulnerability affecting the SSH protocol. It kind of feels that many of the AsyncSSH customers have patched it. The significance of AitM's location and the loss of recently identified threats to Terrapin are essential mitigating components that some critics say were misplaced in different tales. That mentioned, at this level, there's little reason why to seek out protocol insects at this level, since patches turned into to be had a couple of week or two in the past. “This assault calls for a large number of complexity as a result of MitM is essential, in order that it reduces using the gear we would like,” Piotr Kijewski, a researcher at Shadowserer, wrote in an e-mail to Ars. “It’s not going that many of us will use this. Alternatively, the selection of folks in danger presentations that this vulnerability will likely be with us for future years and that during itself makes it horny from time to time.” complicated assaults, corresponding to the ones supported by means of international locations. Even if earlier variations of AsyncSSH had been the one identified approach at risk of Terrapin assaults, the researchers had little time to research the others. Attackers with extra time, sources, and motivation can determine different prone methods. Kijewski indexed the highest 50 indicators displayed by means of prone IP addresses as: serverid_software rely openssh_7.4 2878009 openssh_7.6p1 956296 openssh_8.2p1 802582 openssh_8.0 758138 openssh_41457p openssh_41457p _8.9p 1 460595 openssh_7.2p2 391769 openssh_7.4p1 320805 openssh_8.5 316462 openssh_9.3 298626 openssh_8.7 219381 openssh_6.7p1 156758 openssh_9.2p1 141010 openssh_6.6.1p1 openssh_1364. 05423 dropbear_2020.80 93154 openssh_8.8 88284 openssh_7.5 76034 aws_sftp_1.1 75157 openssh_9.0p1 70305 openssh_8.2 59887 openssh_7.9 59301 dropbear 51374 openssh 35408 openssh _7.2 34494 openssh_7.8 33955 dropbear_2020_2020_519. 6748 openssh_8.1 23188 lancom 22267 openssh_6.4 18483 openssh_8.4 18158 openssh_8.9 17310 openssh_7.6 17235 openssh_for_windows_8.1 17150 openssh_for_windows_7.7 15603 openssh_8.6 1401 8 openssh_6.9 13601 openssh_80202be602 drops8. 22.83 12036 openssh_7.7 11645 openssh_for_windows_8.0 11089 openssh_7.3 10083 mod_sftp 9937 openssh_8.3p1 9163 cisco-1.25 8301 Kuyika Terrapin sizowongoka, chifukwa cha kuchuluka kwa zomwe zachitika zomwe zakhudzidwa komanso kufunikira koti mapulogalamu omwe akugwira ntchito pa kasitomala onse ndi seva azilumikizidwa. The researchers indexed the next vulnerabilities and incorporated hyperlinks to patches when to be had. Asterisks point out builders that had been contacted previous to the discharge of the analysis paper: Implementation Affected Variations Patched Model(s) AsyncSSH* 2.14.1 and previous 2.14.2 Bitvise SSH* 9.31 and previous 9.33 ConnectBot* 1.9.9 and previous 1.9.10 CrushFTPFTP 10.5.6 and previous 10.6.0 CycloneSSH* 2.3.2 and previous 2.3.4 Dropbear* 2022.83 and previous Unencumber Erlang/OTP SSH* OTP 26.2 and previous
OTP 25.3.2.7 is older
OTP 24.3.4.14 is the unique OTP 26.2.1
OTP 25.3.2.8
OTP 24.3.4.15 FileZilla Shopper 3.66.1 and previous 3.66.4 Golang x/crypto/ssh* 0.16.0 and previous 0.17.0 JSch (Fork)* 0.2.14 and previous 0.2.15 libssh* 0.10.5 and previous
0.9.7 is already 0.10.6
0.9.8 libssh2* 1.11.0 and previous Unencumber Maverick Legacy* 1.7.55 and previous 1.7.56 Maverick Synergy* 3.0.21 and previous (Hotfix)
3.0.10 and previous (OSS) 3.0.22
3.1.0-SNAPSHOT MobaXterm 23.5 and previous 23.6 Nova 11.7 and previous 11.8 OpenSSH* 9.5 / 9.5p1 and previous 9.6 / 9.6p1 Paramiko* 3.3.1 and previous 3.4.0 phpseclib 34 and previous.
2.0.45 and previous
1.0.21 is already 3.0.35
2.0.46
1.0.22 PKIX-SSH* 14.3 and previous 14.4 ProFTPD* 1.3.8a and previous 1.3.8b PuTTY* 0.79 and previous 0.80 Russh* 0.40.1 and previous 0.40.2 SecureCRT* 9.4.4.3 34.9 SF Gate and 34 SF Gate. .5 and previous 3.4.6 SFTPGo 2.5.5 and previous
2.4.5 and previous 2.5.6
2.4.6 ssh2* 1.14.0 and previous 1.15.0 sshj* 0.37.0 and previous 0.38.0 Tera Time period* 5.0 and previous
4.107 is already 5.1
4.108 Thrussh* 0.34.0 and previous 0.35.1 TinySSH 20230101 and previous 20240101 Transport 5.10.3 and previous 5.10.4 Win32-OpenSSH* 9.4.0.0p1-Beta CP1.6.0. beta XShell 7* Construct 0142 is already Construct 0144 As discussed previous, there is not any want for alarm. Terrapin isn’t Citrix Bleed , CVE-2022-47966, MoveIT, CVE-2021-22986, or CVE-2023-49103, or CVE-2021-22986, which have been some of the maximum exploited vulnerabilities in 2023 for tens of millions of servers. So far, there are not any identified studies of Terrapin patches inflicting uncomfortable side effects. Admins would do neatly to patch quickly.